Shadowserver Special Reports – Exchange Scanning #4
March 15, 2021
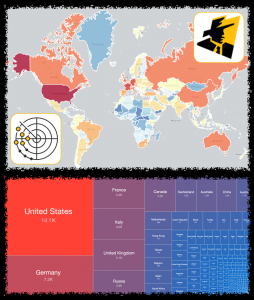
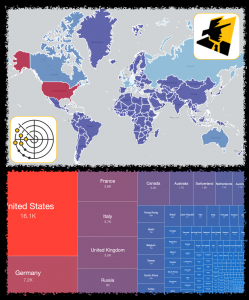
Another internet wide scan based one-off Special Report identifying 59218 potentially vulnerable Microsoft Exchange Servers on 2021-03-14 courtesy of Kryptoslogic, with a comparison of the degree of overlap in coverage between this data set and our previous one-off Special Report that was just released. If your mail servers appear in either report - please patch immediately.