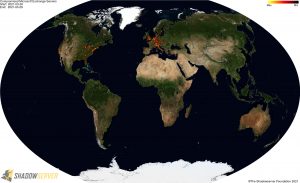
Updated 2021-03-31: In response to questions about post-exploitation webshells potentially still being present on patched Microsoft Exchange servers, we have re-run our compromised/vulnerable Microsoft Exchange Server Special Report, covering retesting performed during the period 2021-03-26 to 2021-03-31 for all known webshell paths so far – including on Exchange servers that may originally have reported to test vulnerable or compromised, but have since tested as having been patched and no longer vulnerable. This Special Report contains 510,632 events, made up of 253,839 unique webshell URLs on 400 different common paths, hosted across 34,647 IP addresses and 40,512 hostnames, located in 5008 ASNs and 205 countries. Please make sure that any detected webshells are urgently remediated on all servers that remain un-patched, and that any already patched but potentially still compromised servers are also quickly remediated too.
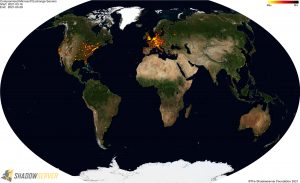
Updated 2021-03-29: Compromised/vulnerable Microsoft Exchange Server Special Report re-run, containing 143,728 events for 75,806 unique live webshell URLs detected across 14,352 IPs & 16,877 hostnames, such as in Brian Kreb’s story of how attackers associated their post-compromise activity to his name. This represents the remaining still live subset from 282,905 unique webshell URLs that were detected across 86,855 IPs & 102,101 hostnames during past 2 weeks (on servers that were since patched and hopefully cleaned up). We are currently waiting for one-off re-test for webshells on patched servers to complete, which unfortunately seems likely add another 5-6000 still live webshells.
(click to enlarge heatmaps)
Over the past 12 days we have published 5 one-off Special Reports that provided information about the recently patched recently patched zero-day vulnerabilities in Microsoft Exchange Server (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065). You can read our blog posts covering the previous installments here:
- HAFNIUM attributed Exchange victims (2021-02-26 to 2021-03-03, pre-patch release)
- Exchange Scanning #1 – mass exploitation (2021-03-09, post-patch release)
- Exchange Scanning #2 – confirmed web shells (2021-03-12, post-patch release)
- Exchange Scanning #3 – potentially vulnerable servers (2021-03-13 to 2021-03-14, post-patch release)
- Exchange Scanning #4 – scanning for vulnerable compared with some DNS based detection (2021-03-14, post-patch release)
Early exploitation of these zero-day Microsoft Exchange Server vulnerabilities was initially attributed to the so-called HAFNIUM nation state threat actor group, but with exploits rapidly becoming available publicly, they allowed un-patched Microsoft Exchange servers to be exploited by a wide range of potential actors – which has also added major complexity to ongoing incident response efforts.
We have already shared remediation data with our constituents that was provided by public spirited entities and companies such as DIVD and KryptosLogic, plus additional data sets that were generated internally by Shadowserver.
This latest Special Report represents our most comprehensive effort yet to enumerate as many vulnerable and compromised Microsoft Exchange Servers as possible. Much of the detection of potentially vulnerable Microsoft Exchange servers performed to date has been based on internet-wide scanning of all ~4 billion IPv4 addresses (IPv4 /0 scanning), which is effective at identifying Exchange/OWA environments which are configured to use the default IP address. However, this kind of mass scanning will not always identify potentially vulnerable Microsoft Exchange servers, since they can also be configured to use web server virtual hosting on fully qualified domain names (FQDNs), rather than simply binding to the default web site instance or a server’s main IP address. In such cases, it is possible that virtual host-based Microsoft Exchange Server instances may be missed during IPv4 /0 scans.
This sixth Special Report contains a hybrid data set generated during the period 2021-03-16 to 2021-03-23, employing both scanning and FQDN host name based testing (using data such as that obtained through analysis of MX records, reverse DNS, passive DNS, SSL certificate issuer/subject common names, etc) to attempt to identify additional potentially vulnerable or compromised Microsoft Exchange servers.
In this report:
- Devices with a status of “vulnerable-at-time-of-scan” were observed to behave as being vulnerable to the ProxyLogon CVE-2021-26855 Exchange SSRF test via X-AnonResource-Backend and X-BEResource cookies, as per Microsoft’s published Nmap NSE script.
- Devices with a status of “compromised” were observed to return the expected response from a web shell present on easily guessable URI paths that are known to be dropped onto successfully compromised Microsoft Exchange servers. Where possible, the Exchange Version information (obtained from the web shell’s “AdminDisplayVersion” field, such as “Version 15.0 (Build 1395.4)” and “ExchangeVersion” field, such as “0.10 (14.0.100.0)“) plus the internal server host name are included in the later scans, to aid victim identification and remediation.
Some of the potentially vulnerable or compromised Microsoft Exchange servers will be running as a virtual host on an IP address that is also configured to respond as the default site for that IP address, independently from web server virtual hosting, so there will be some duplication across unique vulnerable and compromised Microsoft Exchange Server URL paths (ie FQDN exchange.foo.com is also mail.foo.com, which is also IP address 1.2.3.4 which also has reverse DNS ip4-3-2-1.region.someisp.com).
Since the data set covers the period 2021-03-16 to 2021-03-23, it is possible that some Microsoft Exchange servers may have already been patched and detected web shells removed. However, we are providing the full data set for each network/country to our report recipients for that full period, so that they can make their own informed assessment of their own potential exposure risks against their own remediation practices.
This new Special Report is being shared outside of our normal free daily network reporting process with 120 National CSIRTs in 148 countries and over 5900 network owners or maximum public benefit. Due to the high risk that many systems have already been compromised at least once, we strongly encourage network owners and National CERT/CSIRTs to urgently remediate and patch/rebuild all impacted victim systems immediately.
You can find more detail on the format of the new Special Report here.
Data Analysis
In total this Special Report contains:
- 1,048,810 events globally for the period 2021-03-16 to 2021-03-23, which correspond to 86,138 unique IP addresses and 101,045 distinct hostnames that were identified at the time of the scanning to be vulnerable Microsoft Exchange Servers
- 79,352 unique web shell URLs on compromised Microsoft Exchange Servers (after excluding honeypots, which each respond on many possible common web shell paths and artificially inflate web shell counts). Of which, 46,166 web shells still returned valid Exchange Version information in the most recent 2021-03-23 scans
- The data came from a total data set of 1,619,498 events, which include 321,139 unique web shell paths that were identified before honeypot web shell paths were excluded
For the day (2021-03-16) with the highest individual event count (which had an overlap between this report and the previous report), that corresponded to 117,198 unique IP addresses in 10617 different Autonomous System Numbers (ASNs), which geo-located to 222 different countries.
It is worth noting that patching these Microsoft Exchange Server vulnerabilities may prevent further compromise, but damage could well still have been done during the past weeks of mass exploitation. In some cases, web-shells that allow subsequent remote access or other malware may still be present on servers that have been successfully patched. On many compromised Microsoft Exchange Servers we routinely observe two, three or more different web shells being present – quite possibly deployed by different threat actors at different times, which even taking into account potential false positives from honeypots, makes for a depressing dataset.
Remediation
Remediation advice for Microsoft Exchange Server operators has been provided by CISA. Microsoft have released tools for checking Exchange servers for evidence of exploitation, including a one-click remediation tool. You can also use the online CheckMyOWA resource to check if your Exchange Server has appeared in their historical data.
If you have missed this Special Report because you were not yet a subscriber to our free daily network reports, do not worry: simply subscribe for your network or country now and specifically request all recent Shadowserver Special Reports. We will resend the Special Report specifically for your network or country (for National CERT/CSIRTs).
If you have a data set which you feel could also be of benefit to National CERT/CSIRTs and network owners world-wide to help protect victims of cybercrime, please get in touch and discuss the options for using Shadowserver’s proven reporting systems for distribution and remediation.
We hope that the new Shadowserver Special Reports will be a useful additional free tool in helping network defenders identify victims and better protect their networks and the entire Internet. Please contact us if you have any questions.