We are happy to announce multiple enhancements to our public Dashboard, particularly to the Exploited Vulnerability data collected by our server-side honeypot sensors, thanks to funding provided by the UK Foreign Commonwealth and Development Office (FCDO). We launched our public Dashboard in September 2022, supported by UK FCDO funding, and subsequently extended the data visualizations to encompass IoT related scan results and exploited vulnerability tracking, gathered through EU CEF VARIoT project funding. We have now added a number of extra features and improvements as demonstrated below.
CISA Known Exploited Vulnerabilities (KEV) catalog filtering
Shadowserver operates thousands of sensors globally that include honeypots designed to track attempted exploitation of known software vulnerabilities. Exploitation activity as observed by these sensors is updated daily on our Dashboard in the form of a Top Exploited Vulnerability list.
The US Cybersecurity & Infrastructure Agency (CISA) maintains an authoritative list of vulnerabilities confirmed as being exploited in the wild, called the CISA Known Exploited Vulnerability catalog. All US federal civilian executive branch (FCEB) agencies are required to remediate vulnerabilities included in the CISA KEV catalog within prescribed timeframes, under a binding operational directive aimed at improving cybersecurity. CISA strongly recommend patching these vulnerabilities immediately.
As part of our latest Dashboard update, we have now added a new feature to the list of displayed results that matches each of the Common Vulnerabilities and Exposures (CVEs) detected by our honeypots with the CISA KEV catalog. This potentially enables better prioritization of which CVEs should be triaged and handled by your constituency or network.
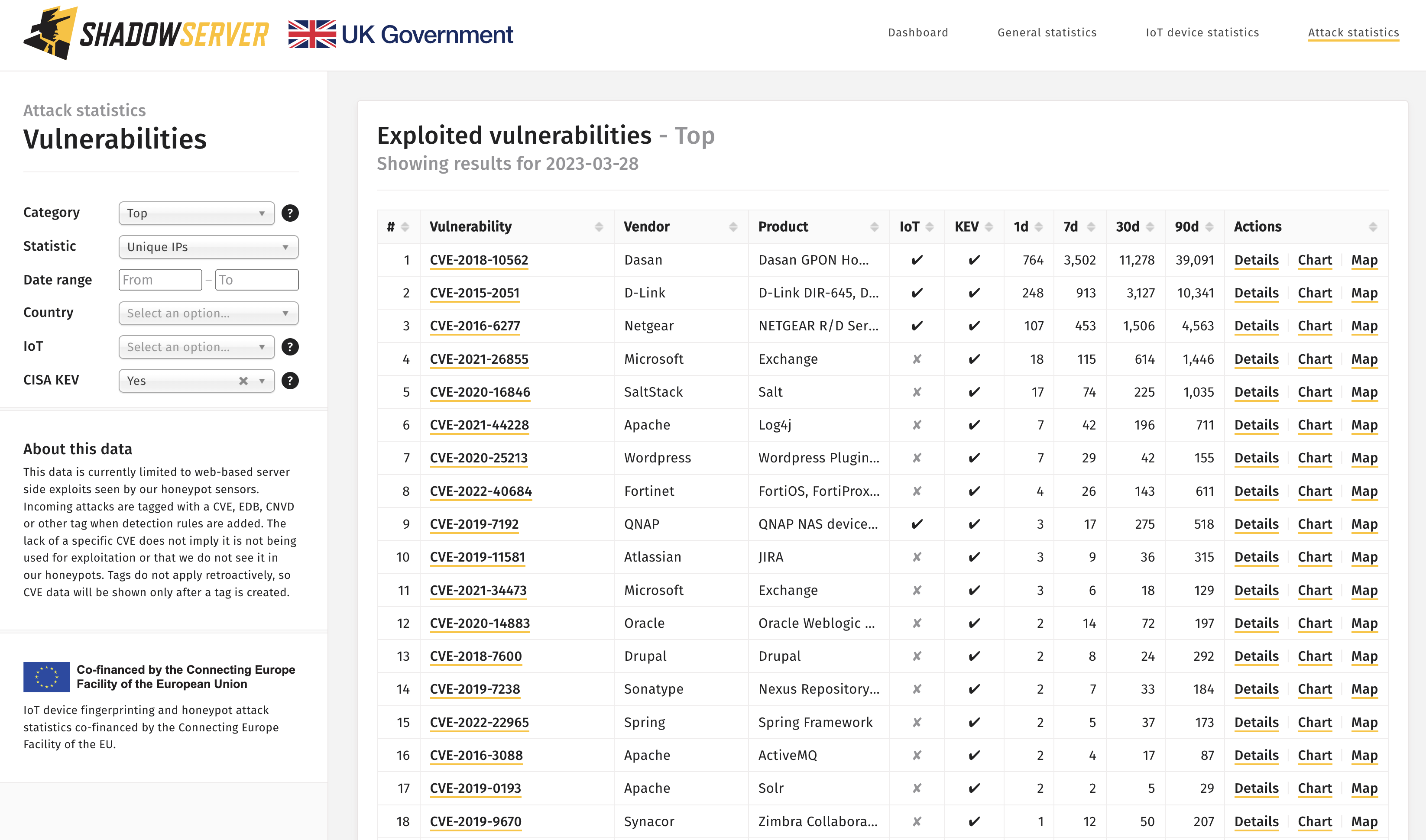
Exploited vulnerabilities filtered by presence in the CISA KEV
Country level filtering
Another newly added feature allows for filtering the exploited vulnerability list by country. For example, the following query displays the most common CVE exploitation sourced from US networks.
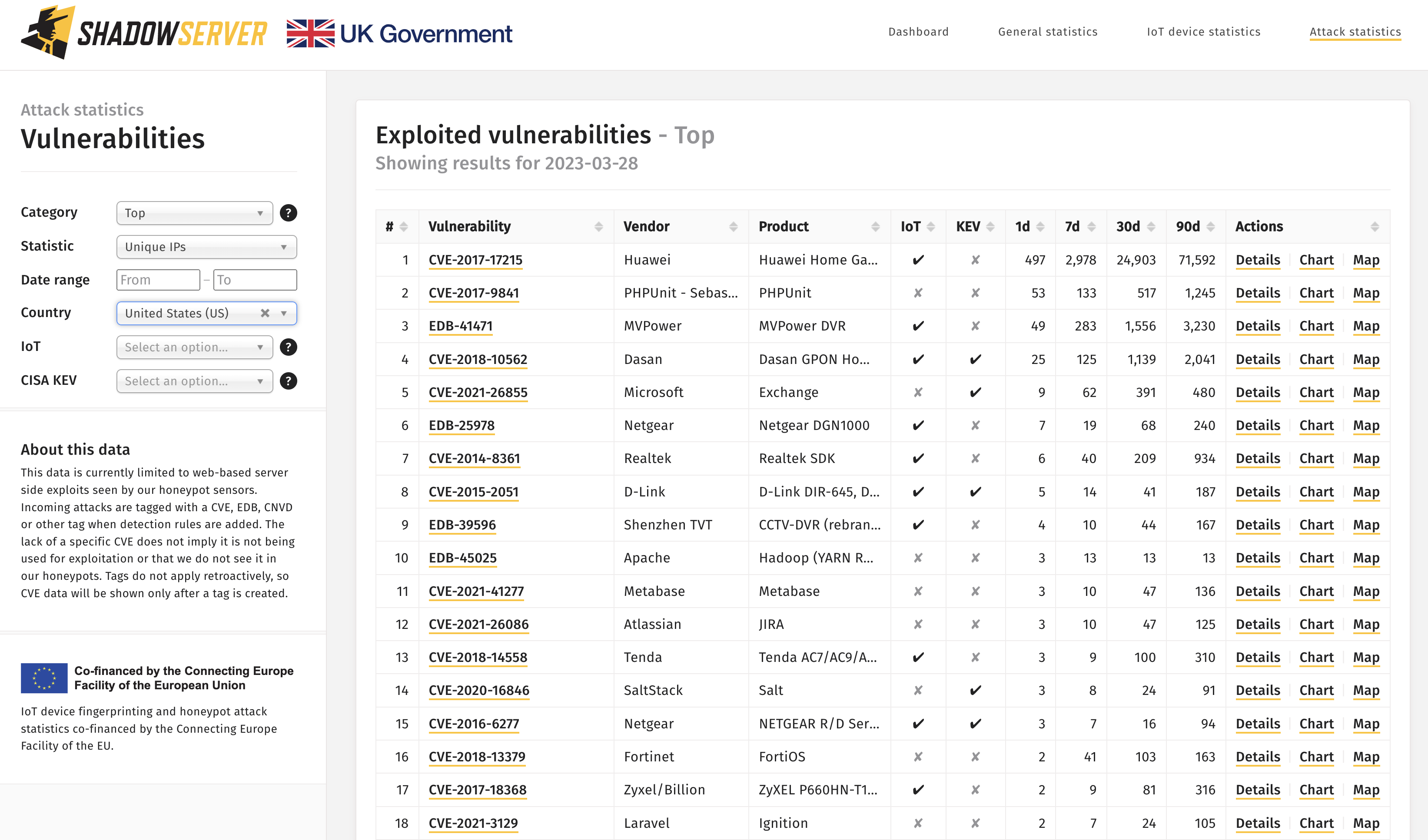
Exploited vulnerabilities attempted from IP addresses geo-locating to the US
This filter also includes the option of viewing anomalies per country as well, which are updated daily. For example, the following query displays volume based anomalies in CVE exploitation sourced from US networks.
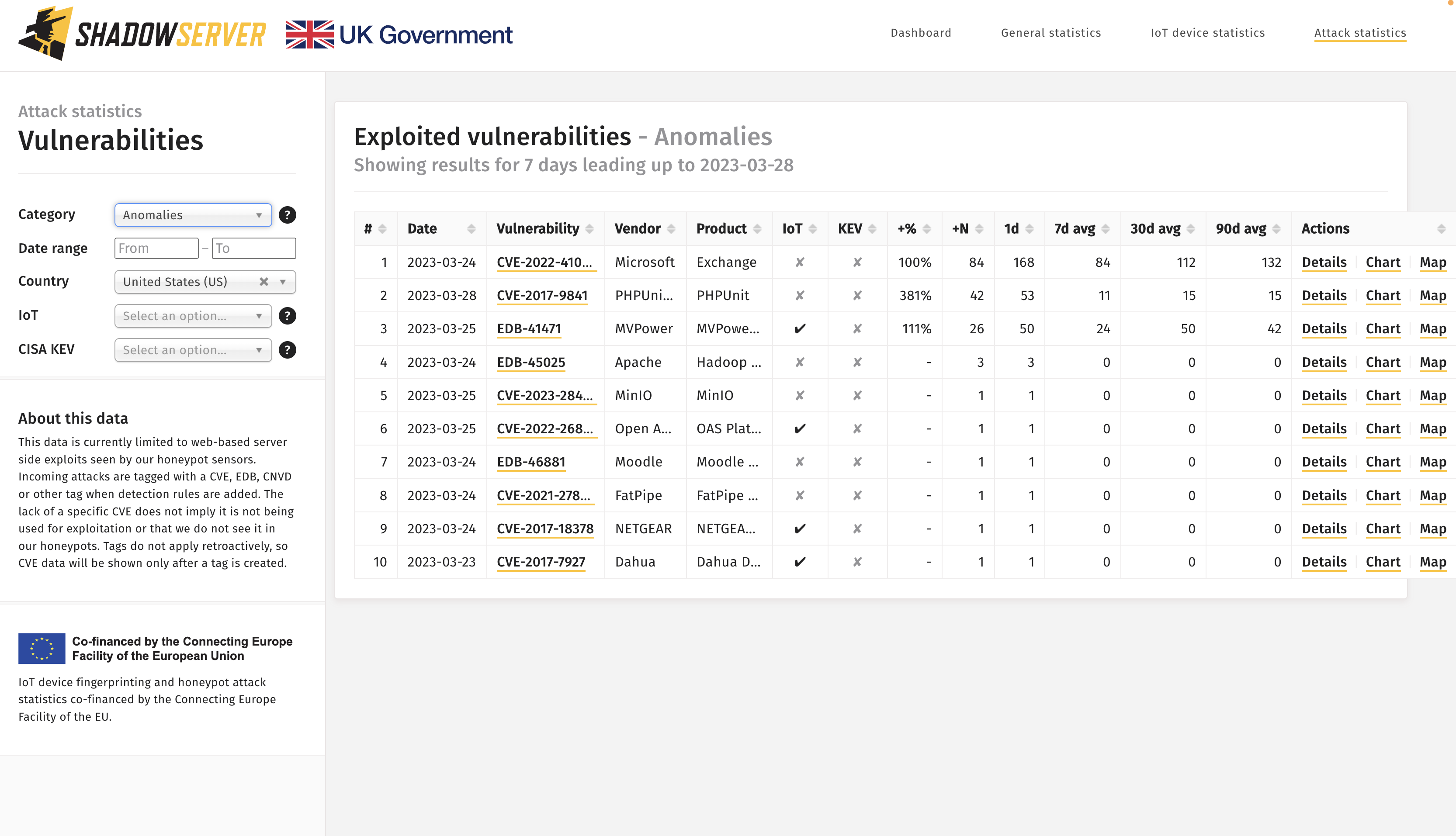
Anomalies in CVE exploitation sourced from US networks
IoT vulnerability filtering
You can now also track exploited vulnerabilities by whether they affect Internet of Things (IoT) devices or not, by selecting an IoT filter. This should help improve situational awareness in the community of the types of devices under threat.
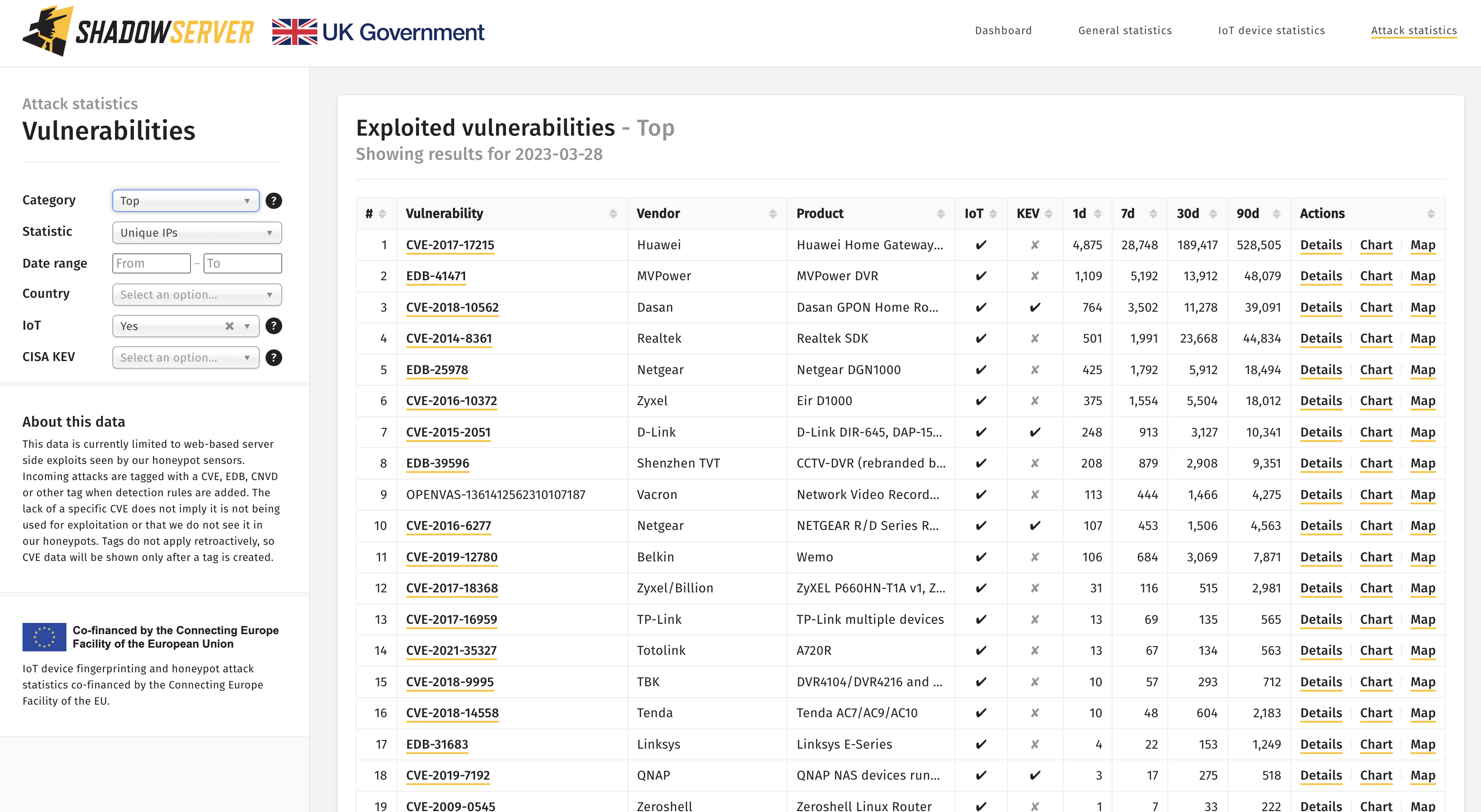
Exploited vulnerabilities filtered for only IoT devices
Improved filtering of CVE vulnerability scan tags
Aside from the exploited vulnerability enhancements, we have also improved filtering functionality in other areas of the dashboard. It is now much easier to filter the results of our scans using CVE numbers (or other) tags. When selecting vulnerable HTTP instances or Microsoft Exchange Server instances you can now select CVE tags with ‘+’ as a suffix. The values for tags with the ‘+’ suffix would be the sum of the rows containing that CVE (e.g. tag like ‘%cve-2021-26855%’). For example, to track Exchange servers vulnerable to CVE-2021-26855 you would use this query.
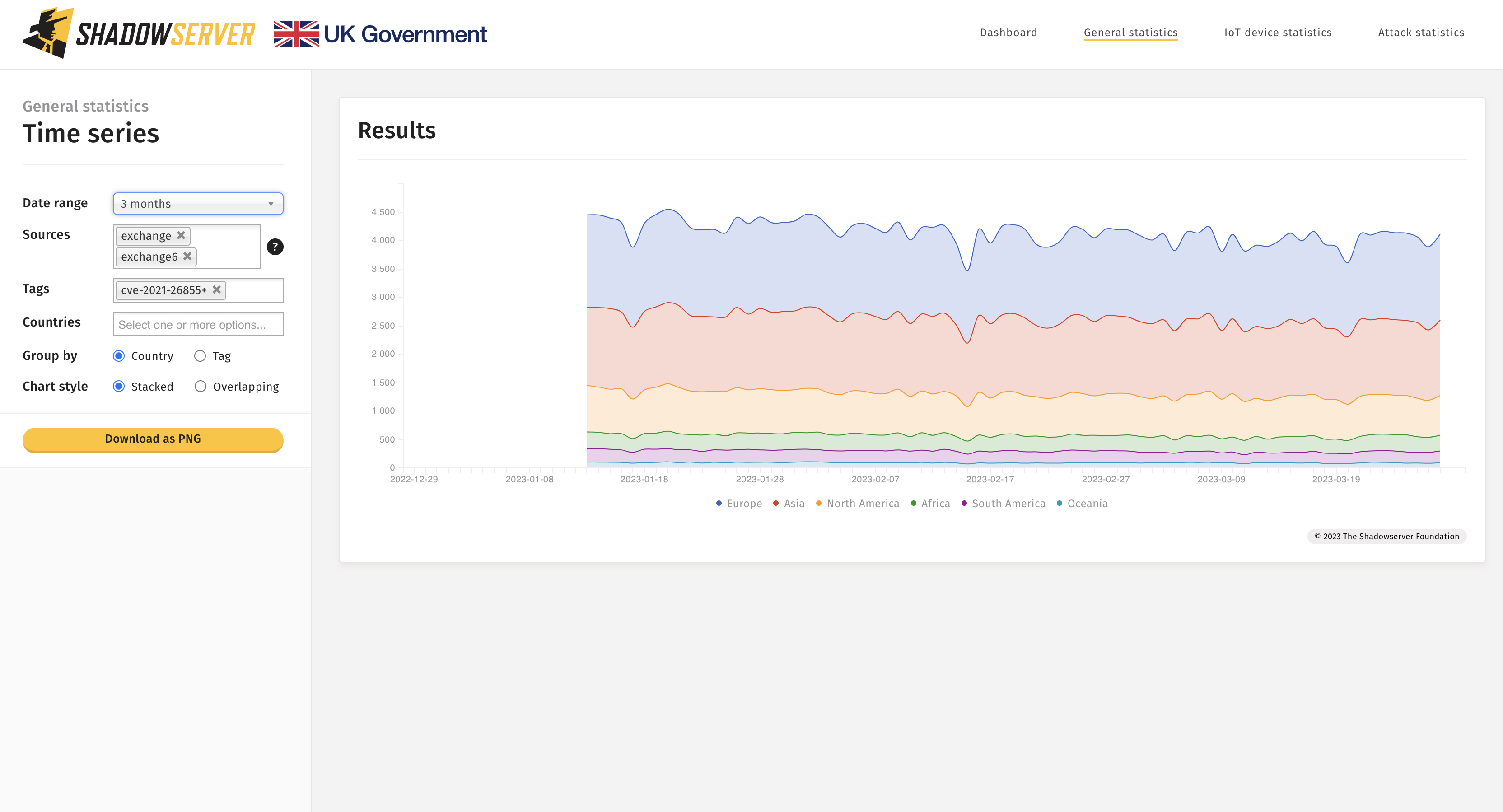
Exchange instances vulnerable to CVE-2021-26855
We hope the updates provide new insights into attacks seen on the Internet and improve the usability of our Dashboard. We would like to thank the UK FCDO for their continued support.
If you have not done so yet, please sign up for our free daily threat feeds that will provide you specific, actionable IP information about threats or vulnerabilities seen on your network(s). These will be filtered for your networks/domains or constituency (or country, for National CSIRTs).
Please also consider joining our Alliance, which will provide you with additional insights, details into threats that we see and other benefits (as well as helping to ensure financial sustainability for all of Shadowserver’s free public benefit services).
For any questions, please contact us.

