Shadowserver 2024: Highlights of the Year in Review
February 17, 2025
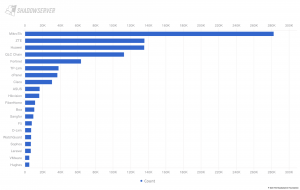
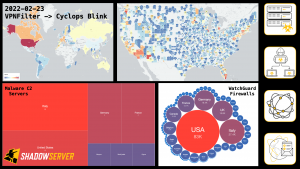
A review of Shadowserver’s 20th year as the world’s largest provider of free, timely, actionable, daily cyber threat intelligence. Covering the latest improvements in our public benefit services, responses to emerging cyber threats, and detection and reporting of the latest vulnerabilities to National CSIRTs and system defenders globally. We provide highlights of our cybersecurity capacity building efforts, plus successful outcomes from our free support to Law Enforcement in major cybercrime disruption operations.