Introduction
We have recently started to perform a full IPv4 Internet-wide scan for accessible SMTP services and will report out possible vulnerabilities that have been observed, with a current focus on Exim (in the future non-Exim vulnerabilities may be added). We scan by performing a connection to port 25, recognizing an SMTP response and collecting the banner served. These connections look just like a normal SMTP connection, there is not any attempt to exploit the port, only to collect the banner information from that connection to the server.
The scans were inspired by the recent Qualys Security Advisory 21Nails: Multiple vulnerabilities in Exim. This advisory identified 21 vulnerabilities (from CVE-2020-28007 to CVE-2020-28026, plus CVE-2021-27216) for a total of 11 local vulnerabilities, and 10 remote vulnerabilities.
To share results of the scan, we have created two new reports:
- Vulnerable SMTP report – a default report that includes a list of all vulnerable Exim SMTP servers identified (and in the future other SMTP vulnerabilities)
- Accessible SMTP Report – an optional report that includes results of all SMTP servers seen regardless of vulnerability state (a population scan)
Vulnerable SMTP report
As of 2021-05-18, the Vulnerable SMTP report contains a list of vulnerable Exim servers found through our scans, based on vulnerable Exim version information as provided in the Qualys Security Advisory 21Nails: Multiple vulnerabilities in Exim. In the future we will add additional vulnerabilities as well, not necessarily Exim related.
This report contains information on services with the following Exim vulnerabilities:
- 21nails – the vulnerability set uncovered by Qualys
- CVE-2020-28020 (unauthenticated RCE as “exim”, in Exim < 4.92), also covered by the 21nails Qualys advisory but distinctly tagged.
Please note: The above information is based on banner version information collected during the SMTP scan, hence there is a possibility of False Positive reports. If you believe a report is a False Positive, please let us know along with the details of the SMTP server/patch in question.
The report excludes Ubuntu Exim versions >= 4.82 and Debian Exim versions >= 4.89 as it is not possible to determine based on the banner whether the following patches below have been applied:
The following tables shows example tag mappings that are applied (aside from Ubuntu Exim versions >= 4.82 and Debian Exim versions >= 4.89):
| Banner | Tag |
|---|---|
| ESMTP Exim 4.94.2 (not vulnerable) | smtp |
| ESMTP Exim 4.94.0 | smtp;21nails |
| ESMTP Exim 4.92 | smtp;21nails |
| ESMTP Exim 4.91 and lower | smtp;cve-2020-28020 |
All Exim versions below 4.94.2 are potentially vulnerable (with possibly the Ubuntu and Debian exceptions if not patched).
Vulnerable Exim 21nails Results overview
On 2021-05-18 our scan uncovered 317,848 distinct IPs that are likely vulnerable based on the connected banner identification.
Using the above criteria, the following is a country-level breakdown of vulnerable Exim IPs (distinct IPs found vulnerable to 21nails – including CVE-2020-28020):
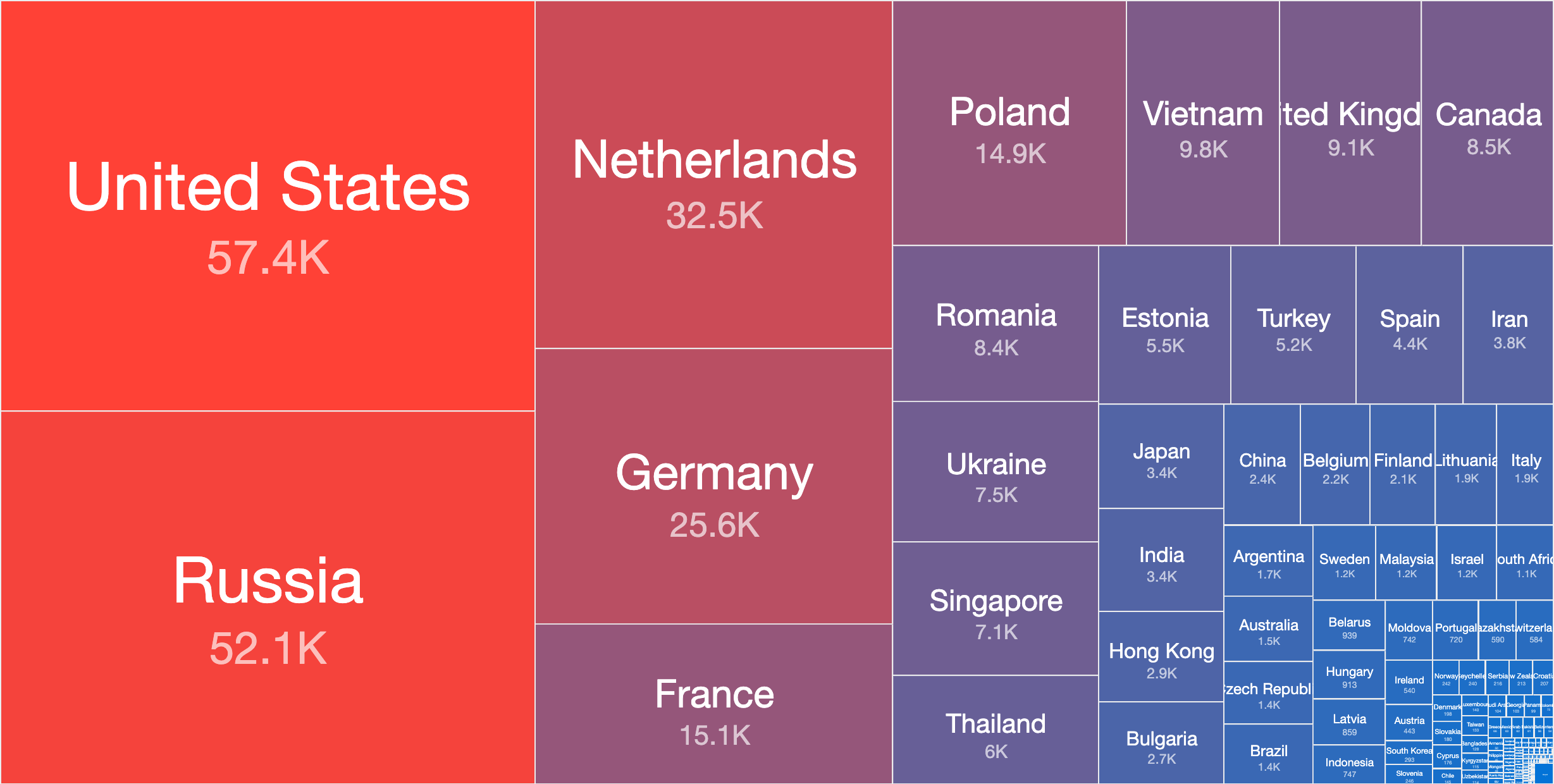
Top Countries with Vulnerable Exim Servers (by distinct IPs) – 2021-05-18
The following is a Top 20 list of vulnerable versions detected:
| Exim Version | Count |
|---|---|
| 4.94 | 95973 |
| 4.92.3 | 37407 |
| 4.92 | 34400 |
| 4.89 | 30267 |
| 4.93 | 26359 |
| 4.84 | 16598 |
| 4.93.0.4 | 11164 |
| 4.92.2 | 8324 |
| 4.91 | 8265 |
| 4.80 | 6300 |
| 4.90 | 5914 |
| 4.72 | 5774 |
| 4.87 | 4914 |
| 4.76 | 3698 |
| 4.80.1 | 2658 |
| 4.69 | 2282 |
| 4.82 | 2245 |
| 4.92.1 | 1680 |
| 4.77 | 1415 |
| 4.85 | 1411 |
Patch your Exim Servers!
If you need to run an Exim server exposed to the Internet, make sure to patch to the latest version that fixes the above vulnerabilities: 4.94.2.
The following table provides an overview of Linux distributions with the fixed minimal patch versions:
| Vendor | Fixed version (minimal) |
|---|---|
| Centos | 4.94.2-1.el8 |
| Debian | 4.89-2+deb9u8 |
| Fedora | 4.94.2 (see Red Hat) |
| Gentoo | 4.94.2 |
| Red Hat | 4.94.2 |
| SUSE | 4.94.2-lp152.8.3.1 |
| Ubuntu | 4.82-3ubuntu2.4+esm3;4.86.2-2ubuntu2.6+esm1 |
OPTIONAL: Accessible SMTP Report
Another new report we have created is the Accessible SMTP Report. This report is optional – you need to explicitly request to have it delivered daily to you. This report enumerates all hosts running SMTP on port 25 and the collected SMTP banners. It is similar to our Accessible HTTP Report, Accessible QUIC Report, Accessible SSH Report, and Accessible SSL Reports where we collect all the services from these protocols looking for other issues and vulnerabilities giving us the total list of devices with those protocols running. These are all different optional reports that can be signed up for at any time as a part of our free service.
On 2021-05-18 our IPv4 Internet-wide scan uncovered 5,208,709 distinct IPs responses.
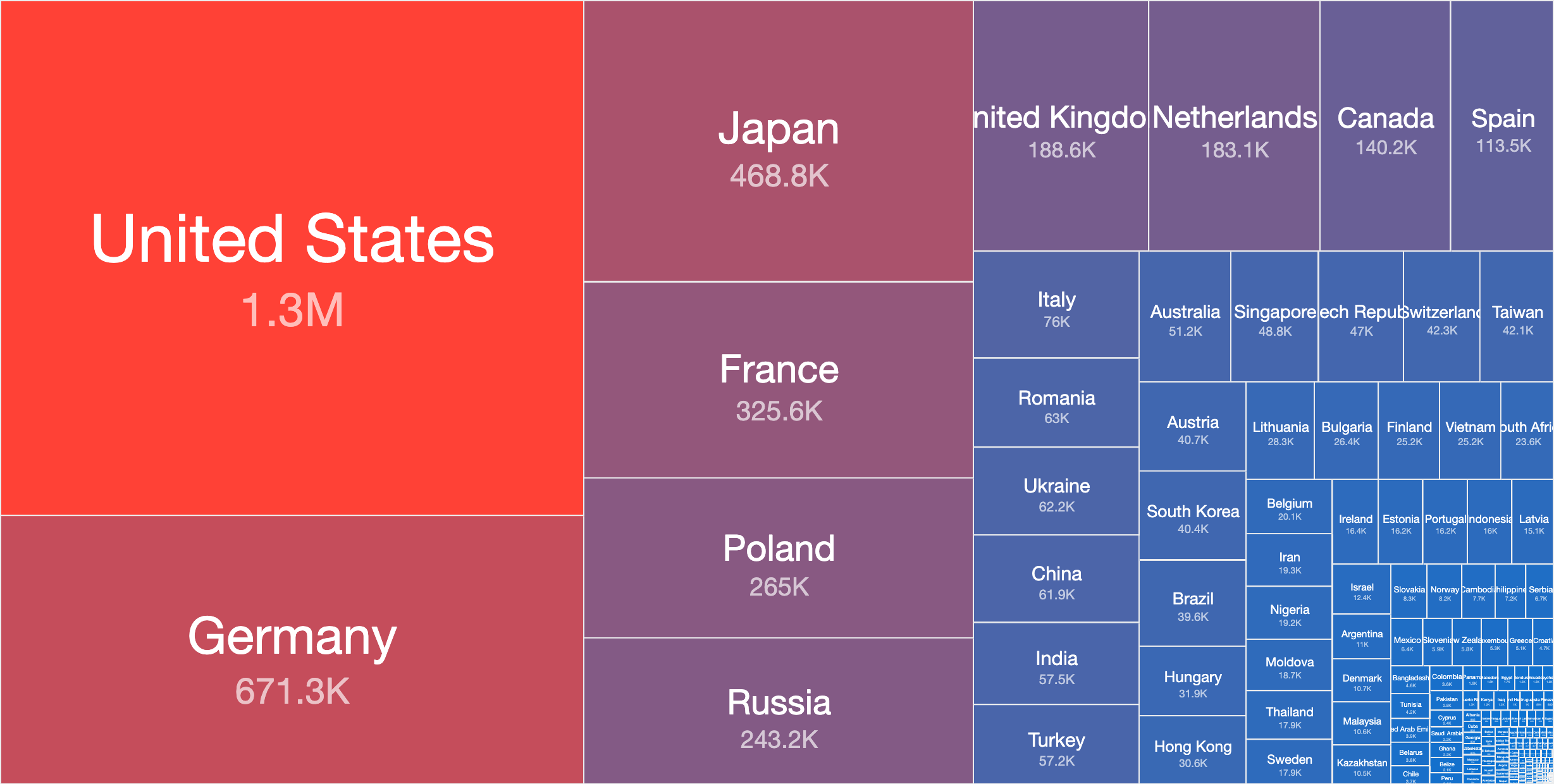
Top Countries with exposed SMTP services (by distinct IPs) – 2021-05-18
Subscribe to the new reports!
Details about the format of the new reports being shared can be found in the Vulnerable SMTP report page and Accessible SMTP Report page. All existing Shadowserver report subscribers are now automatically receiving the Vulnerable SMTP report, if any potentially vulnerable SMTP (currently Exim only) services are identified within their networks and countries (for national CSIRTs). If you are an existing subscriber and would like to receive the optional Accessible SMTP Report please send us a request via our contact page.
If you are not already a subscriber to Shadowserver’s public benefit daily network reports and would like to receive this new report and our other existing report types (covering not just other scan results, but observations from sinkholes, honeypots, darknets, sandboxes, blocklists and other sources), then please sign up to our free daily public benefit network remediation feed service.
If you have any questions or comments on the new reports, please contact us.

