Since July 2019, The Shadowserver Foundation has been participating in a new EU CEF (Connecting Europe Facility) funded project called VARIoT. The main goal of the VARIoT (Vulnerability and Attack Repository for IoT) project is to create new services to provide security-related actionable information about the Internet of Things (IoT). One of The Shadowserver Foundation’s roles in the project involves expanding our internet wide daily port scanning capability to enable the mapping of exposed IoT devices on the Internet. The aim is to alert National CSIRTs and network owners of potentially vulnerable IoT devices, as well as to build higher level statistics on IoT device types seen on a per-country level, which can be shared via the European Data Portal with the general public.
As part of these efforts, we have recently begun scanning all 4 billion routable IPv4 addresses for publicly accessible MQTT (Message Queuing Telemetry Transport) broker services enabled on port 1883/TCP. MQTT is a lightweight publish/subscribe protocol designed for the Internet of Things. The goal of the scanning is to identify not just the exposed MQTT brokers out there but, in particular, MQTT instances that have no authentication enabled – allowing the broker to be anonymously accessed by anyone. This could mean that MQTT messages may be read, or potentially even published by a remote attacker. Additionally, the MQTT service on port 1883/TCP is unencrypted, so even user/password protected instances can still lead to data leakage.
Our Internet wide MQTT IPv4 scans are now carried out daily. We scan from Shadowserver’s existing production scanning cluster IP ranges (which are already whitelisted by many major ISPs) using the standard 24 byte MQTT Connect command and capture the response. All MQTT brokers that we find, along with the captured responses, are incorporated in a new free daily network report – the Open MQTT Report. Since March 13th 2020, the new MQTT report has been sent out daily, as part of our free victim remediation feeds to 107+ National CSIRTs and 4600+ network owners worldwide.
To provide an illustration of the size of the exposed MQTT broker footprint on the Internet, on 12th March 2020, 71,508 IP addresses responded to our probes. A breakdown of these responses for the 12th of March 2020 follows:
| MQTT Response | IPv4 Count |
|---|---|
| Connection Accepted | 41558 |
| Connection Refused, not authorized | 19476 |
| Connection Refused, bad user name or password | 8933 |
| Connection Refused, Server unavailable | 763 |
| Connection Refused, unacceptable protocol version | 384 |
| Connection Refused, identifier rejected | 381 |
| Unknown | 13 |
Obviously these counts only represent devices that are not firewalled and allow direct querying.
The IP-geolocated country breakdown of the above reachable MQTT responses looks as follows:
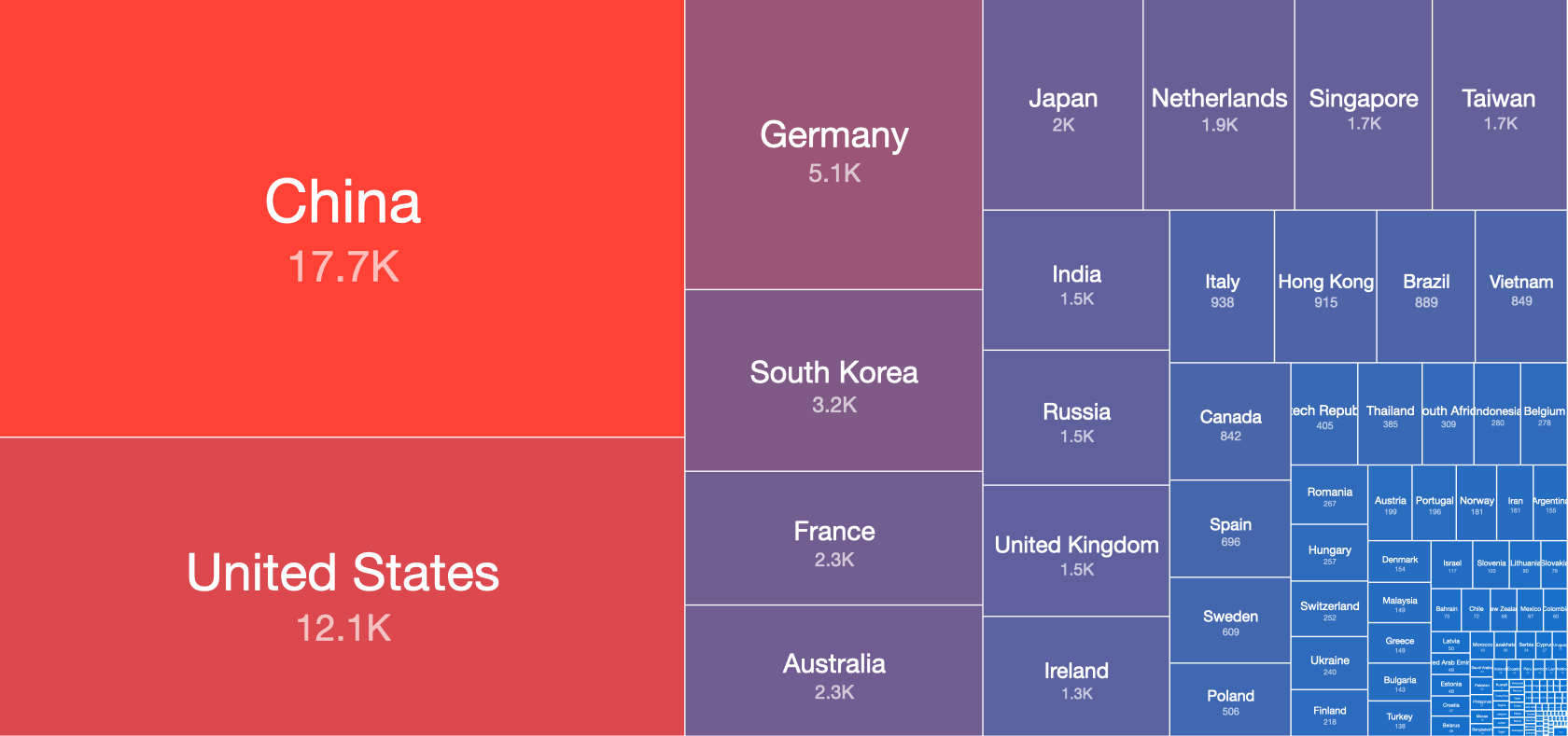
Top Countries with reachable IPv4 MQTT instances (12th March 2020)
Out of these exposed devices, 41,558 IPs allow for anonymous access. This is 58% of the accessible broker instances. The IP-geolocated country breakdown of the IP addresses that do allow anonymous access is as follows:

Top Countries with reachable anonymously accessible IPv4 instances (12th March 2020)
Details on the format of the new report being shared can be found in the new Open MQTT Report page. All existing Shadowserver report subscribers are now receiving the Open MQTT Report if any accessible MQTT brokers are identified within their networks and countries.
We hope that the data being shared will lead to a reduction of anonymously accessible MQTT broker services, as well as raise awareness among network owners to the potential exposure of data through non-encrypted services. One thing we know for certain is that new security vulnerabilities are being discovered all the time. If you do not need to have your IoT device’s MQTT broker accessible from the Internet to everyone, authenticate your clients, consider firewalling to restricted clients only, and enable the broker on the SSL/TLS aware service on port 8883/TCP instead. We hope that through the EU CEF funded VARIoT project we will be able to help network owners better protect themselves by recognising what IoT devices they have with accessible services exposed to the Internet.
If you are not a subscriber to Shadowserver’s free daily network reports but would like to receive this new report and our other existing 76 report types, then please sign up to our free daily remediation feed service. You can also check the updated statistics for this scan on our dedicated MQTT scan page.

