UK/US Joint Announcements Remind Us That Un-Remediated Vulnerabilities Snowball
April 20, 2023
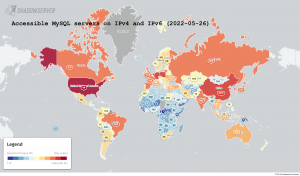
The UK’s National Cyber Security Centre (NCSC) and the US Cybersecurity and Infrastructure Security Agency (CISA) issued an alert on nation-state sponsored exploitation of router infrastructure. The alert calls out SNMP public exposure and one vulnerability in particular - CVE-2017-6742 - which relates to a long known “remote code execution” opportunity on certain Cisco routers. This alert is a timely reminder for all with unpatched equipment to think broadly! We use this opportunity to highlight our data and free daily reports that provide information on the SNMP and Cisco device exposed attack surface (and more!).