Last week we enabled a new IPv4 Internet-wide scan for accessible Microsoft RDPEUDP services on port 3389/UDP. This UDP service is an extension to the classic Microsoft Remote Desktop Protocol service (RDP) over TCP on port 3389.
We scan by sending a 16 byte RDP UDP connection request to port 3389/UDP. Our scan results in around 12 000 unique IPv4 addresses on a given day responding. We report our findings daily in a new Accessible MS-RDPEUDP report as part of our free daily remediation feeds.
RDP as a remote access service has long had a number of security risks associated with it, which includes weak credentials being brute-forced by attackers to gain remote access as well as past vulnerabilities such as Bluekeep (CVE-2019-0708) that allow for remote code execution by unauthenticated attackers.
The number of exposed RDP-UDP services is much lower than for RDP-TCP which currently has over 3.5M distinct IPs responding daily.
However, as a UDP service, the RDP-UDP extension can in addition be abused to perform reflected amplification DDoS attacks. A response to a RDP-UDP connection request with a spoofed IP source address is amplified around 28 times, with the protocol allowing for 3 such responses, for a total amplification factor of over 84 times.
As of January 2021, exposed MS-RDPEUDP services are being actively abused for amplification DDoS attacks.
The country breakdown of accessible RDPEUDP services that responded to our request probe on the 20th of January 2021 (around 12 000 IPv4 addresses) is shown below. As can be seen, nearly a half of all exposed services are found in the United States and China.
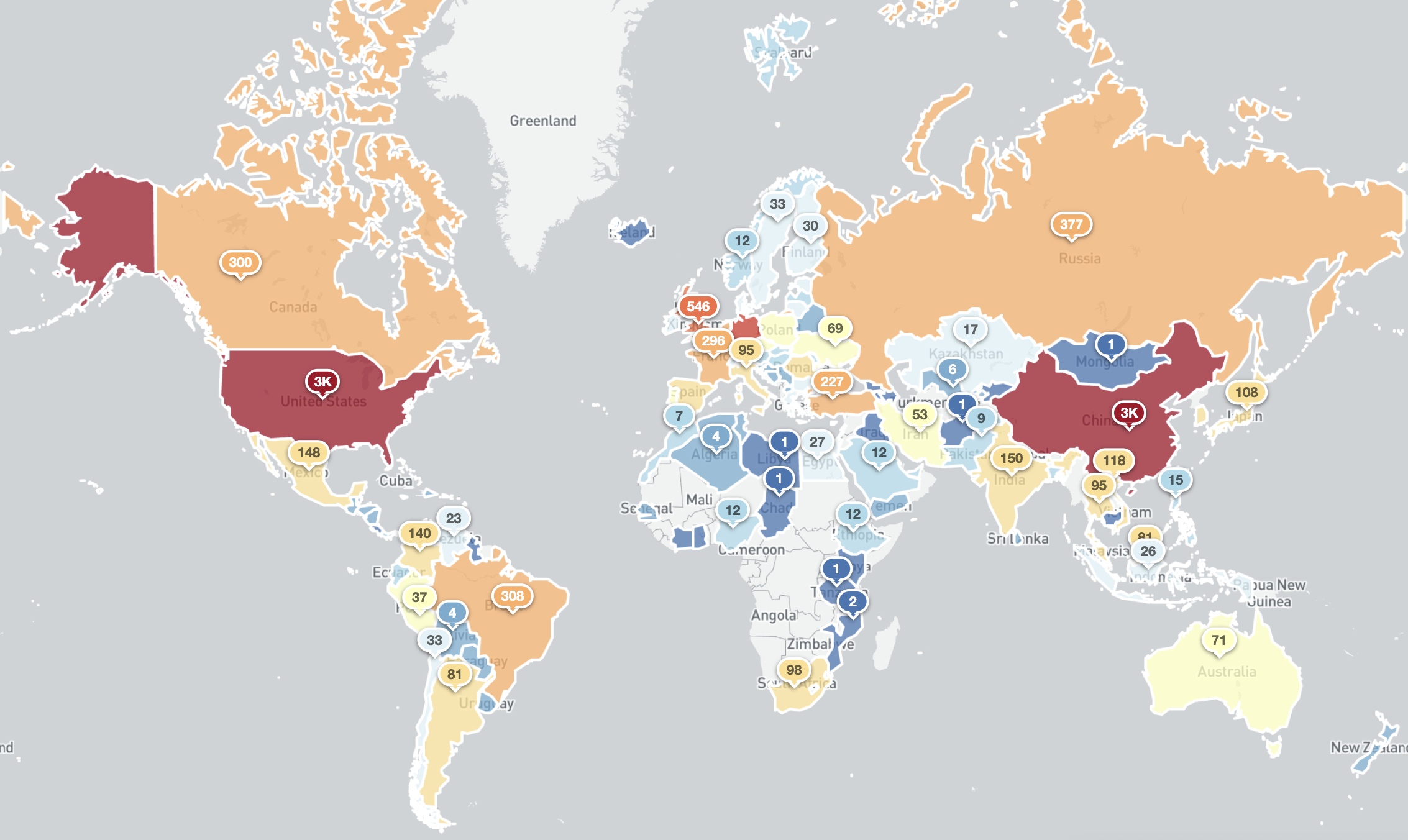
Exposed MS RDPEUDP services (port 3389/UDP) around the world (20th January 2021)
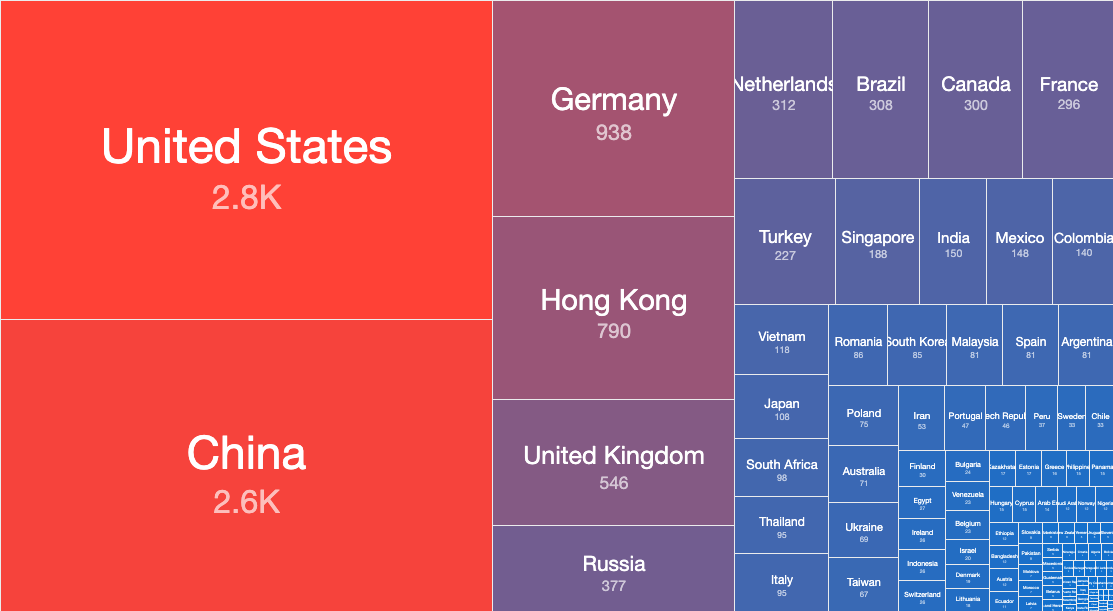
Top Countries with exposed MS-RDPEUDP services (20th January 2021)
Details about the format of the new report being shared can be found in the new Accessible MS-RDPEUDP Report page. All existing Shadowserver report subscribers are now automatically receiving the Accessible MS-RDPEUDP Report if any exposed MS-RDPEUDP services are identified within their networks and countries (for national CSIRTs).
To avoid being abused for reflected DDoS attacks, network owners should revert to RDP-TCP services unless UDP support is explicitly required. As suggested in the detailed research here, it is also possible to select a RDP-UDP-L Mode (“Best-Efforts”) for the service instead of the default RDP-UDP-R Mode (“Reliable”), which stops the protocol from re-transmitting packets, and hence lowers the amplification factor.
Network owners exposing RDP services should consider if exposing them to the wider Internet is absolutely necessary and firewall where possible or protect these services behind VPNs. RDP services should use 2FA mechanisms for authentication. Further security considerations can be found here.
For additional insight into the complexities of the RDP protocol, check out this blog on analyzing encrypted RDP connections.
If you are not already a subscriber to Shadowserver’s public benefit daily network reports and would like to receive this new report and our other existing report types (covering not just other scan results, but also many observations from sinkholes, honeypots, darknets and sandboxes), then please sign up to our free daily public benefit network remediation feed service.

