Introduction
On Monday June 2nd 2014, the US Department of Justice announced an ongoing operation to take down the infamous Gameover Zeus and CryptoLocker cybercrimal botnet infrastructures. “Operation Tovar” is a joint effort between international law enforcement agencies, such as the FBI, UK NCA and Europol/EC3, plus multiple private partners. The actual botnet take over occurred on Friday May 30th 2014 and is still ongoing as an active operation. The Shadowserver Foundation has participated by providing operational infrastructure and gathering data on infected clients for the purposes of victim notification and remediation.
Bot Description
Gameover Zeus is based on the popular 2007+ Zeus credential stealing trojan (for which the source code was leaked in May 2011). It was modified in September 2011 to incorporate Peer 2 Peer (P2P) communications, to attempt to decentralize the command and control (C&C/C2) infrastructure and make the botnet harder to take down. It includes a fallback Domain Generation Algorithm (DGA) in case communication with the P2P network is lost. It also incorporates advanced features, such as RSA-2048 digital signatures for critical C2 activity, as well as using RC4 encryption, layers of chained peers as data exfiltration proxies, plus anti-poisoning and auto blacklist features. Unusually, the P2p Zeus network is a single centralized P2P botnet, although it can be sub-divided into sub-botnets based on BotIDs and controlled by different sub-botmasters.
Gameover Zeus is often spread by spam/phishing emails, usually delivered by the Cutwail botnet. It had become widely distributed and has been used for financial crimes targeting several hundred different banks – both by stealing ordinary credentials and also in real-time hijacking of bank accounts. However, it can also be used for activities as diverse as malware dropping, DDoS attacks, stealing Bitcoins or theft of Skype and other online service credentials.
CryptoLocker is ransomware that hijacks the infected computer and strongly encrypts the local data. It then demands a ransom that must be paid within a short time period in order to give the victim access to their own data. Currently there is no known method to decrypt the data without paying the ransom. CryptoLocker ransomware was being delivered using Gameover Zeus.
Reports
If you are already receiving our free nightly reports for your networks you will probably have noticed a new category called “Gameover Zeus”. This contains remediation data for all three components of the Gameover Zeus infrastructure:
- P2P layer peer communication entries – tagged “gameover-zeus-peer“
- HTTP proxy layer connections – tagged “gameover-zeus-proxy“
- Fallback DGA requests (to 1000 random domains per week in the .biz, .com, .info, .net, .org and .ru TLDs) – tagged “gameover-zeus-dga“
We will soon begin reporting out Gameover Zeus DNS activity and Cryptolocker infection information too (we are dependent on other third parties to fully activate these data feeds).
Charts
To get a better picture of the full extent of Gameover Zeus activity worldwide, you can find various types of statistics for the distribution of infected computers on our live Gameover Zeus statistics page.
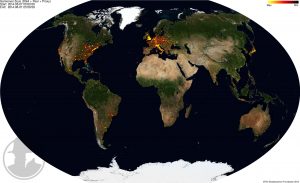
This is a heatmap of the world infections seen so far (click to enlarge):
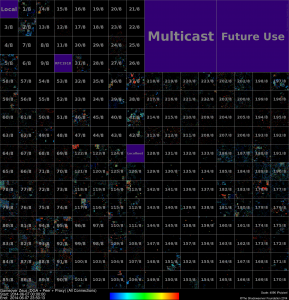
And, of course, our favorite Hilbert Curve (click to enlarge):
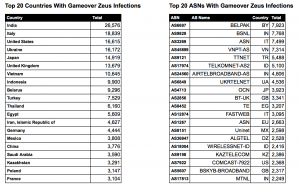
Top 20 Countries and ASN’s (click to enlarge):
The video below attempts to visualize the patterns of backup DGA HTTP traffic during the initial period of the Gameover Zeus botnet takedown. It shows how infected hosts in many countries began contacting our sinkhole webservers once the malicious domains in the .biz, .com, .info, .net, and .org TLDs were seized by law enforcement and pointed at the sinkhole (flags show the IP-geolocation of the infected host, their title is the malicious DNS domain they were attempting to contact, while the tree branches are based on country code, then ASN, then color coded IP octets):
End User Remediation
You can check if your computer is infected with Gameover Zeus by visiting this page:
https://goz.shadowserver.org/gozcheck/
US CERT provides a useful summary of mitigation tools for infected end users:
https://www.us-cert.gov/ncas/alerts/TA14-150A
More Information
New articles covering the threats:
- https://krebsonsecurity.com/2014/06/operation-tovar-targets-gameover-zeus-botnet-cryptolocker-scourge/
- https://www.secureworks.com/research/zeus
- http://www.crowdstrike.com/blog/gameover/index.html
- http://www.bleepingcomputer.com/virus-removal/CryptoLocker-ransomware-information
- http://nakedsecurity.sophos.com/2013/10/18/CryptoLocker-ransomware-see-how-it-works-learn-about-prevention-cleanup-and-recovery/
Notes
The Shadowserver Foundation is a non-profit organization that provides infection notification and remediation information for many types of computer security threats. If you are a hosting provider, internet provider or a CERT with a constituency you can sign up to receive free nightly reports on your networks.