The Data Center Move - All the Gory Details and Extras
October 16, 2020
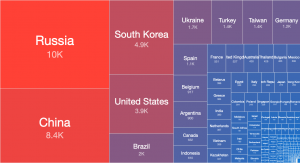
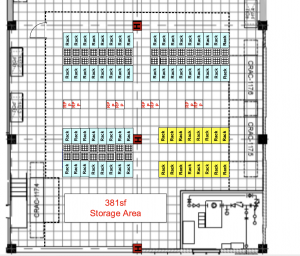
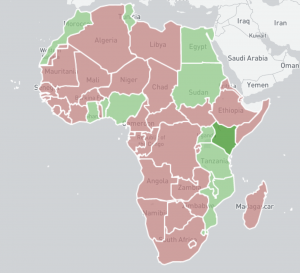
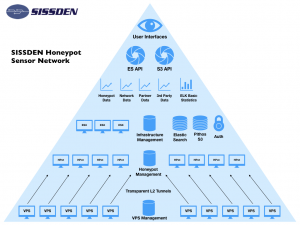
As everyone knows now, Shadowserver had a bit of a funding issue earlier this year which caused us to go through the process of needing a new space for our data operations. A place to call home for all that storage and computing that we do daily. A new data center was required. This story will go through that recent history, the actual move, and a few after action and post move things that occurred. This blog will be partially serious, some tongue in cheek, and some sad comedy, so enjoy our journey.