LAST UPDATED: 2021-06-07
LEGACY REPORT
Report discontinued. Replaced by: Honeypot Amplification DDoS Events Report
This category of DDoS attacks utilizes UDP-based, open, amplifiable services to reflect packets to a victim, by spoofing the source IP address of the packets sent by the amplifier to the victim’s IP address.
Depending on the protocol and type of open services abused, the size of the original packet content sent by the attacker can be amplified in the service response multiple times (even by a factor of hundreds), flooding the victim with packets and enabling DDoS.
Honeypots that emulate open and amplifiable services can be used to detect this kind of abuse. However, as the source of these attacks is spoofed to the victim address, it is possible only to report on victims being abused, not on the source of the DDoS.
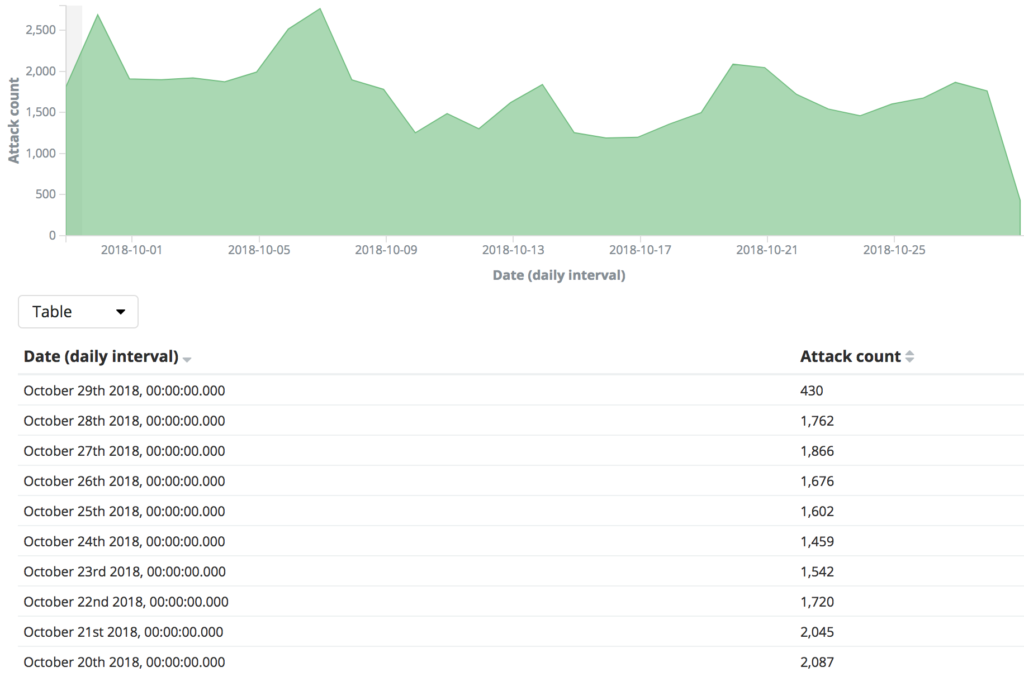
The chart below illustrates the scale of these types of amplificable DDoS attacks in Europe, based on SISSDEN data. Looking back from 29th October over the prior 30 days, over 53 000 attacks have been observed against over 36 000 victims with IP space in Europe, with open NTP (port 123/udp), DNS (port 53/udp) and chargen (port 19/udp).
You can read more about our DDoS attack observations in the SISSDEN blog entry on observations on DDoS attacks in 2018. For more insight into how amplifiable DDoS attacks work, check out this writeup and paper by Christian Rossow, as well as the US-CERT Alert (TA14-017A).
The Amplification DDoS Victim report we send to subscribers includes the IP that is being targeted (i.e., the victim), information about the type of service being abused for the DDoS, DDoS start times, end times if available, and request used if available.
This report type was enabled as part of the EU Horizon 2020 SISSDEN Project.

