VulnCheck State of Exploitation 2026
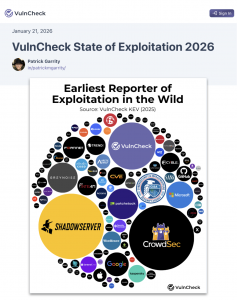
In 2025, VulnCheck identified 884 Known Exploited Vulnerabilities (KEVs) for which evidence of exploitation was observed for the first time. Our analysis shows that 28.96% of KEVs in 2025 were exploited on or before the day their CVE was published, an increase from the 23.6% observed in our 2024 trends in exploitation report, highlighting the continued prevalence of both zero-day and n-day exploitation. 2025, exploitation evidence was first reported by over 100 unique organizations, including security researchers, cybersecurity vendors, and software suppliers. These trends demonstrate that exploitation speed remains consistently high year over year, and that defenders must prioritize visibility into exploited vulnerabilities with timely remediation in order to keep pace with attackers.
Transparency in exploitation disclosure is critical, as it enables consumers to better understand who first reported exploitation and to assess the level of trust they place in each source. Shadowserver remained the leading source for first-to-report exploitation evidence.