Changes in Sinkhole and Honeypot Report Types and Formats
April 1, 2021
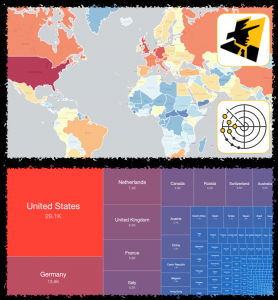
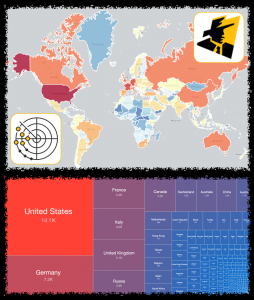
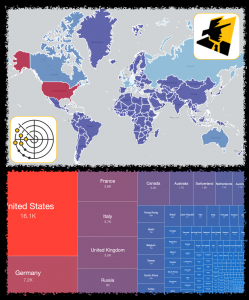
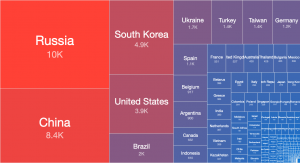
Over the years, Shadowserver’s report list has grown considerably from when we originally started. When some of these reports were originally set up, the requirements were different to those needed today. We have therefore decided to implement changes with some of the existing report types, especially those related to our sinkholes and honeypots, as well as remove some legacy reports. Changes will come into effect on 2021-06-01. On that day, the old reports will cease and only the new equivalents will be sent out. Until that time, starting 2021-04-05 both the old reports and new reports will function in parallel.