Introduction
Shadowserver has recently been funded by the UK Foreign, Commonwealth & Development Office (FCDO) to provide more detailed and tailored cyber threat insight support to countries in the Gulf Region, specifically Kuwait, Bahrain, the United Arab Emirates (UAE), Saudi Arabia, Oman and Qatar (“the Gulf“). These activities included obtaining a better understanding of the device makeup of the publicly exposed attack surface in those countries, vulnerability exposure (especially relating to emerging threats) and observed attacks/infected devices – coming both from and directed at the region. The intention is to enrich Shadowserver’s free daily threat feeds and public benefit services to the region, providing National CSIRTs and other system defender entities (organizations that are network owners) with a better awareness of their threat and vulnerability landscape, thus helping them to improve their cybersecurity posture.
This work with the FCDO builds on our previous global outreach to Africa, Indo-Pacific, Central and Eastern Europe (CEEC) to shine a cyber security spotlight on the Gulf Region with a specific focus on Kuwait, Bahrain, the UAE, Saudi Arabia, Oman and Qatar. For a review of previous FCDO supported activities please read:
- UK Foreign, Commonwealth & Development Office funds Shadowserver surge in Africa and Indo-Pacific regions
- Continuing Our Africa and Indo-Pacific Regional Outreach
- More Free Cyber Threat Intelligence For National CSIRTs
- Shadowserver’s New Public Dashboard
- Observations on cyber threat activity and vulnerabilities in Indonesia, Malaysia, Philippines and Thailand
Device Fingerprinting
As part of these activities, Shadowserver engaged in adding detection fingerprints for devices observed in the region during our daily Internet scanning. This includes identifying the vendor, type and model of publicly exposed devices, so that Internet defenders in those countries will be better aware of their exposed assets when a potential new threat appears. Note we make no assessment of device vulnerability, only exposure.
The bar chart below (taken from our public dashboard) shows the top 20 device vendors by volume identified across the region, including some well known vendors such as Huawei, Fortinet, Cisco and MikroTik:
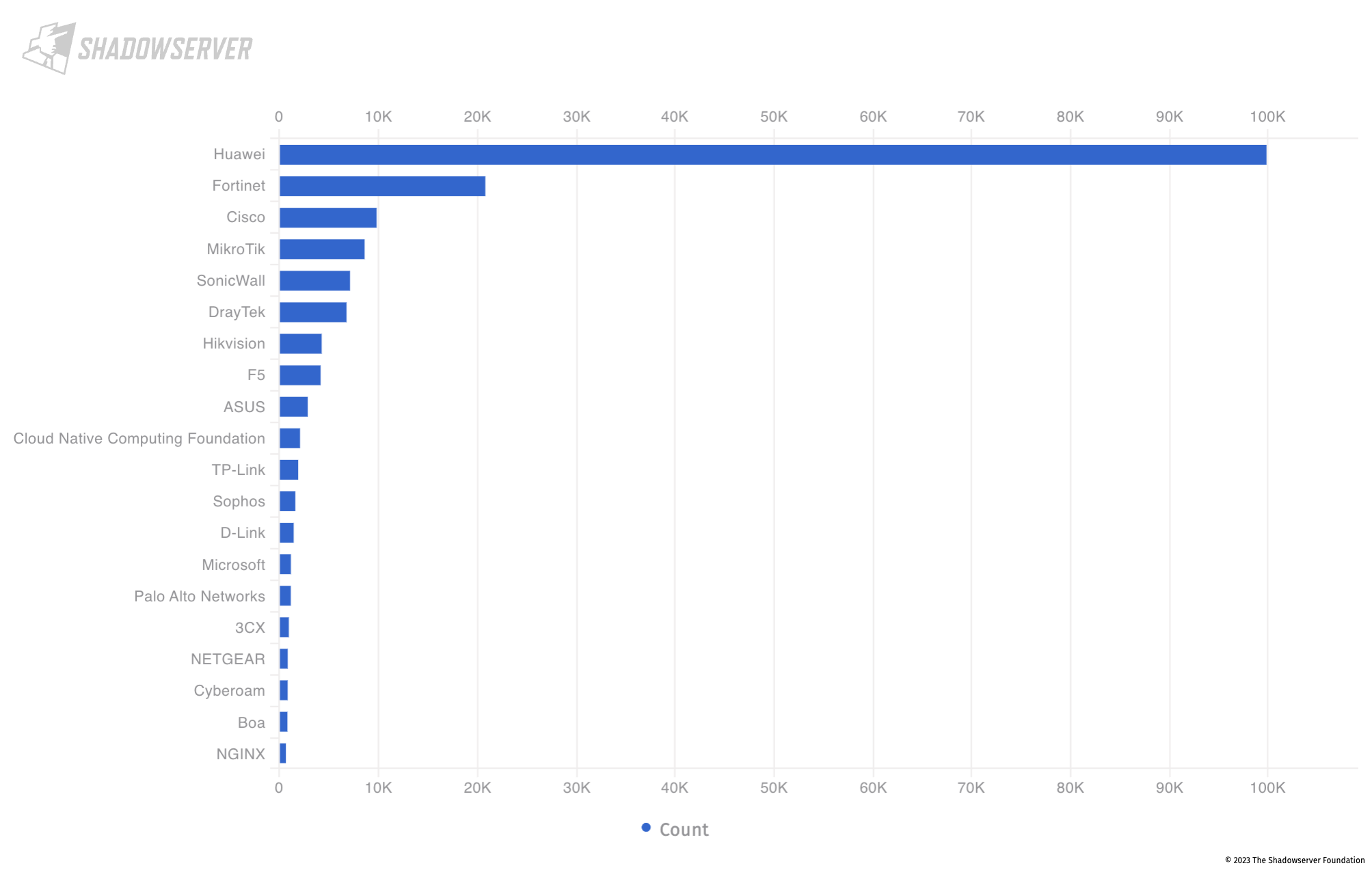
Top 20 exposed device vendors found across the Gulf countries (average daily scan results from 2023-03-01 to 2023-04-30)
Drilling down into the publicly exposed devices by country, we observe that the above mentioned vendors form the majority of the (exposed) population in the region, with the exception being Oman, where there is almost a monopoly of Huawei devices (over 74k devices, with Fortinet less than 1.2k as the second highest device vendor observed by volume).
As displayed in the bubble diagram below, the top exposed device vendor for Bahrain is the Cloud Native Computing Foundation who maintain the open source Kubernetes platform. Kubernetes is a popular open-source system for automating deployment, scaling, and management of containerized applications:
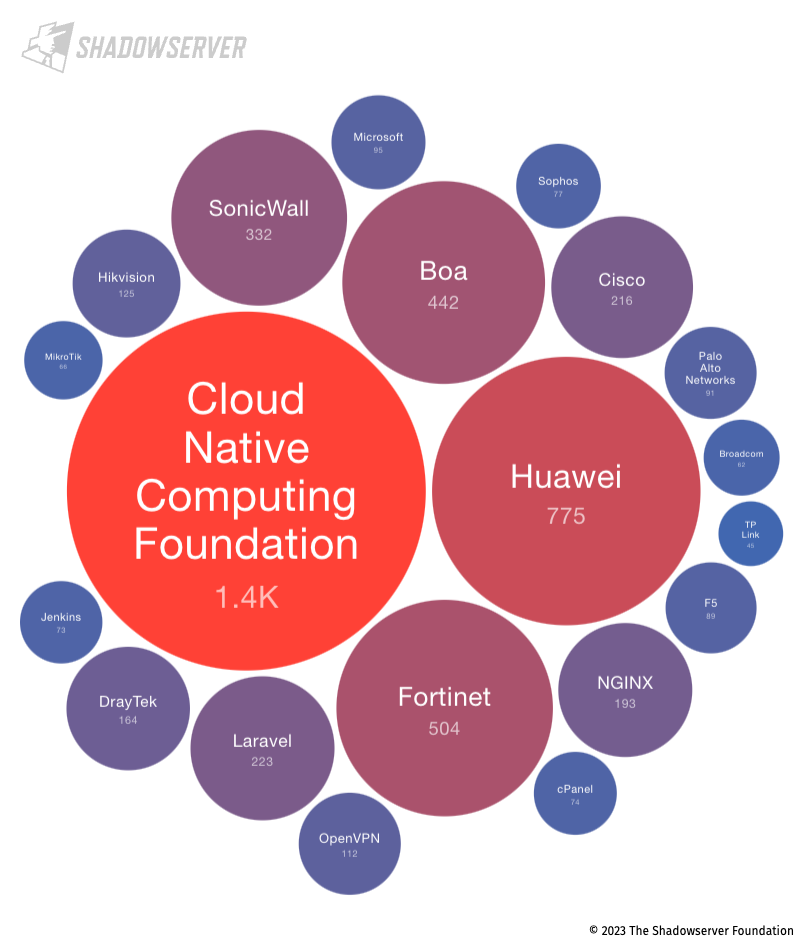
Top 20 exposed device vendors found in Bahrain (average daily scan results from 2023-03-01 to 2023-04-30)
We published a blog about Kubernetes API exposure in 2022. A new Kubernetes security audit performed by the NCC Group has recently identified a number of bugs around user and network permissions (related to access control and authentication).
Over 1.4k exposed Kubernetes instances represent a substantial potential attack surface (relative to total exposure in the Gulf), and while we do not specifically identify any vulnerabilities, reducing the attack surface would be good practice.
Looking at Kuwait, we observe that perhaps surprisingly, Huawei devices are not seen in high numbers, with Fortinet, Cisco and TP-Link being the most common vendors:
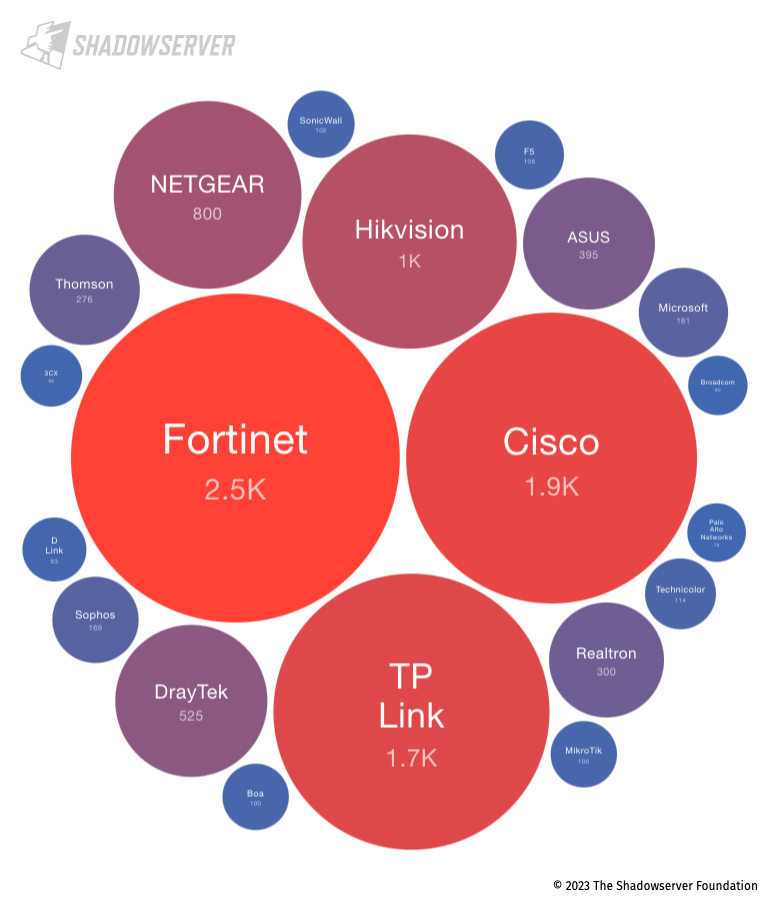
Top 20 exposed device vendors found in Kuwait (average daily scan results from 2023-03-01 to 2023-04-30)
We share actionable, detailed and IP-specific data about exposed devices in your network/constituency in the Gulf and around the world in the Device Identification report.
Critical Vulnerabilities (in exposed infrastructure)
One of the most important elements of our free public benefit scans is detection and reporting of critical vulnerabilities in public facing Internet infrastructure to National CSIRTs and network defenders. The critical vulnerabilities we report on allow remote code execution on multiple Internet facing services (which can potentially lead to breaches and ransomware attacks). In the following analysis, we will typically focus on HTTP related vulnerabilities, but we will also mention an older but still critical SNMP issue. These vulnerabilities are typically exploited in the wild, either through ubiquitous or targeted attacks, and often result in security breaches and sometimes ransomware deployment.
We find that Fortinet CVE-2022-42475 (FortiOS SSL-VPN heap based buffer overflow vulnerability) remains a prevalent weakness across the region. This is unfortunately consistent with other global regions in terms of a critical volume of detected devices that still remain unpatched.
The UAE is most vulnerable to CVE-2022-42475, accounting for approximately one-third of all publicly-exposed, critically vulnerable instances in the Gulf Region.
Nevertheless, as shown in the chart below, substantial volumes of vulnerable Fortinet devices remain in all 6 Gulf Region countries. It is clear that action on those devices is still urgently needed:
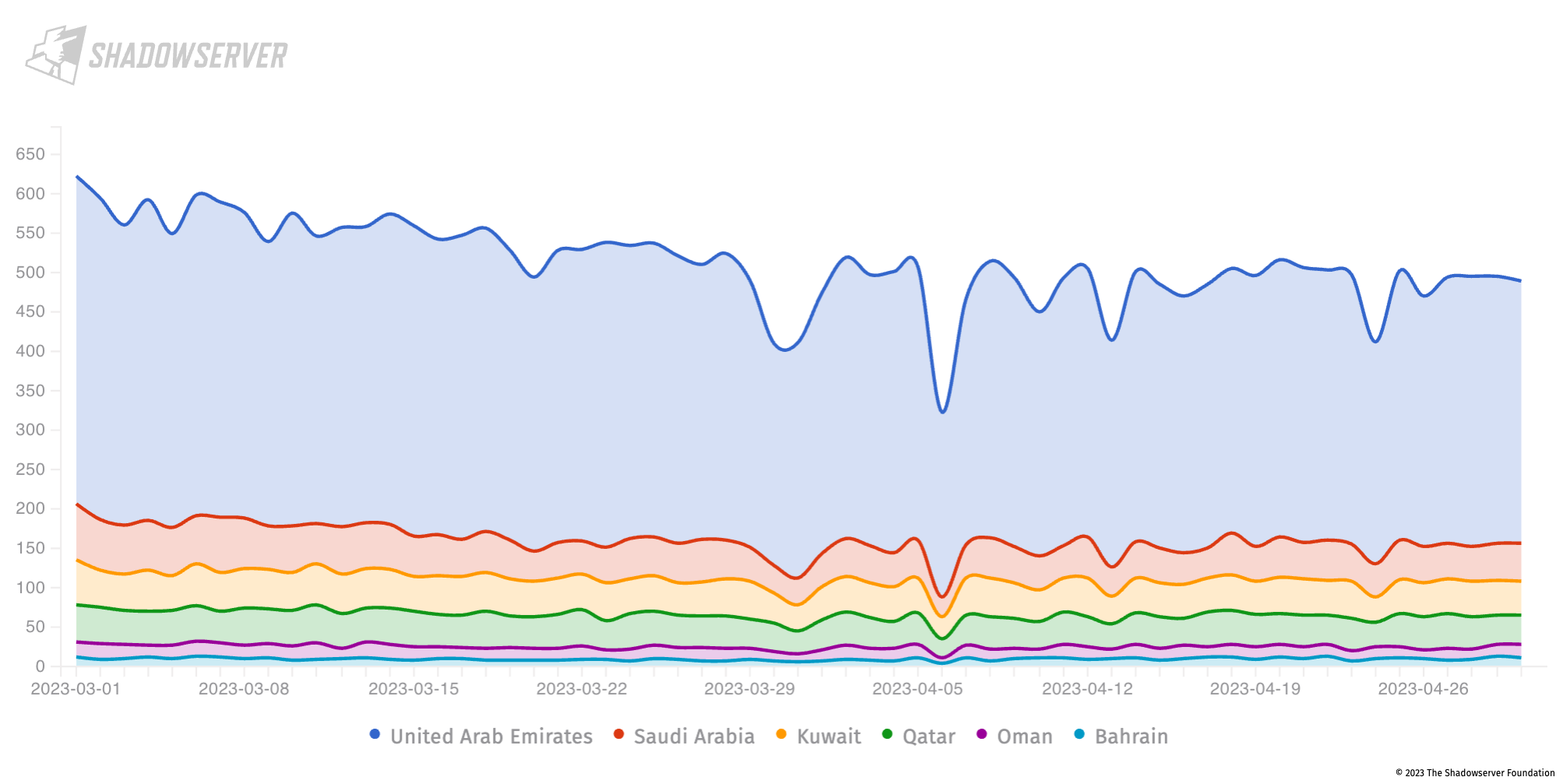
Fortinet CVE-2022-42475 vulnerable devices in the Gulf (daily scan results from 2023-03-01 to 2023-04-30), Y-Axis = unique IP address count
In Bahrain, we also observe CVE-2023-27898 (a vulnerability in the Jenkins open source automation server which could lead to code execution on targeted systems) in a small volume:
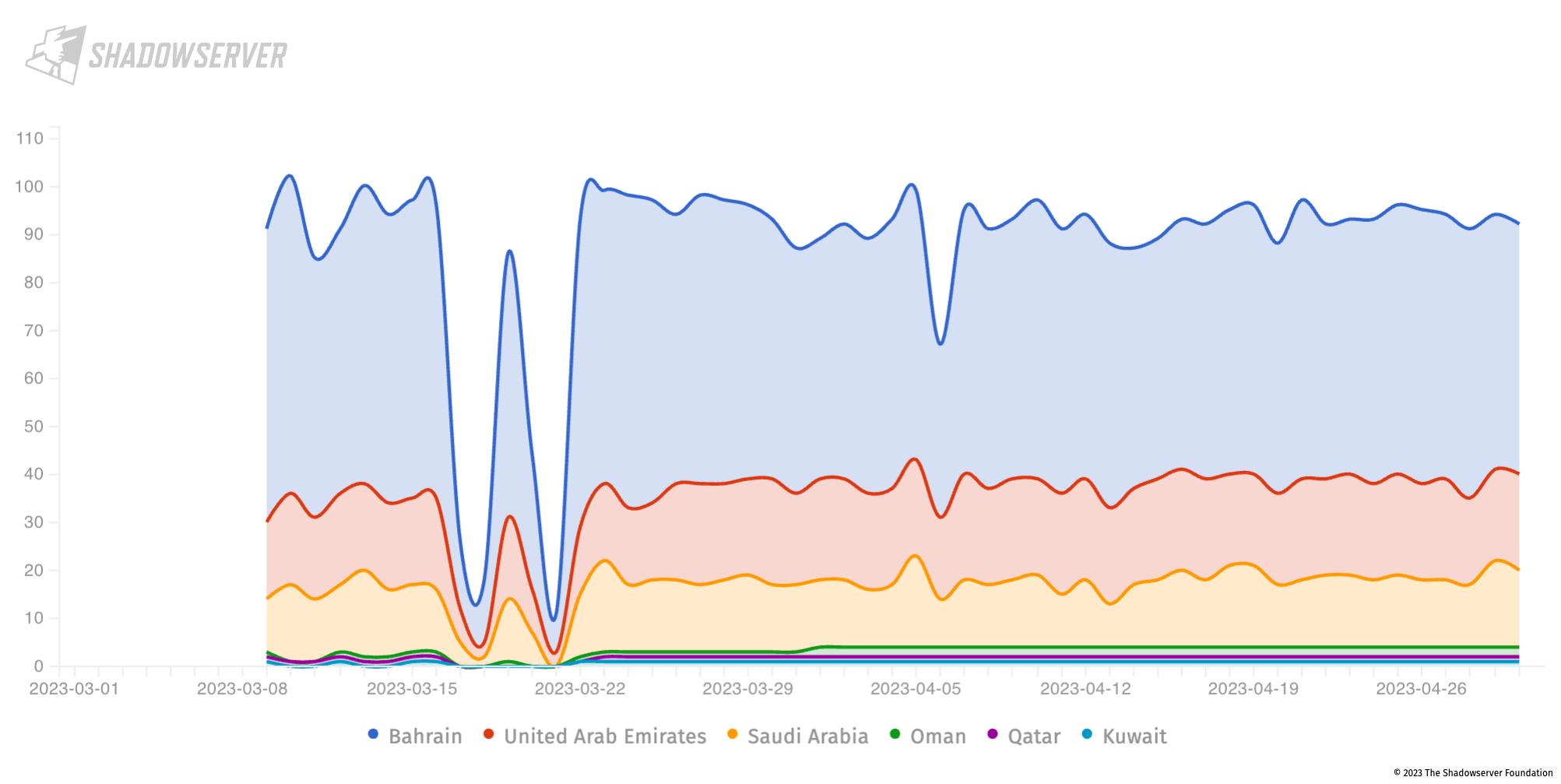
Jenkins CVE-2023-27898 vulnerable devices in the Gulf (daily scan results from 2023-03-01 to 2023-04-30), Y-axis is unique IP address count
In addition, we find a number of exposed git configurations. Git source code management system configuration data can potentially reveal sensitive information and, as such, should be made secure as a priority for all operators:
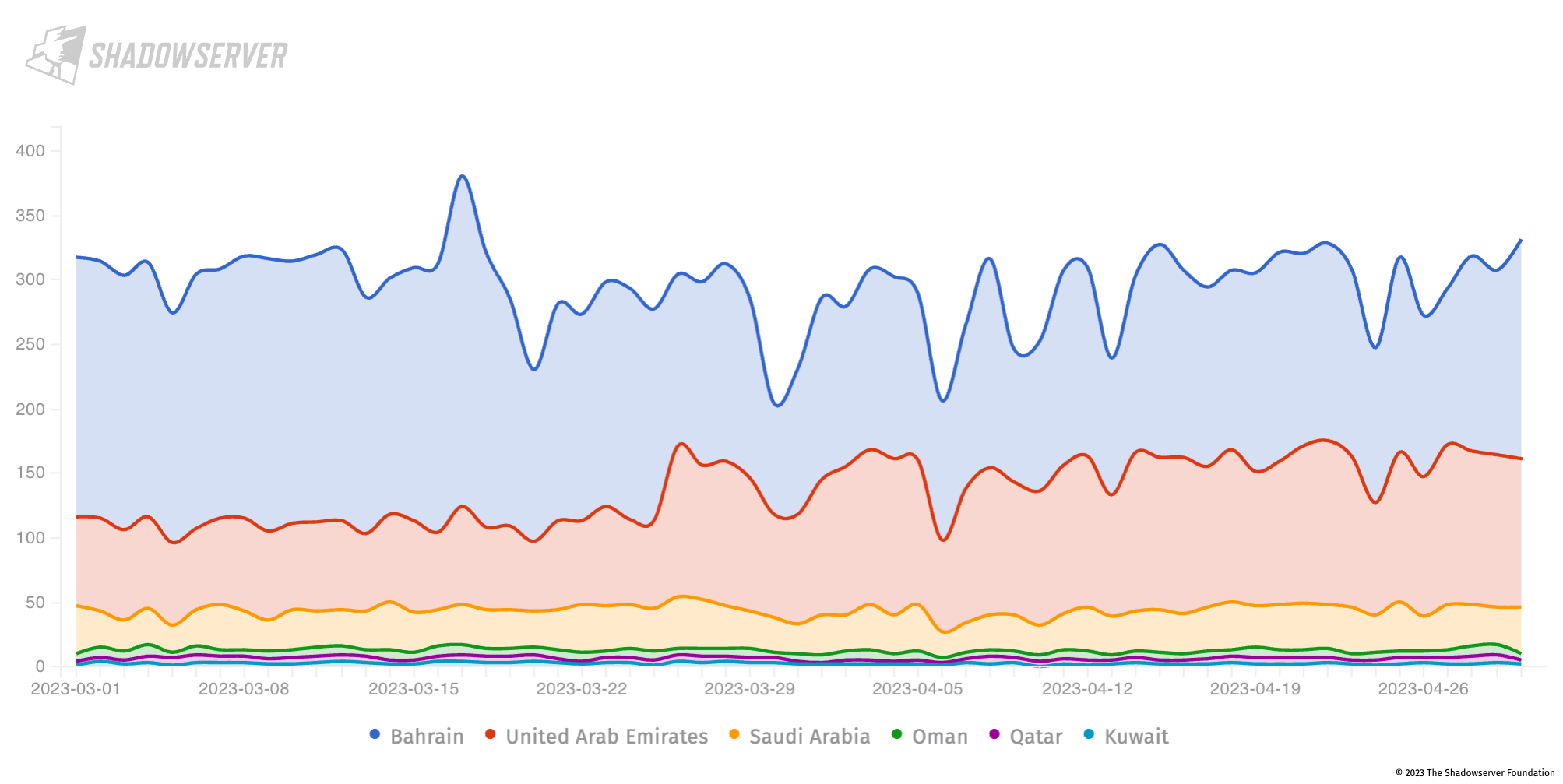
Exposed Git config instances in the Gulf (daily scan results from 2023-03-01 to 2023-04-30), Y-axis is unique IP address count
We also scan for critical vulnerabilities in Microsoft Exchange servers at risk from remote code execution. These include:
CVE-2022-41082 and CVE-2022-41040 (collectively known as ProxyNotShell), affect Microsoft Exchange Server 2013, 2016, and 2019. When combined, they allow an authenticated attacker to interact with the Microsoft Exchange Server Powershell backend and remotely execute code.
At the end of April 2023, there were still around 58K likely vulnerable Microsoft Exchange servers worldwide.
In the Gulf Region, the overall numbers are much smaller. The UAE has the highest number of vulnerable Microsoft Exchange servers, with an average of 400-450 devices detected daily for this reporting period as shown in the diagram below:
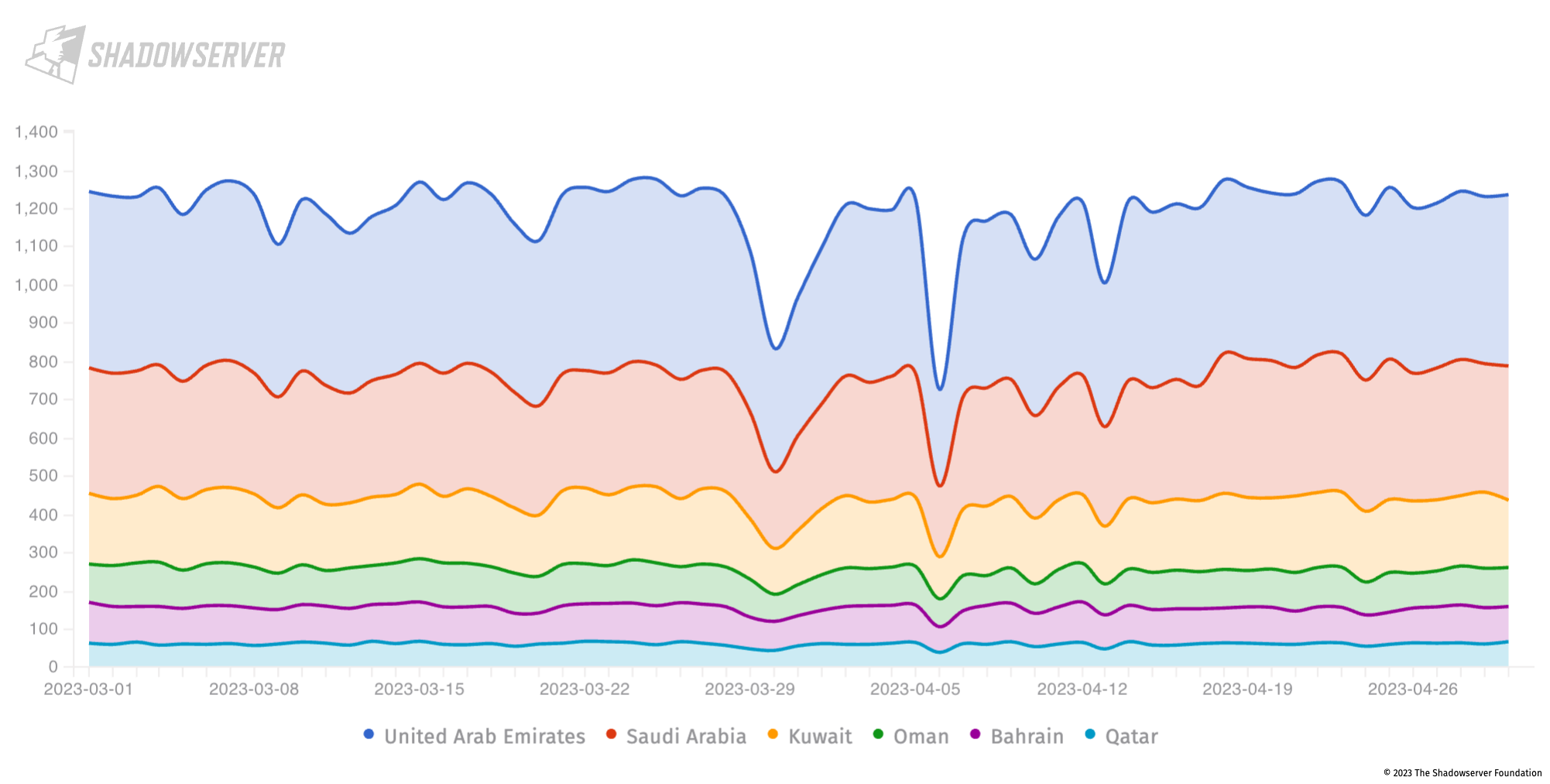
Vulnerable Microsoft Exchange instances in the Gulf (daily scan results from 2023-03-01 to 2023-04-30), Y-axis is unique IP address count
We share actionable, detailed and IP-specific vulnerable HTTP (covering, amongst others, the above Fortinet, git config and Jenkins vulnerabilities) and vulnerable Microsoft Exchange servers in your network/constituency in our daily Vulnerable HTTP and Vulnerable Exchange reports.
Note that new CVE vulnerability scans are continuously added to our Vulnerable HTTP report, and we recommend all affected National CSIRTs and network owners in the Gulf prioritize remediation of issues from our Vulnerable HTTP and Vulnerable Exchange reports.
Aside from HTTP-related vulnerabilities, it is also important to keep track of critical vulnerabilities related to other protocols. We scan for many of those as well. A recent example is an SNMP-related CVE-2017-6736 vulnerability in Cisco routers which, while old, is known to have been recently abused by APT28 – as reported by the UK NCSC in “APT28 exploits known vulnerability to carry out reconnaissance and deploy malware on Cisco routers” (see also our blog UK/US Joint Announcements Remind Us That Un-Remediated Vulnerabilities Snowball). Remediation advice can be found from Cisco. On 2023-05-16 we observed 136 routers in the Gulf Region that were still vulnerable to CVE-2017-6736:
Cisco routers by unique IP address vulnerable to CVE-2017-6736 (on 2023-05-16)
Finally, it is worth taking a step back to see the general statistics of services with either vulnerabilities, misconfigurations or simply being unnecessarily exposed in the Gulf Region.
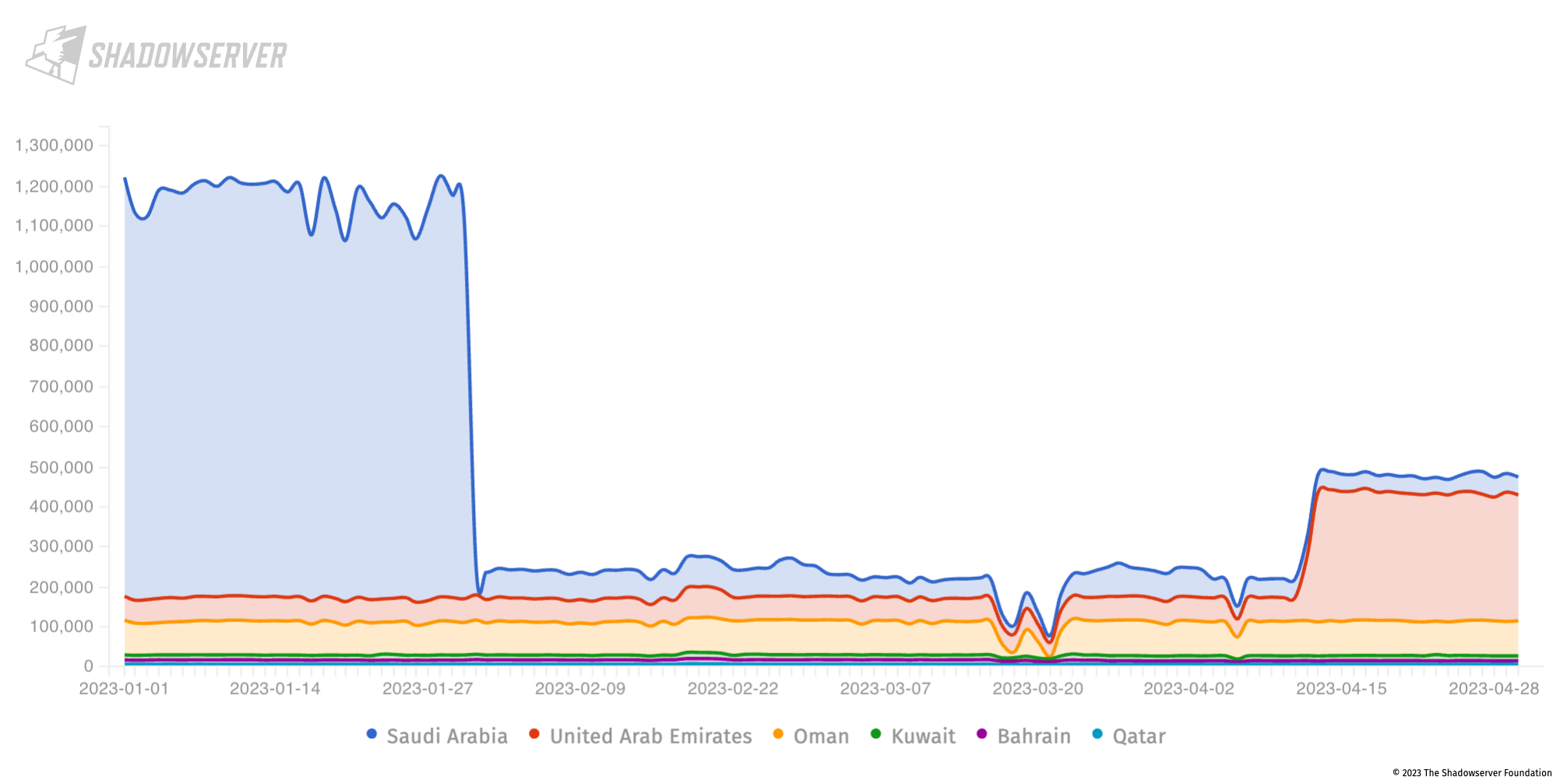
Vulnerable, abusable, misconfigured or otherwise unnecessarily exposed services in the Gulf (2023-01-01 to 2023-04-30), Y-axis is unique IP count
We see a sharp drop at the end of January (less CWMP service exposure on Huawei devices in Saudi Arabia), and then a sharp rise in Middlebox exposure in the UAE that can be abused for DDoS. Shown individually:
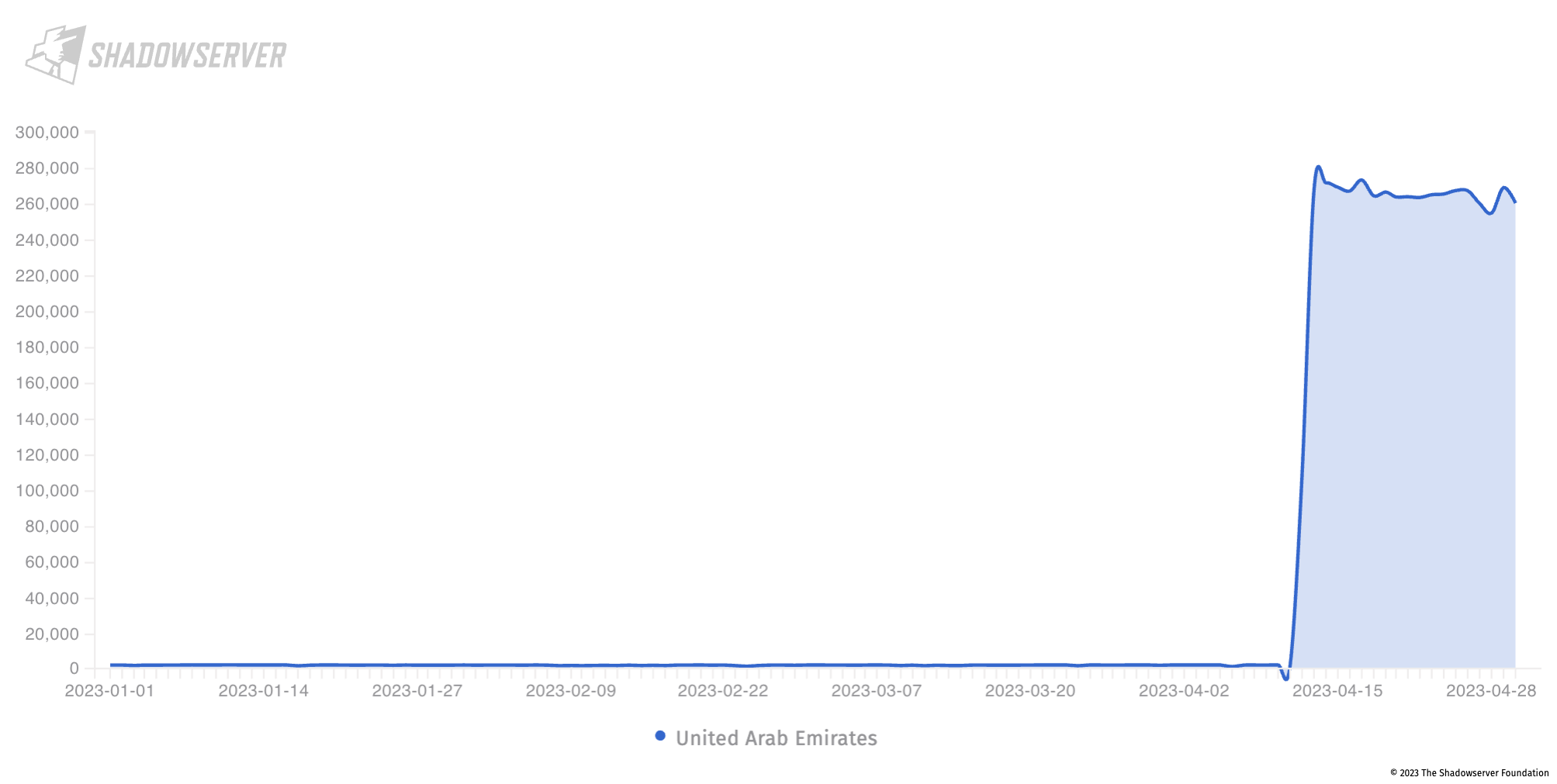
Middlebox exposure in the UAE (2023-01-01 to 2023-04-30), Y-axis is unique IP address count
You can read about how this Middlebox vulnerability can be abused in our previous blog post: Over 18.8 million IPs vulnerable to Middlebox TCP reflection DDoS attacks.
Infected (Attacking) Devices
Shadowserver also attempts to identify devices which are detected attacking our honeypot sensors (and which attempt to utilize the sensor to perform Distributed Denial of Service (DDoS) attacks). You can track these attacks on our Dashboard (updated daily), and filter by country as well.
Looking at attacks coming from infected devices in Kuwait, we observe a number of HTTP scan and brute force attacks being received from infected DVR and IP telephony systems.
The most common attacking device seen from Bahrain runs an embedded (presumably vulnerable) Boa webserver. Boa webserver development was discontinued in 2005(!), but continues to be used by multiple manufacturers. For more background on Boa related attacks, see the Microsoft article “Vulnerable SDK components lead to supply chain risks in IoT and OT environments”. We also see attacks from infected Fortinet and DrayTek devices.
MikroTik is the most common infected device seen in the UAE which is used in DDoS, HTTP and brute force type scans against our honeypots, with Ubiquiti, DrayTek and Fortinet Fortigate device infections in lower volumes.
We see infected MikroTik devices used in DDoS attacks in Saudi Arabia. We also see Huawei Home Gateway infected devices conducting both brute-force attacks and DDoS attacks.
In addition, we see infected Fortinet/Fortigate devices performing DDoS attacks from Oman.
Qatar shows similar attack vectors. Our observations highlight Fortinet/Fortigate brute force attacks and MikroTik DDoS related activity. Attacks are also observed from compromised Hikvision devices.
Exploited CVEs
Shadowserver tracks Common Vulnerability Exposure (CVE) exploitation attempts in the region and the world, primarily focusing on exposed HTTP resources. CVE signatures supported by our sensors were also enhanced as part of the recent FCDO-funded project, with a focus on CVEs being used in attacks against resources in the region.
For the reporting period of our project (March 1st to April 30th 2023), we saw a low frequency of exploits from sources in the region attacking our sensor network.
Overall, the most common CVE exploitation attempt seen originating from each Gulf country is CVE-2017-17215 (which targets Huawei HomeGateway devices). This is an old CVE used in many Mirai-like botnets.
Other notable exploits used in attacks against our sensor network (again at low frequency) can also be seen from Kuwait using EDB-41471, a MVPower DVR Remote Code Execution (RCE) exploit and CVE-2016-10372, and RCE in the Eir D1000 modem that is seen most frequently from the UAE.
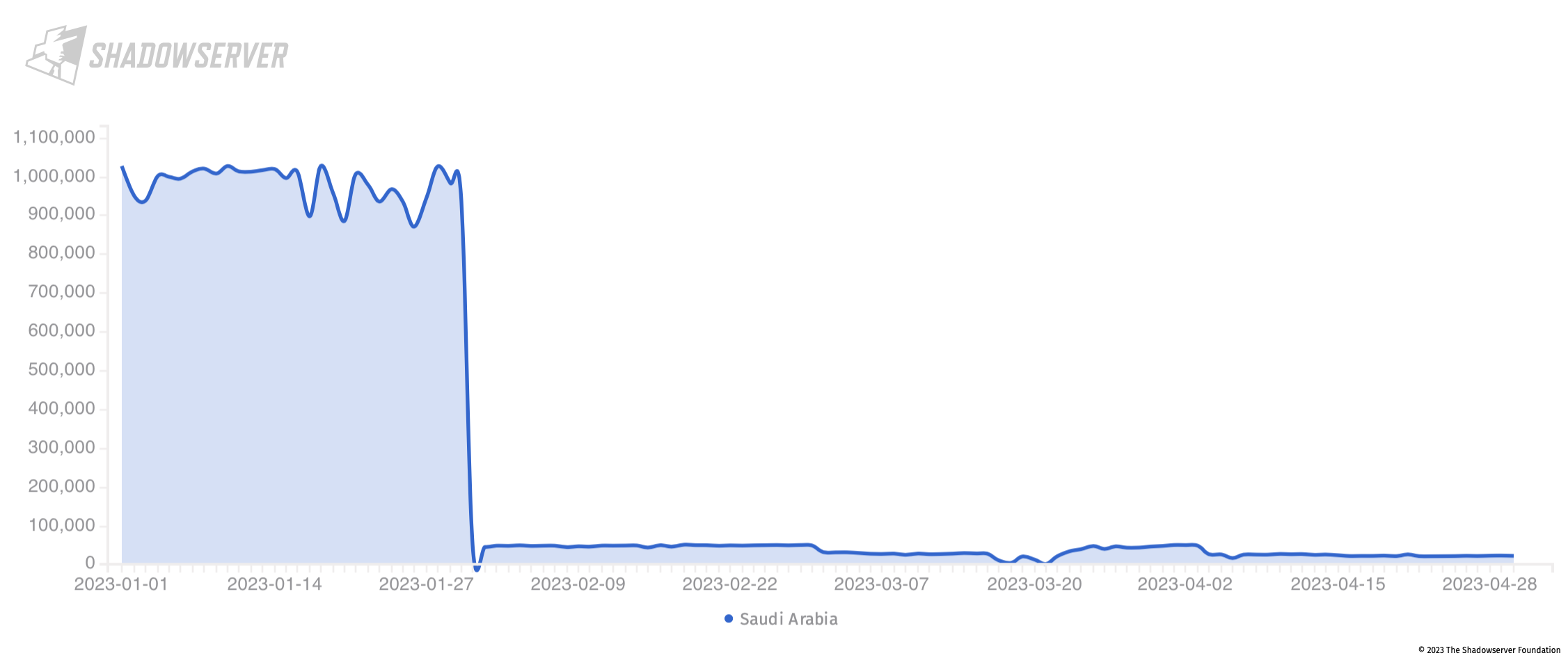
Improvements in Saudi Arabia attack surface exposure
It is particularly worth highlighting improvements in the general attack surface exposure posture of Saudi Arabia, at least seen from our own daily scan perspective. Previously – at the start of 2023 – Saudi Arabia had a very high exposure of Huawei devices (over 800k devices observed per day), which dropped significantly at the start of February. Overall the public exposure of Huawei devices in Saudi Arabia continued to drop steadily after the initial sharp drop:
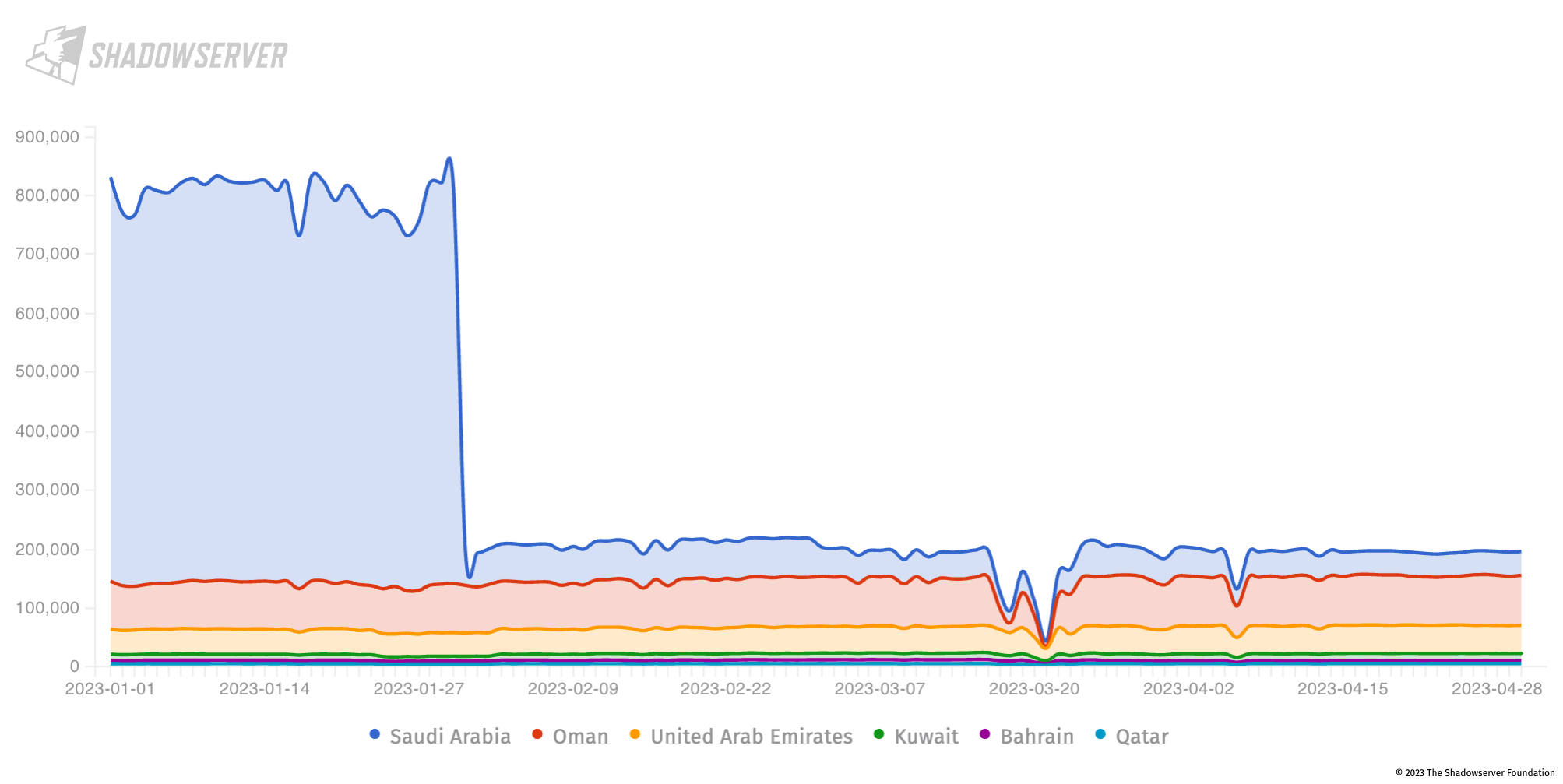
Device exposure over time in the Gulf, with large drop seen for Saudi Arabia. Y-axis shows unique IP address count
Summary
Overall, we see a relatively small amount of infrastructure in the Gulf Region being publicly exposed (compared to some other regions globally). Nevertheless, we observe some critical vulnerabilities (allowing for remote code execution), which can serve as potential points of entry for ransomware and APT actors into organizations’ networks. We note a steady improvement in the attack surface exposure in Saudi Arabia, as well as a reminder from the UAE that sometimes changes are made on a large scale that can have a potentially negative impact on the security posture of a country (the exposed Middlebox devices described above).
We hope that our observations demonstrate that it is possible to obtain a view into the exposed Internet infrastructure of a country or region, not just on exposed services, but on the actual (vulnerable) device makeup. This device makeup can have an impact on Internet defenders (and, of course, attackers). Some of the devices may not need to be made accessible to external queries from the public Internet. Exposing them unnecessarily in this way may pose additional security risks, which we have also illustrated specifically for the selected countries. Obtaining situational awareness about the vendor makeup of externally accessible devices on a network of responsibility may allow for a more efficient response and patch roll out, should any vulnerabilities be announced in these devices. Additionally, National CSIRTs that wish to be more proactive should particularly focus on mitigating the exposed attack surface caused by the known vulnerable devices, which may be continuously compromised by multiple threat actors and used for staging other types of potentially more serious attacks.
All the data discussed in the article is shared daily for free with National CSIRTs in the Gulf Region and beyond, as well as with specific network owners/operators that have subscribed directly to Shadowserver’s public benefit services.
If you have not yet done so, please sign up for our free daily threat feeds that will provide you with specific, actionable IP information about threats or vulnerabilities seen on your network(s). These will be filtered for your networks/domains or constituency (or country, for National CSIRTs).
Please also consider joining our Alliance, which will provide you with additional insights, details into threats that we see and other benefits (as well as helping to ensure financial sustainability for all of Shadowserver’s free public benefit services).
For any questions, please contact us.
We would like to thank the UK FCDO for their continued support, in line with the UK National Cyber Strategy – Pillar 4, Objective 1: to strengthen the cyber security and resilience of international partners.