We have recently enabled a new IPv4 Internet-wide scan and report for accessible Radmin services on port 4899/TCP. Radmin is a remote access software product commonly in use today.
We scan by sending a Radmin connection request to port 4899/TCP. Our daily scans uncover around 50,000 accessible Radmin services on port 4899/TCP.
If you would like to test your own device to see if it has Radmin accessible, try the nmap command: “nmap -v -sV -p 4899 [IP]“.
While Radmin is in general considered a secure mechanism for remote access, care should be taken as with all similar types of services to ensure no misconfiguration has taken place. It is recommended to consider carefully whether every Radmin service should be accessible from the Internet at large or whether it should instead be restricted to only trusted IP addresses, thus limiting an organization’s potential exposed attack surface to a minimum. The scan is also intended to raise awareness of any unexpected Radmin instances that may accidentally have been left accessible.
Of the 50,631 Radmin services that responded to our scan on the 6th July 2020, the version breakdown was as follows:
| Radmin Version Obtained | IPv4 Count |
|---|---|
| Radmin v3.X Radmin Authentication | 36381 |
| Radmin (Details Unknown) | 7074 |
| Radmin v3.0 Windows | 3973 |
| Radmin v3.X Source IP blocked | 1253 |
| Radmin v3.3 Windows | 1024 |
| Radmin v3.X Windows Authentication | 746 |
| Radmin v2.X Windows Authentication | 152 |
| Radmin v2.X Radmin Authentication | 28 |
The country breakdown of 50,631 accessible Radmin services that responded to our probe on the 6th of July 2020 is shown below.
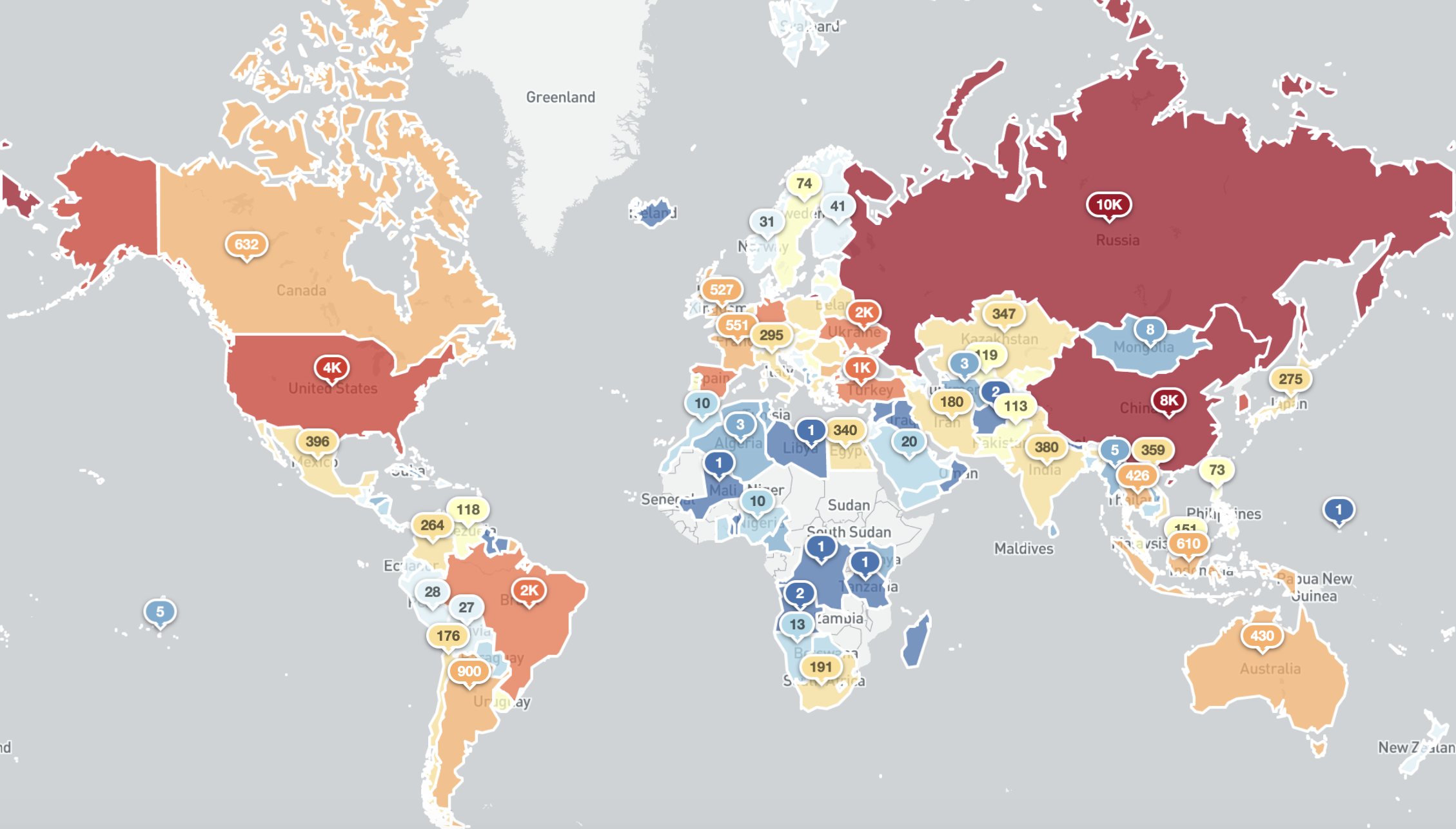
Exposed Radmin services around the world (6th July 2020)
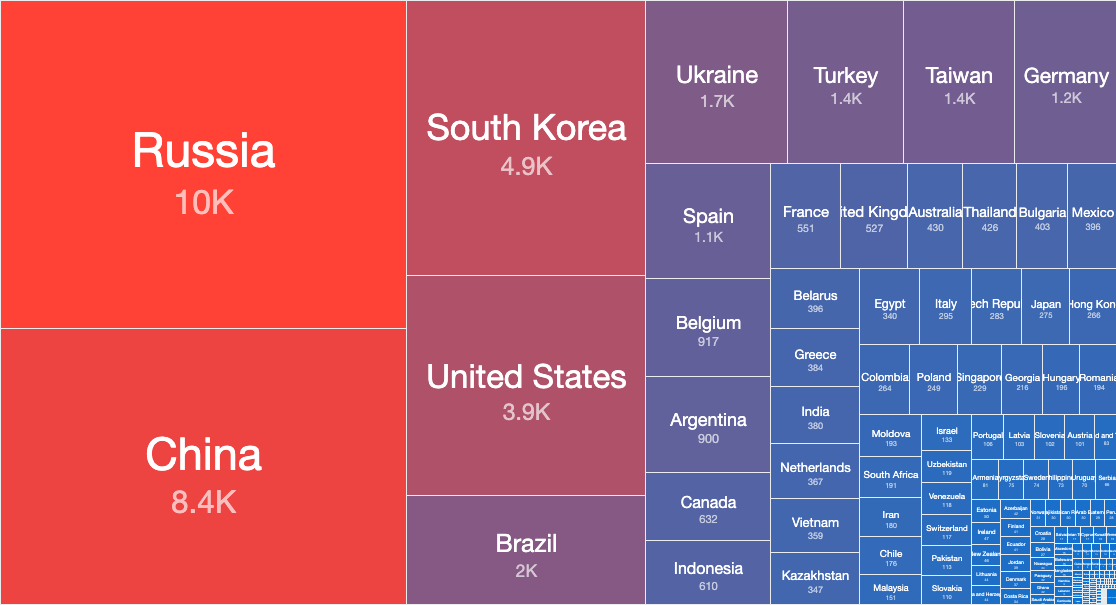
Top Countries with exposed Radmin services (6th July 2020)
Details about the format of the new report being shared can be found in the new Accessible Radmin Report page. All existing Shadowserver report subscribers are now automatically receiving the Accessible Radmin Report if any exposed Radmin services are identified within their networks and countries (for national CSIRTs).
If you are not already a subscriber to Shadowserver’s public benefit daily network reports and would like to receive this new accessible Radmin report and our other existing 79 report types, then please sign up to our free daily public benefit network remediation feed service.
You can also check the updated daily statistics for this scan on our dedicated Radmin scan page.

