On Tuesday October 13th 2015, the UK National Cyber Crime Unit (part of the National Crime Agency) in conjunction with the FBI and US Department of Justice jointly announced an ongoing operation to take down the Dridex botnet (also known as Bugat/Cridex/Feodo). Due to the large dollar value losses involved, that high profile story attracted significant media attention.
The Shadowserver Foundation closely supported this operation during 2014-2016, providing operational infrastructure and technical support to law enforcement, and gathering data on infected clients for the purposes of victim notification and remediation. Our public data about the operation was made available at that time via dridex.shadowserver.org.
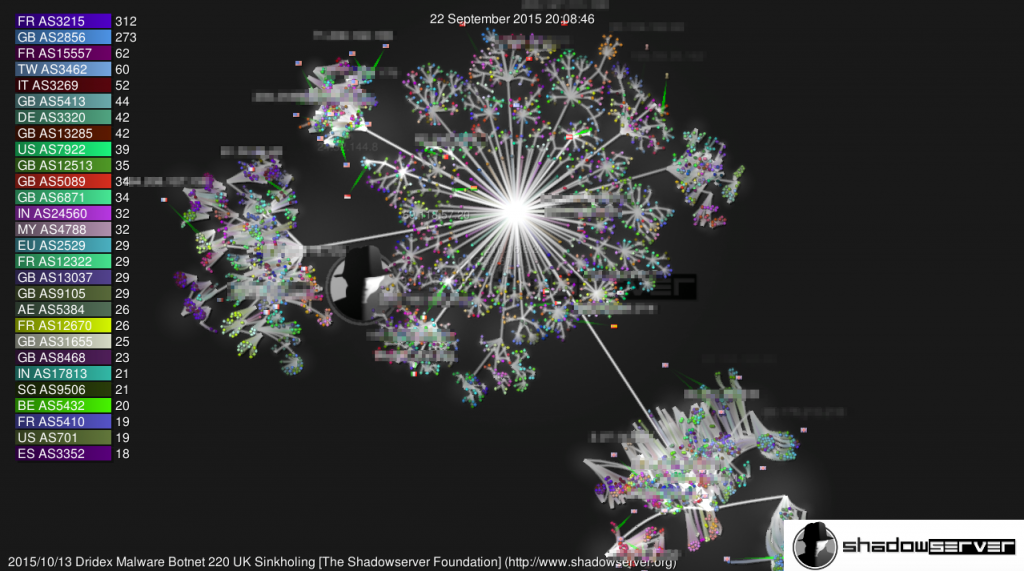
Example 2015 real time visualization of UK victims of Dridex botnet 220:
Over the following year, Shadowserver worked with National CERTs/CSIRTs and network owners globally to successfully remediate as many infected victim computers as possible.
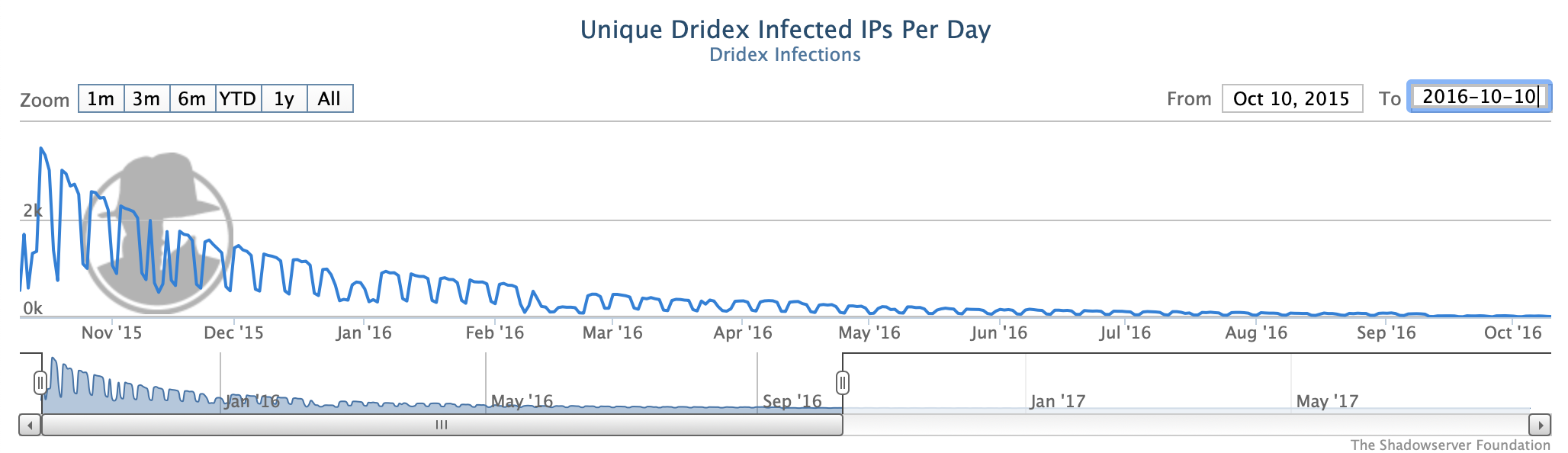
Our Dridex sinkhole statistics for October 2015 to October 2016 show that these international efforts followed a fairly typical botnet victim remediation profile, with most of the victim computers being identified and disinfected relatively quickly, but then there was an extended 6-12 month long tail before the full victim clean up was fully complete:
In February 2017, after being extradited from Cyprus to the US, Moldovan national Andrey Ghinkul, aka “smilex”, pleaded guilty to distributing Dridex malware and was sentenced in December 2018 for his part in the criminal enterprise.
As an update to this legal action, on December 5th 2019, the US Department of Justice and UK National Crime Agency (NCA) announced the unsealing of criminal charges against other actors alleged to be behind the Dridex botnet’s activities, via an organization that was self described as “Evil Corp”.
The US State Department, in partnership with the US Federal Bureau of Investigations (FBI), also announced a reward of up to $5 million under the Transnational Organized Crime Rewards Program for information leading to the arrest and/or conviction of the alleged ringleader Maksim V. Yakubets, aka “aqua”. This represents the largest such reward offer for a cyber criminal to date.
The previous FBI record was $3 million, for information leading to the arrest and/or conviction of Evgeniy Mikhailovich Bogachev, aka “slavik”, for his alleged role in the operation of the Gameover Zeus botnet. For more information on Gameover Zeus see Shadowserver’s previous sinkholing coverage.
Also unsealed on the same day were charges against Igor Olegovich Turashev aka “Enki”, “Parasurama”, “Nintutu”, “Vzalupkin”, “Tigrr” and “Tigrruz”.
One of the most pleasing elements of this case is the degree of successful international public/private cooperation that has been required. Truly international, complex cybercime cases such as this deserve thoughtful and meaningful cooperation, coordination and tenacity. This is a long running criminal case that has been doggedly investigated since the botnet was initially disrupted. The official DoJ and NCA reporting hints heavily to this, including further details in the publicly released indictment documents:
Once again, the ongoing story has attracted significant media coverage, which has unsurprisingly sometimes focused on the suspect’s apparent lavish, high spending lifestyles:

It will be interesting to see what impact the latest round of US legal actions have on the criminal community, and on the ongoing activities associated with Dridex malware that are still being observed in the wild today.