Shadowserver Special Reports are a NEW type of free, one off report. They do not cover a specific time period. We will send out Special Reports whenever we are able to share one-time, high value datasets that we feel should be reported responsibly for maximum public benefit. Although the events included in these Special Reports will fall outside of our usual 24 hour daily reporting window, we believe that there would still be significant benefit to our constituents in receiving and hopefully acting on the retrospective data.
For this new special report – Vulnerable Exchange Servers Special Report – our second after the freshly published HAFNIUM report, we have partnered with the Dutch Institute for Vulnerability Disclosure (DIVD), to share data from their scans for the recently disclosed CVE-2021-26855, CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065 vulnerabilities in Microsoft Exchange that have been widely reported to be being actively targeted by multiple threat actor groups. Kudos to DIVD for being willing to share their data with victims globally for public benefit.
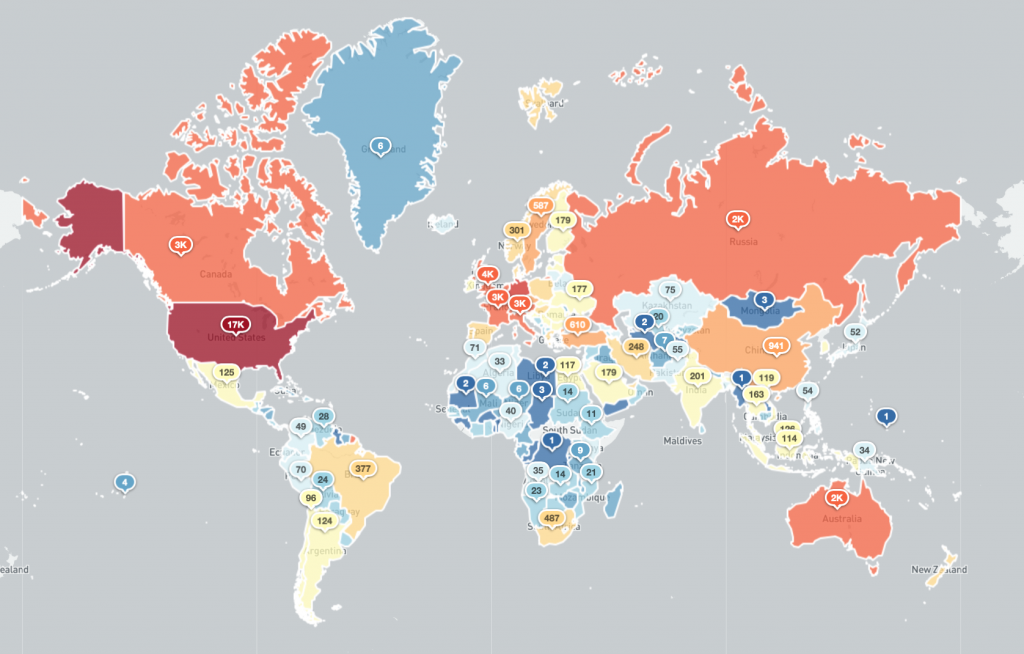
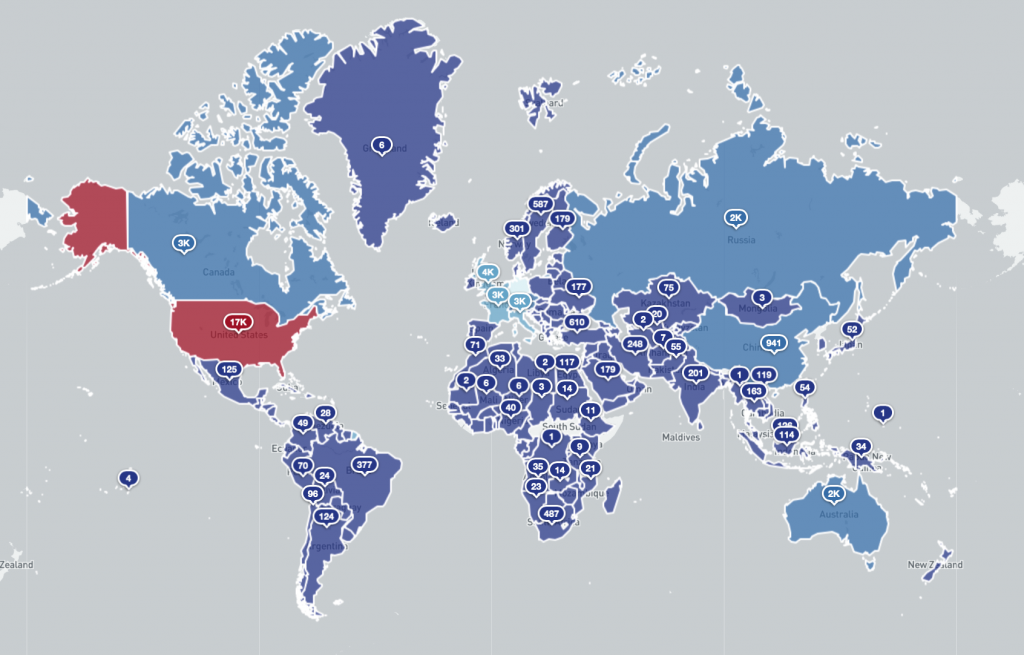
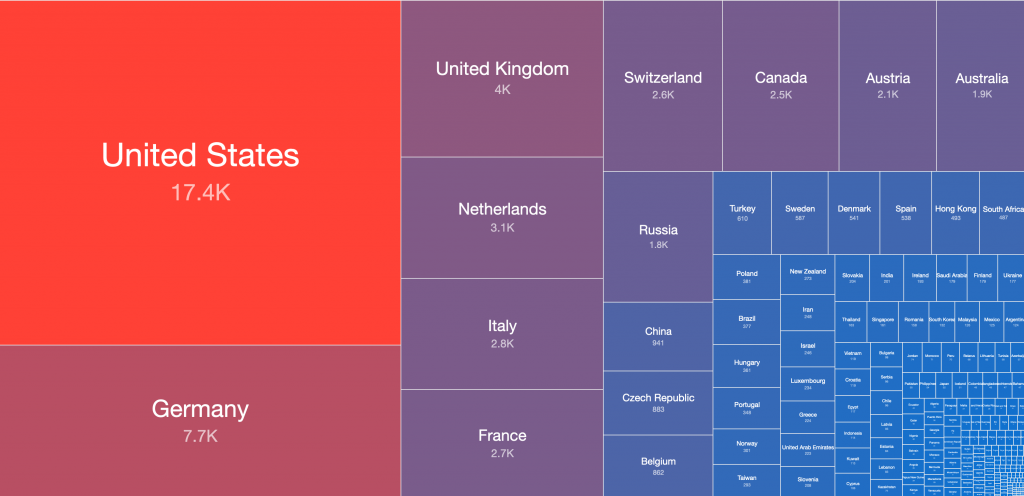
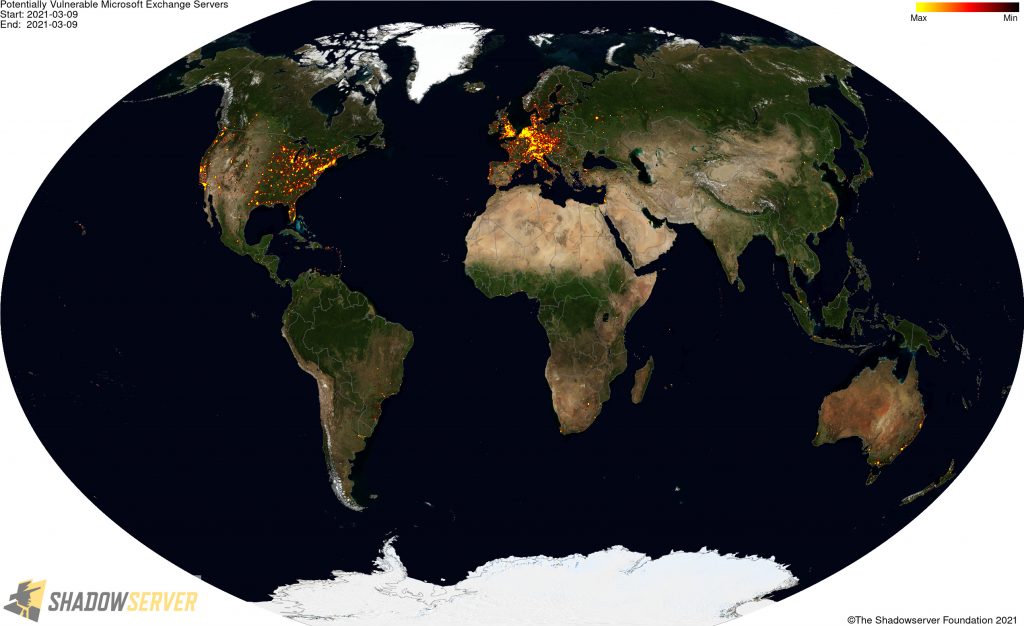
The total dataset distributed to 120 National CSIRTs in 148 countries and over 5900 network owners includes over 64088 unique IP addresses that were assessed on 2021-03-09 as potentially still having exposed Microsoft Exchange Server vulnerabilities (from a scanned population of 111989 unique IP addresses). As you can see from the images below, these risk Microsoft Exchange Servers are widely distributed geographically and many could potentially have already been compromised, putting many organizations world-wide at risk. We encourage network owners and National CERT/CSIRTs to patch and remediate quickly.
Data Visualization
Due to the high profile nature of these ongoing incidents, we know that there is considerable interest in the system demographics. So to help understand where potentially vulnerable Microsoft Exchange servers are located (based on IP-geolocated IP addresses), we provide the following visualizations (note: you can click each image for a high resolution version).
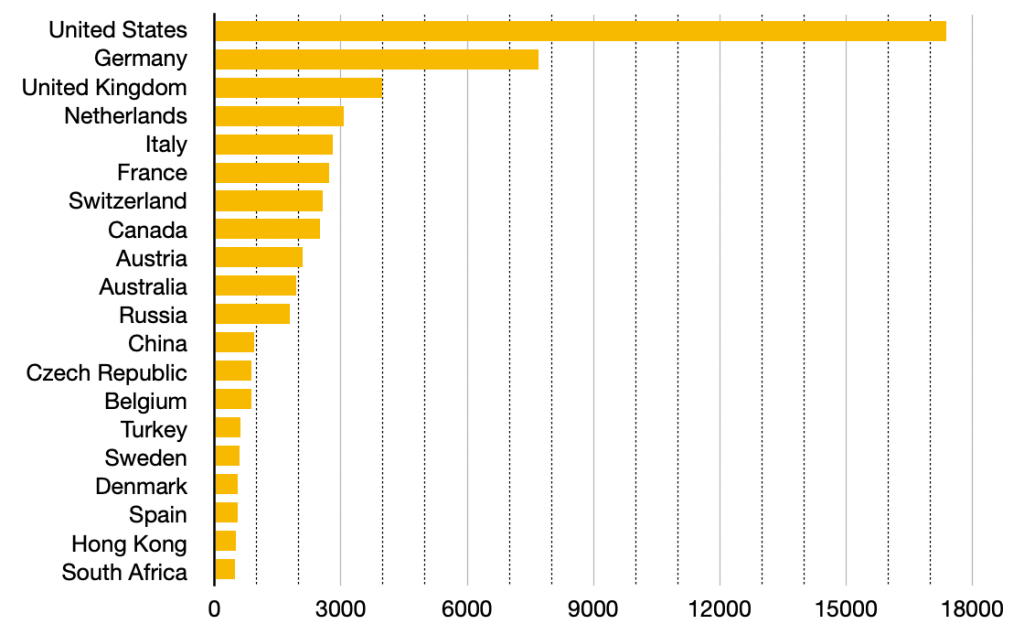
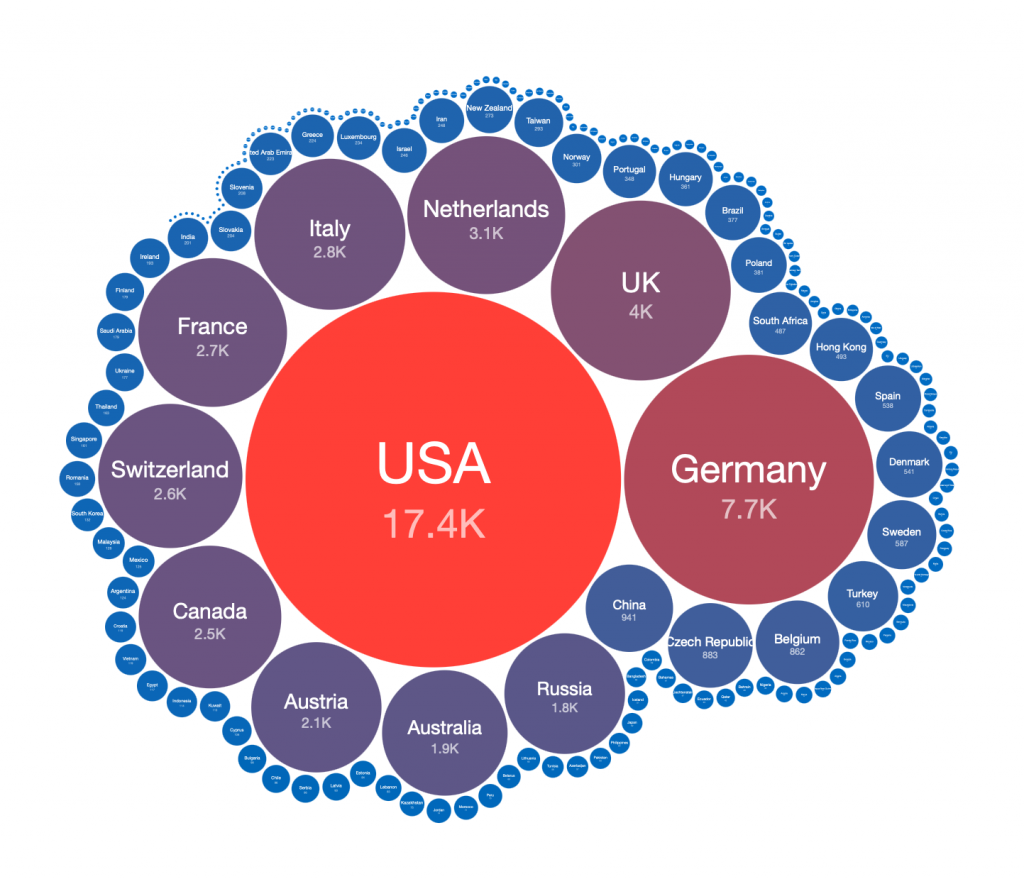
Potentially vulnerable Microsoft Exchange servers – top 20 countries 2021-03-09:
Relative population sizes of potentially vulnerable Microsoft Exchange Server versions 2021-03-09 (log scale, click for more detail):
Potentially vulnerable Microsoft Exchange servers by country 2021-03-09 (log scale):
Potentially vulnerable Microsoft Exchange servers by country 2021-03-09 (linear scale):
Potentially vulnerable Microsoft Exchange servers by country 2021-03-09 (treemap):
Potentially vulnerable Microsoft Exchange servers by country 2021-03-09 (bubblemap):
Potentially vulnerable Microsoft Exchange servers by country 2021-03-09 (interactive worldmap):
Perhaps not unsurprisingly, on 2021-03-09 the US had the largest number of potentially vulnerable Microsoft Exchange Servers per country. Although the two data sets are different (believed compromised by HAFNIUM Microsoft Exchange servers versus potentially vulnerable Microsoft Exchange Servers based on scan data and service fingerprints), we will drill down further into that region by comparing the US distribution detected on 2021-03-09 via IP scanning / Microsoft Exchange Server version fingerprinting against the compromised US data for 2021-02-26 from our previous HAFNIUM Special Report (ie pre vs post Microsoft Exchange patch release periods).
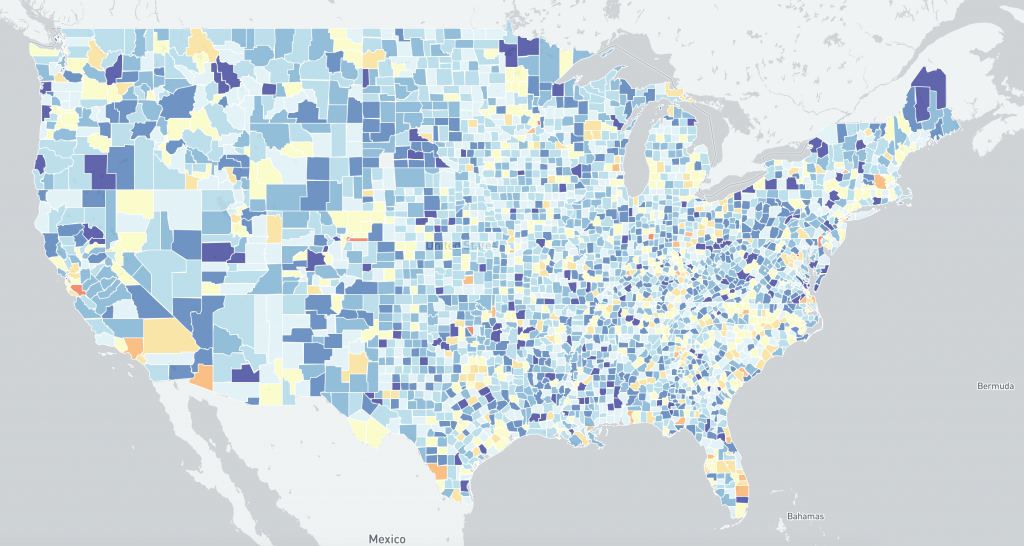
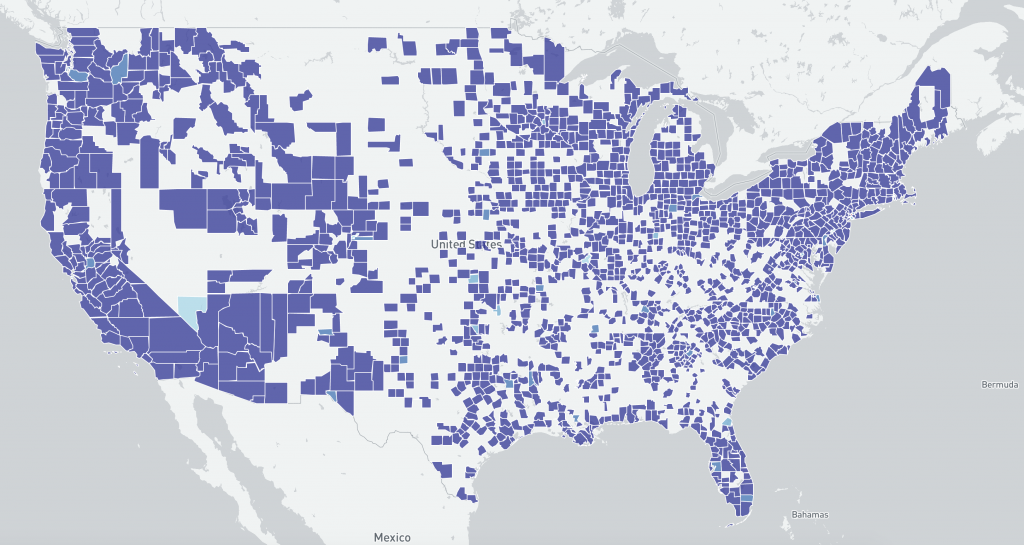
US distribution of IP-geolocated potentially vulnerable Microsoft Exchange Servers at a county level 2021-03-09 scan (log scale) :
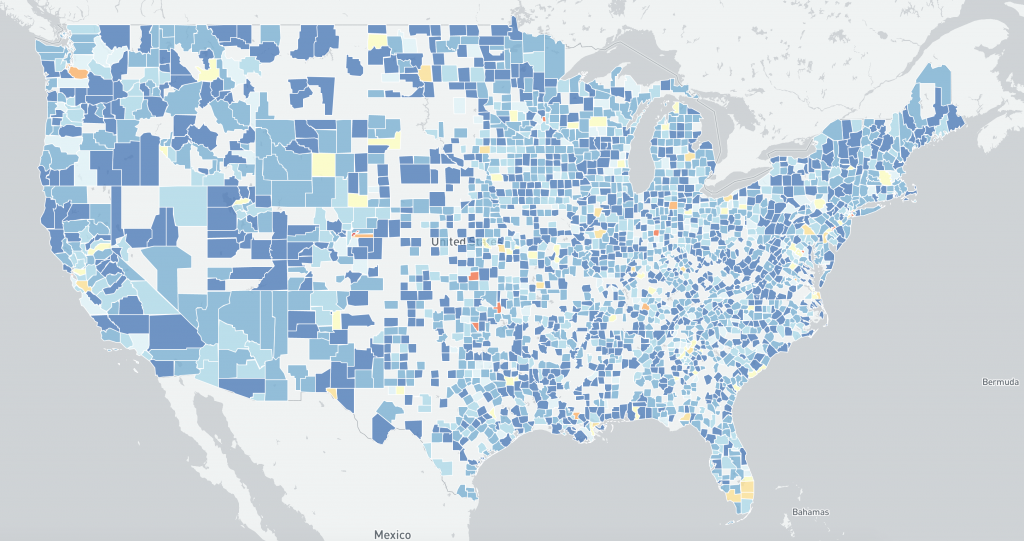
US distribution of IP-geolocated believed to be compromised by HAFNIUM Microsoft Exchange Servers at a county level 2021-02-26 (log scale) :
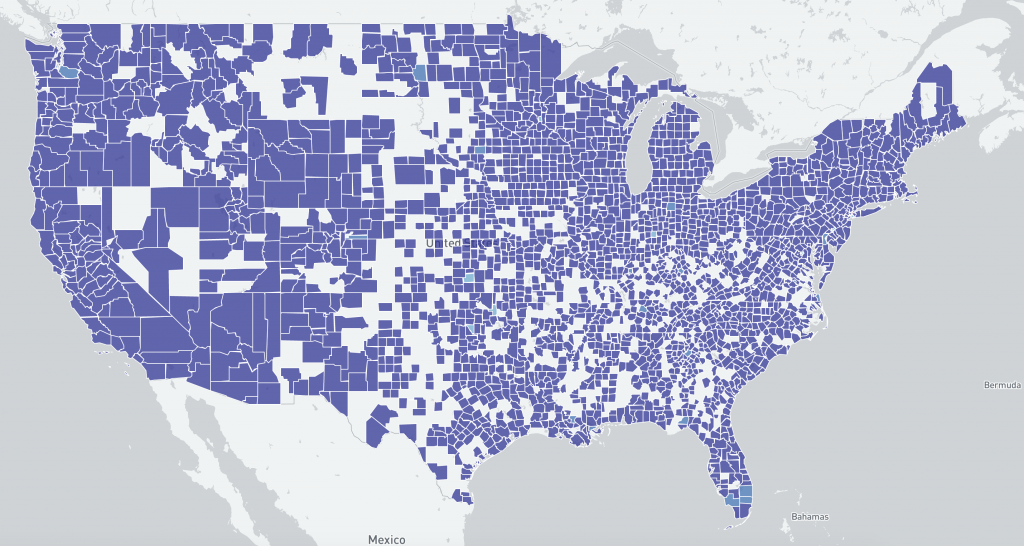
US distribution of IP-geolocated potentially vulnerable Microsoft Exchange Servers at a county level 2021-03-09 scan (linear scale):
US distribution of IP-geolocated believed to be compromised by HAFNIUM Microsoft Exchange Servers at a county level 2021-02-26 (linear scale) :
Although the two data sets are different (believed compromised vs potentially vulnerable based on scan data), the images may help understand changing US demographics between 2021-02-26 (pre-Microsoft Exchange Server patches) and 2021-03-09 (post Microsoft Exchange Server patches, with widespread mass exploitation reported).
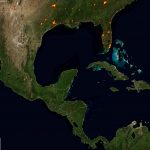
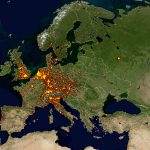
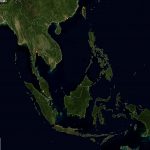
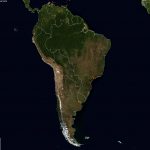
Global distribution of potentially vulnerable Microsoft Exchange Servers (heatmap):
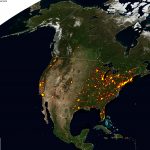
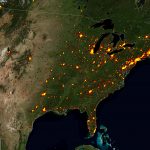
Global distribution of potentially vulnerable Microsoft Exchange Servers – regional zooms (click the heatmap image to view the larger high resolution versions):
We hope that these images help answer some of the initial questions people may have about this data, and encourage system owners who have not already patched to patch and remediate now. It is highly likely that these exploits will be used by a wider range of threat actors in the coming days, such as cybercriminals seeking new vectors for delivering ransomware to high value corporate target systems.
You can find more detail on the format of the new Special Report here.
Remediation advice for Microsoft Exchange Server operators has been provided by CISA. Microsoft have released tools for checking Exchange servers for evidence of exploitation. You can also use the online CheckMyOWA resource to check if your Exchange Server has appeared in their data.
If you have missed this Special Report because you were not yet a subscriber to our free daily network reports, do not worry: simply subscribe for your network or country now and specifically request all recent Shadowserver Special Reports. We will resend the Special Report specifically for your network or country (for National CERT/CSIRTs).
If you have a data set which you feel could also be of benefit to National CERT/CSIRTs and network owners world-wide to help protect victims of cybercrime, please get in touch and discuss the options for using Shadowserver’s proven reporting systems for distribution and remediation.
We hope that the new Shadowserver Special Reports will be a useful additional free tool in helping network defenders identify victims and better protect their networks and the entire Internet. Please contact us if you have any questions.