We recently began scanning for middlebox devices that are vulnerable to Middlebox TCP reflection, which can be abused for DDoS amplification attacks. Our results are now shared daily, filtered for your network or constituency in the new Vulnerable DDoS Middlebox report.
TCP Middlebox Reflection was first disclosed in August 2021 in the Usenix paper “Weaponizing Middleboxes for TCP Reflected Amplification” authored by University of Maryland and University of Colorado Boulder researchers. Reflection based attacks have been associated primarily with UDP services in the past, but in this case apply to TCP based services instead. The research paper is accompanied by a page describing in detail how the attacks work.
In March 2022 Akamai reported observing Middlebox TCP reflection attacks in the wild.
What is a Middlebox?
As described in the Usenix paper:
A middlebox is an in-network device that sits on the path between two communicating end-hosts, and can monitor, filter, or transform packet streams in-flight. Unlike traditional network devices like routers and switches, middleboxes operate not only on packets’ headers, but also on their payloads using Deep Packet Inspection (DPI).
How does a Middlebox TCP reflection attack work?
Middlebox TCP reflection attacks are possible by taking advantage of TCP-noncompliance in network middleboxes: responding to out of state TCP packets. This behaviour, combined with the fact that middleboxes are commonly configured to block certain traffic, can be abused by an attacker to use the middlebox device as an amplifier and reflector for DDoS attacks when they send custom out of state TCP packets with the source IP address spoofed to the IP address of the DDoS victim.
As noted by Akamai:
Attackers can craft various TCP packet sequences that contain HTTP request headers; in these HTTP headers, a domain name for a blocked site is used as the host header. When these packets are received by the middlebox that is configured to not allow access to the site, the middlebox responds, typically with HTTP headers and in some cases entire HTML pages. These responses provide attackers with a reflection opportunity, and in some cases a significant amplification factor.
How we scan
Please note that exploiting TCP Middlebox reflection involves sending custom packets that push payloads in TCP packets that normally do not contain payloads (such as for example a TCP SYN packet), so you cannot verify the susceptibility of a device to attacks by simply running an nmap scan or trying a telnet or netcat connection to the device.
We identify abusable middleboxes through scanning with custom TCP packets, specially constructed to elicit the amplified responses.
We currently scan IPv4 addresses worldwide with 2 methods described in the Usenix paper.
- SYN packet with sequence number s, followed by a PSH + ACK with sequence number s+1 containing a HTTP GET payload request for a forbidden resource
- SYN packet with a HTTP GET payload request for a forbidden resource.
A forbidden resource in this case is a URL that the middlebox is configured to block.
We base our scans on https://github.com/Kkevsterrr/zmap/blob/618f7dd2b2a0c79a71f00aabc40ab3f9addcc9bd/src/probe_modules/module_forbidden_scan.c
The HTTP GET payload request embedded in the payloads is: GET / HTTP/1.1\r\nHost: www.you[redacted].com \r\n\r\n
Scan results
The scan methods described above have allowed us to uncover over 18,800,000 IPv4 addresses responding to our Middlebox probes. The country with the highest number of such responses is from China (over 6.3M), followed by Iran (around 5.2M) and Indonesia (over 2.7M).
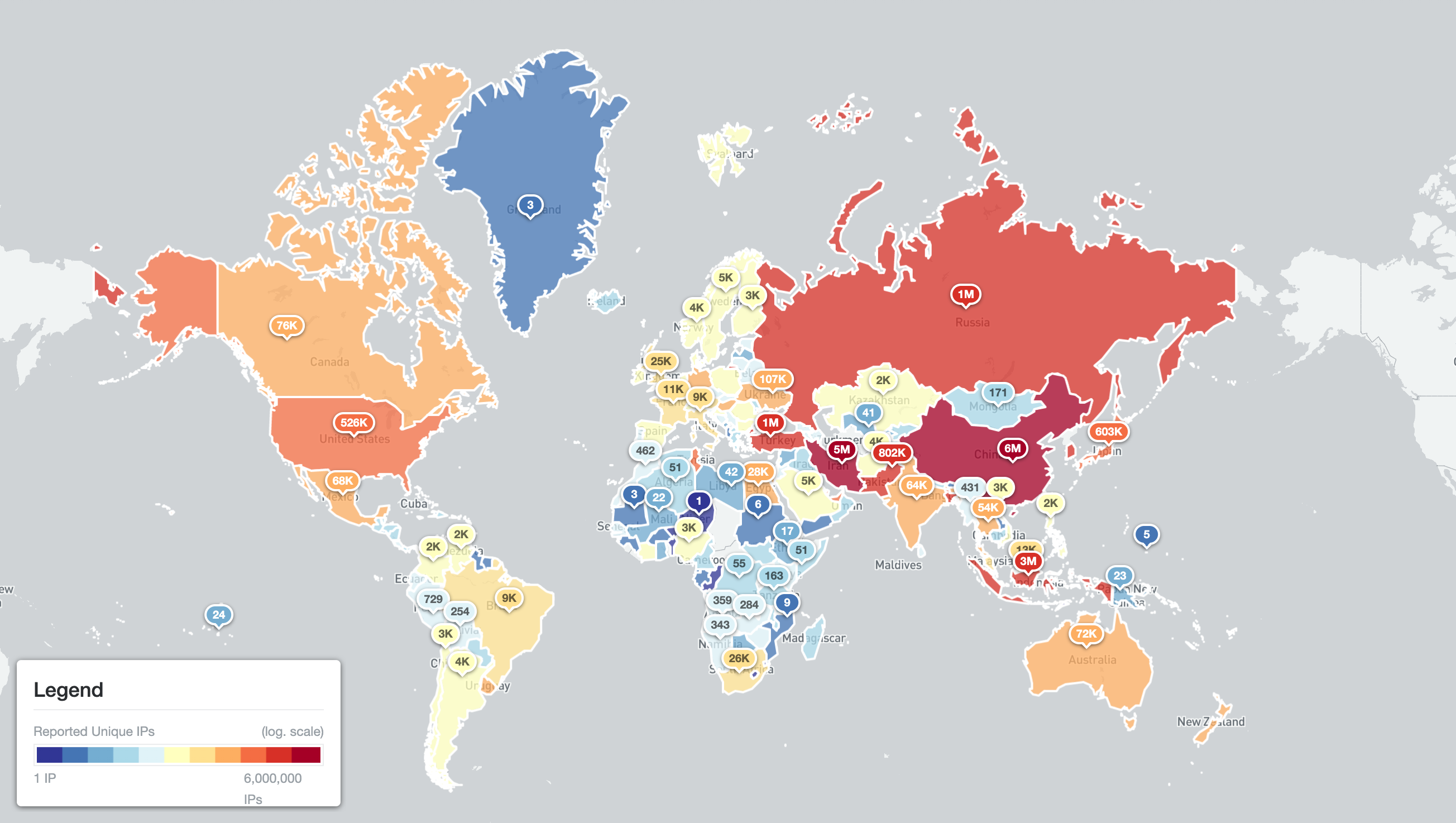
Abusable middlebox devices worldwide by unique IPv4 addresses (23rd April 2022)
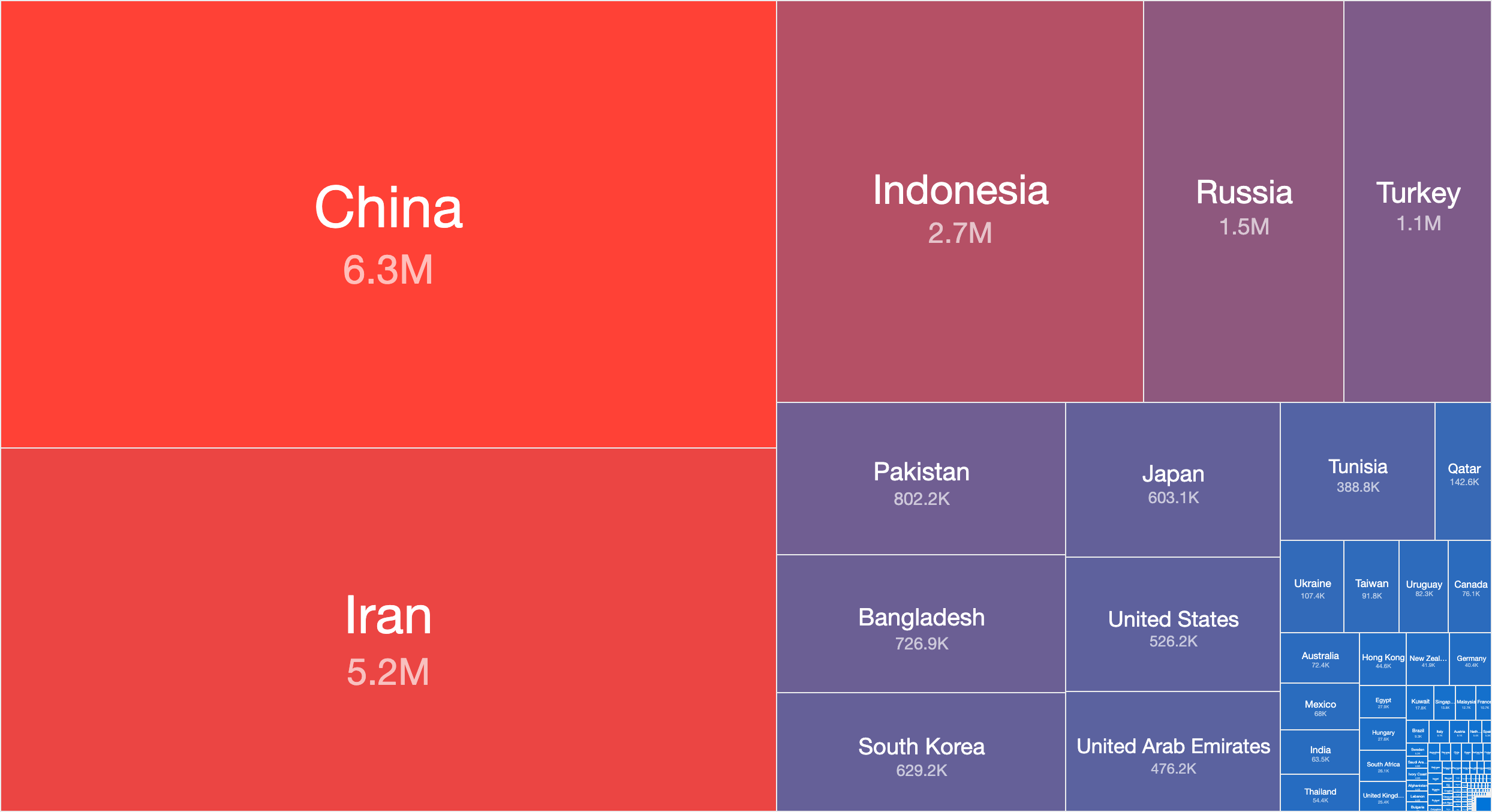
Countries with the most abusable middlebox devices worldwide by unique IPv4 address count (23rd April 2022)
It is possible that more responding IP addresses can be uncovered by querying for a different forbidden URL. Note also that we have been scanning IPv4 addresses only. We plan to scan IPv6 addresses as well in the future (based on IPv6 address hitlists).
Amplification factor
Based on the response received, we also calculate the amplification factor. This amplification is is based solely on the payload size sent and payload size received (ie. without TCP/IP header sizes).
The top amplifier we found has an amplification rate of 6,583,549 with the TOP 10 all above 50,000.
When we remove the biggest amplifiers (there are 70 with an amplification factor over 10,000), the average amplification rates are:
- SYN with GET: around 19.4
- SYN+PSH:ACK: around 7.6
The median amplification rates are as follows:
- SYN with GET: around 9
- SYN+PSH:ACK: around 6
Mitigation
If you are notified of a device that is abusable, please consider countermeasures/mitigation techniques that have been described in the sources referenced above.
For example, Akamai suggests firewall ACLs can be used to block the known incorrect patterns.
Note however that the request can generally be sent on any port, simply mitigating for queries to 80 is not enough as the middleboxes detect and respond to traffic on any port.
Reconfiguration of the middlebox can also resolve the issue. Reach out to your appliance manufacturer/vendor for guidance.
Subscribe to get free data on abusable Middlebox devices in your network or constituency!
Details about the format of the new report being shared can be found in the Vulnerable DDoS Middlebox report. If you are an existing subscriber you will get the report daily should any IP be found in your network/constituency.
If you are not already a subscriber to Shadowserver’s public benefit daily network reports and would like to receive this new report and our other existing report types (covering not just other scan results, but observations from sinkholes, honeypots, darknets, sandboxes, blocklists and other sources), then please sign up to our free daily public benefit network remediation feed service.
If you have any questions or comments on the new report please contact us.
For more information on our scanning efforts, check out our Internet scanning summary page.

