12,000+ KerioControl Firewalls Exposed to 1-Click RCE Attack
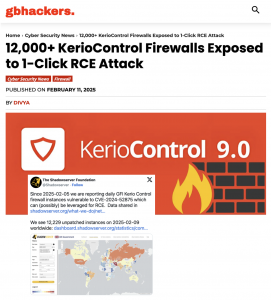
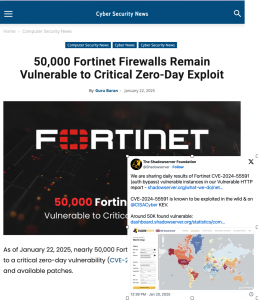
Cybersecurity researchers caution that over 12,000 instances of GFI KerioControl firewalls remain unpatched and vulnerable to a critical security flaw (CVE-2024-52875) that could be exploited for remote code execution (RCE) with minimal effort. The Shadowserver Foundation has been tracking this vulnerability and issuing daily reports since February 5, 2025.
A global heatmap published by Shadowserver highlights the widespread nature of the issue, showing unpatched devices across multiple countries. The Shadowserver Foundation is actively sharing data with network owners to help facilitate immediate remediation efforts.