Citrix Bleed exploit lets hackers hijack NetScaler accounts
This Monday, Citrix issued a warning to administrators of NetScaler ADC and Gateway appliances, urging them to patch the flaw (CVE-2023-4966) immediately, as the rate of exploitation has started to pick up.
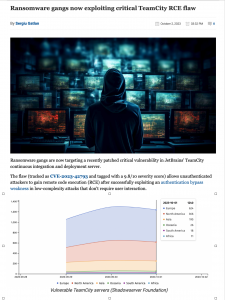
Today, researchers at Assetnote shared more details about the exploitation method of CVE-2023-4966 and published a PoC exploit on GitHub to demonstrate their findings and help those who want to test for exposure. Threat monitoring service Shadowserver reports spikes of exploitation attempts following the publication of Assetnote’s PoC, so the malicious activity has already started.
As these types of vulnerabilities are commonly used for ransomware and data theft attacks, it is strongly advised that system administrators immediately deploy patches to resolve the flaw.