Since May 2016, The Shadowserver Foundation has been intensively participating in the three year EU HORIZON 2020 funded SISSDEN project, which involves setting up a large sensor network of honeypots, supported by darknet and other external sources of attack data collection. The primary objective of the SISSDEN project is the delivery of new free-of-charge victim remediation reports to the operational security community via The Shadowserver Foundation’s existing daily report sharing mechanism.
In the SISSDEN model, one sensor contains a number of tunneled IP address, on which we deploy a range of standardized, centrally managed honeypots of different types. As of mid April 2019, the H2020 SISSDEN project has successfully deployed 255 sensors (using 981 allocated IP addresses), distributed across 383 /24 address ranges, in 119 different ASNs and 58 countries. In total SISSDEN has 13 different types of honeypot types deployed in our sensors, supplemented by 3 project partner honeypot networks and 2 project partner darknet networks.
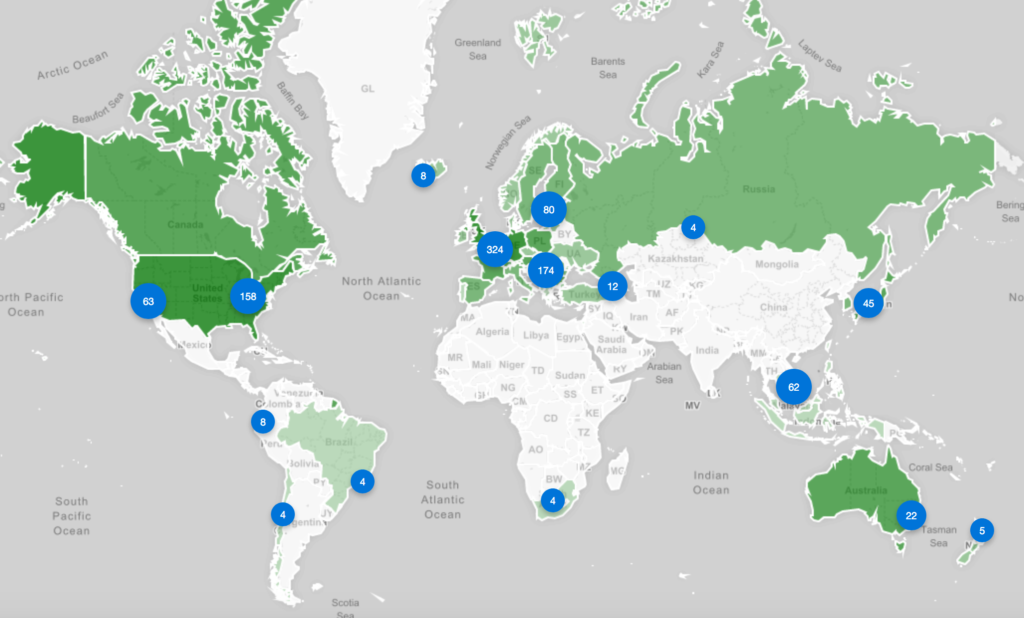
H2020 SISSDEN Global Sensor Distribution by IP Allocation Count (April 2019)
H2020 SISSDEN is offering 5 new report types, 4 of which are created from honeypot deployments and 1 from a network telescope (darknet) deployment. The full list of new SISSDEN reports sent out by The Shadowserver Foundation is as follows:
- The Brute Force report (on IPs performing brute force attacks coming primarily from IoT botnets)
- The HTTP Scanner report (on IPs performing HTTP-based scanning and/or exploitation)
- The ICS Scanner report (on IPs targeting ICS/SCADA protocol aware devices)
- The Amplification DDoS Victim report (on IPs that are victim of DDoS Amplification Attacks)
- The Darknet report (a darknet based report that fingerprints IPs exhibiting Mirai-like activity)
Additionally, an older Spam-URL report offered by Shadowserver that includes data from spam messages that have a URL embedded in them has also been enhanced with SISSDEN data.
As of mid April 2019, these reports have resulted in up to 31 million attack events being reported out by The Shadowserver Foundation. The reports now reach over 100 National CSIRTs and 4100+ network owners worldwide on a daily basis.
A more detailed architectural overview of the project is available on the SISSDEN project website.

