Over 380 000 open Kubernetes API servers
May 17, 2022
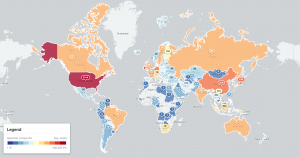
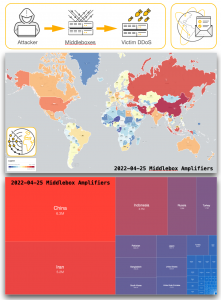
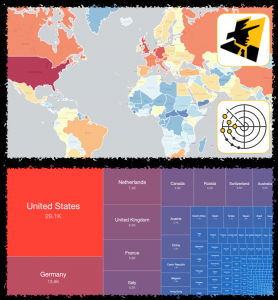
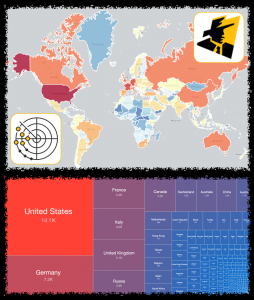
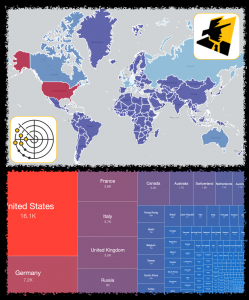
We have recently started scanning for accessible Kubernetes API instances that respond with a 200 OK HTTP response to our probes. Kubernetes is an open-source system for automating deployment, scaling, and management of containerized applications. We find over 380 000 Kubernetes API daily that allow for some form of access, out of over 450 000 that we are able to identify. Data on these is shared daily in our Accessible Kubernetes API Server Report.