Accessible Radmin Report - Exposed Radmin Services on the Internet
July 7, 2020
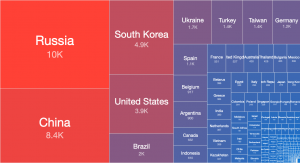
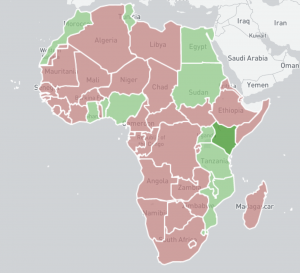
We have recently enabled a new IPv4 Internet-wide scan and report for accessible Radmin services on port 4899/TCP. Radmin is a remote access software product commonly in use today. Our daily scans uncover around 50,000 accessible Radmin services on port 4899/TCP. While Radmin is in general considered a secure mechanism for remote access, care should be taken as with all similar types of services to ensure no misconfiguration has taken place.