Government Launches Automatic Alert Service for Vulnerabilities and Exposure in Cyberspace
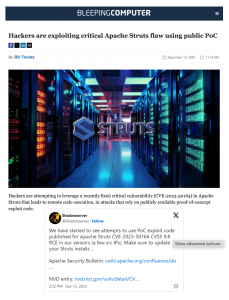
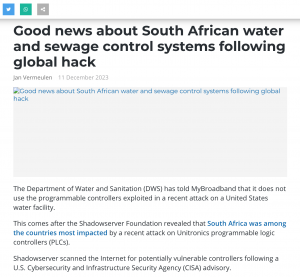
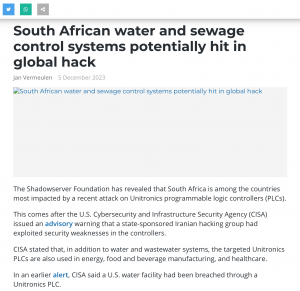
The Government, through the National Cybersecurity Center (CNCS), made an automatic notification service for vulnerabilities and exposure in cyberspace available to public and private entities. The new service, which is offered free of charge, aims to help organizations strengthen their cybersecurity and protect their digital assets to promote a safer, more reliable and resilient cyberspace, through timely notifications.
The resource, presented by the National Cyber Incident Response Team (CSIRT-RD), together with the Shadowserver Foundation, is aligned with the Digital Agenda 2030, our National Digital Transformation Strategy. The director of the CNCS, Juan Gabriel Gautreaux, explained that those interested in obtaining the service must subscribe by registering an official and authorized contact of the organization to which they belong and complete a form.