Over 60,000 Exchange servers vulnerable to ProxyNotShell attacks
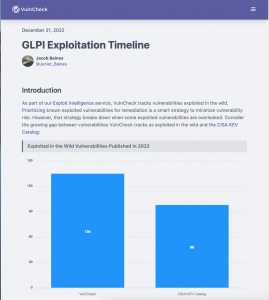
More than 60,000 Microsoft Exchange servers exposed online are yet to be patched against the CVE-2022-41082 remote code execution (RCE) vulnerability, one of the two security flaws targeted by ProxyNotShell exploits. According to a recent tweet from security researchers at the Shadowserver Foundation, a nonprofit organization dedicated to improving internet security, almost 70,000 Microsoft Exchange servers were found to be vulnerable to ProxyNotShell attacks according to version information (the servers’ x_owa_version header). However, new data published on Monday shows that the number of vulnerable Exchange servers has decreased from 83,946 instances in mid-December to 60,865 detected on January 2nd. These two security bugs, tracked as CVE-2022-41082 and CVE-2022-41040 and collectively known as ProxyNotShell, affect Exchange Server 2013, 2016, and 2019.