Scanning for Accessible MS-RDPEUDP services
January 25, 2021
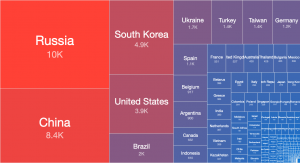
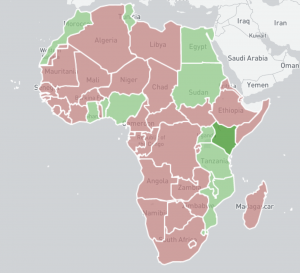
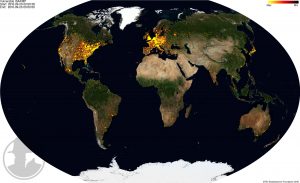
We have started daily IPv4 /0 scanning for exposed MS-RDPEUDP instances on port 3389/UDP. Aside from the usual risks associated with exposing RDP services to the Internet, this UDP extension of the popular RDP services has been found to be susceptible to amplification DDoS abuse with an amplification factor of over 84. Over 12 000 instances of MS-RDPEUDP have been found to be accessible on the IPv4 Internet.