Technical Summary of Observed Citrix CVE-2023-3519 Incidents
August 7, 2023
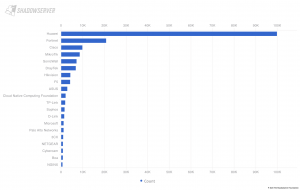
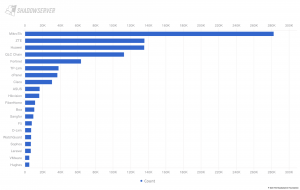
The Shadowserver Foundation and trusted partners have observed three different malicious campaigns that have exploited CVE-2023-3519, a code injection vulnerability rated CVSS 9.8 critical in Citrix NetScaler ADC and NetScaler Gateway. The summary below is based on collaboration with the individual compromised organizations, as well as their commercial incident response teams. All timestamps in this write-up are in UTC timezone, and they have all been slightly adjusted to not disclose the actual times. If you own a Citrix NetScaler or have those in your constituency, please follow the detection and hunting advice for signs of compromise and webshells!