More Free Cyber Threat Intelligence For National CSIRTs
April 25, 2022
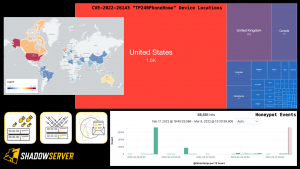
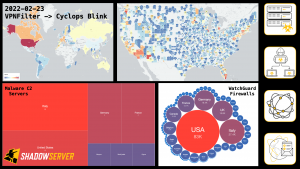
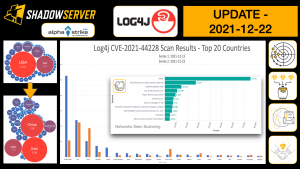
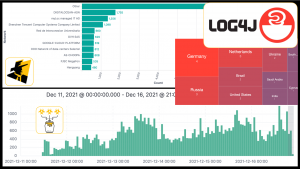
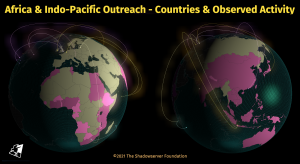
The UK FCDO have been supporting The Shadowserver Foundation's efforts to provide more free, actionable, daily Cyber Threat Intelligence to National CSIRTs in Africa and the Indo-Pacific. After making some great progress over the past year, we are seeking support from the community to engage some additional countries in the region. Can you help connect us, and the Internet more secure for everyone?