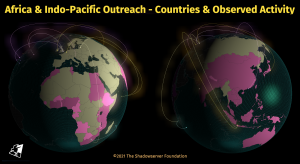
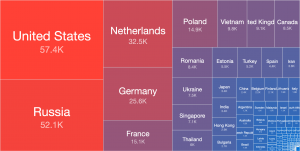
Over 3.6 million exposed MySQL servers on IPv4 and IPv6
May 31, 2022
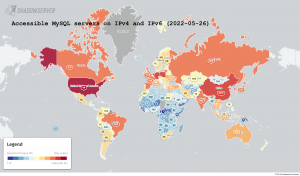
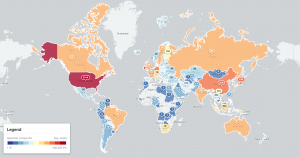
We have recently began scanning for accessible MySQL server instances on port 3306/TCP. These are instances that respond to our MySQL connection request with a Server Greeting. Surprisingly to us, we found around 2.3M IPv4 addresses responding with such a greeting to our queries. Even more surprisingly, we found over 1.3M IPv6 devices responding as well (though mostly associated with a single AS). IPv4 and IPv6 scans together uncover 3.6M accessible MySQL servers worldwide.