This unprecedentedly complex operation was the culmination of over four years of law enforcement and technical work, and impacted over twenty different malware families that utilized over 832,000 different DNS domains for Domain Generation Algorithms (DGAs) in 60 top level domains. Sinkhole data from the Avalanche platform is available each day in Shadowserver’s free of charge daily reports to national CERTs and network owners.
At that time, one individual malware family was excluded from that operation, to allow ongoing law enforcement investigations to continue. Victim remediation efforts are still ongoing for computers still infected with Avalanche related malware, with many victim computers still to be disinfected (you can find tools for disinfection here). So one year later, public and private international partners once again came together at Europol’s European Cybercrime Center (EC3) in a joint effort to extend their action against their existing targets and also target the previously excluded Andromeda botnet.
On 29 November 2017, the Federal Bureau of Investigation (FBI), in close cooperation with the Luneburg Central Criminal Investigation Inspectorate in Germany, Europol’s European Cybercrime Centre (EC3), the Joint Cybercrime Action Task Force (J-CAT), Eurojust and private-sector partners The Shadowserver Foundation, Microsoft, The Registrar of Last Resort, Internet Corporation for Assigned Names and Numbers (ICANN) and associated domain registries, Fraunhofer Institute for Communication, Information Processing and Ergonomics (FKIE), and the German Federal Office for Information Security (BSI), as well as law enforcement representatives from Australia, Austria, Belarus, Belgium, Canada, Finland, France, Italy, the Montenegro, Netherlands, Poland, Singapore, Spain, the United Kingdom and Taiwan, announced that they had dismantled one of the longest running malware families in existence – Andromeda (also known as Gamarue). At the same time, they also continued their existing legal and technical actions against over 848,000 Avalanche related command and control (C2) domains, to continue to protect existing victims and provide more time for any remaining victims to be identified and remediated.
The FBI began their investigation into the Andromeda banking trojan in 2015, and worked closely together with Microsoft on the case.
Andromeda was spread by spam or exploit kits and the victim population was estimated to exceed over one million computers infected per month. In addition to typical financial crime and data exfiltration, Andromeda was also sometimes used to download up to 80 other malware families onto infected victim computers. The main targets of the distributed malware were Asia, North America, Romania, Italy, Germany and Poland.
International investigations led the FBI to a suspect in Belarus, who was arrested by Belorussian law enforcement authorities on November 29th. During the search of his home, the investigators seized many data systems and storage media. In addition, law enforcement authorities have seized or shut down the 7 C2 servers used to spread the malware in 6 different countries, and 1,500 domains used by Andromeda for C2 purposes were sinkholed under court orders.
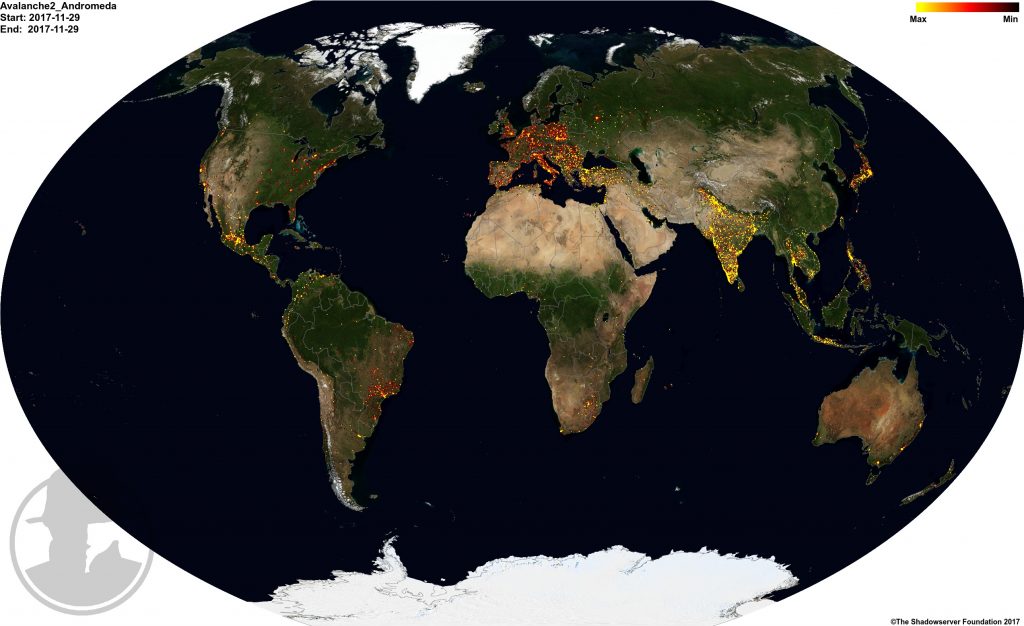
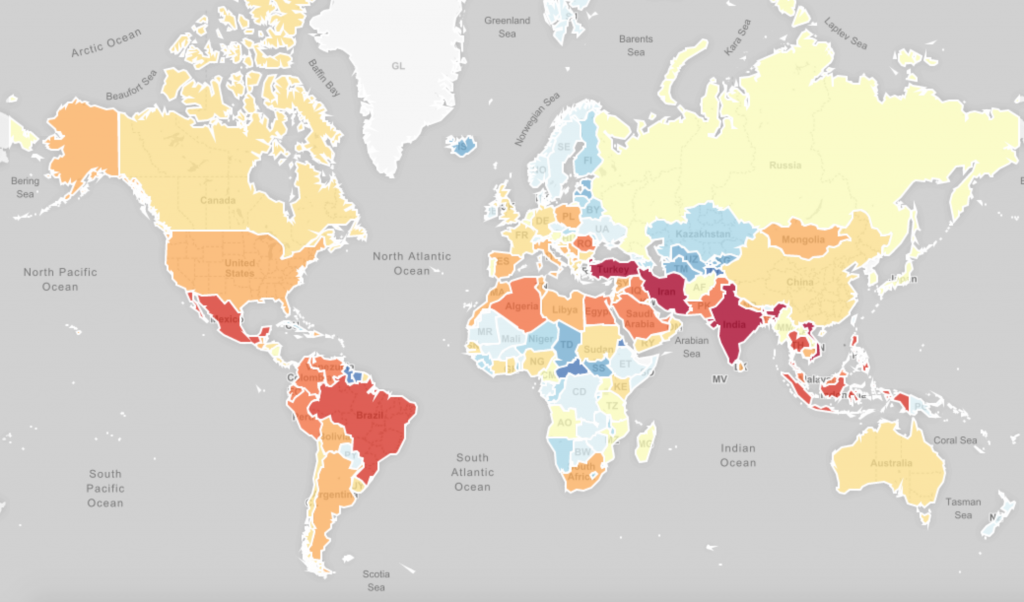
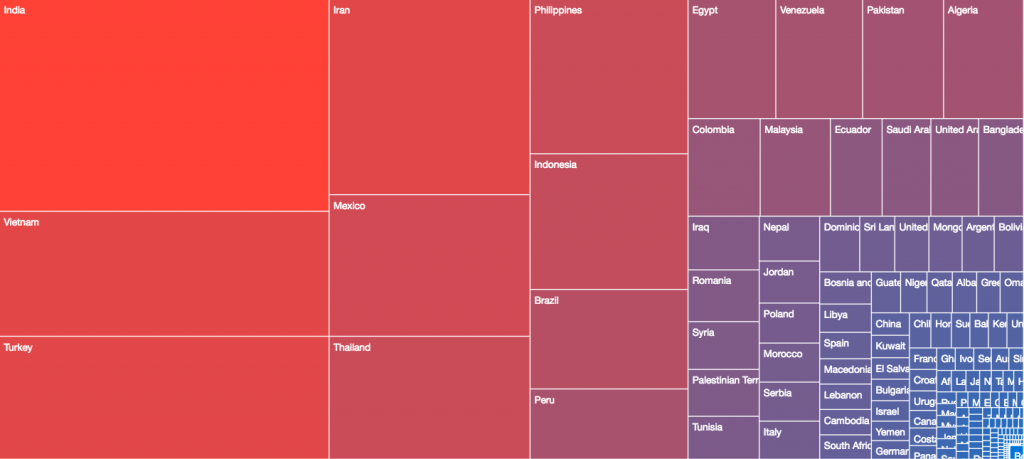
During the first 48 hours of sinkholing, approximately 2 million unique Andromeda victim IP addresses from 223 countries were observed connecting to the court-ordered sinkholes.
Initial victim distribution on November 29/30th:
Current live and daily historical statistics on Avalanche and Andromeda botnet victim distribution can be found on Shadowserver’s updated public reporting pages for Avalanche here and here.
Andromeda data from multiple sinkholes is tagged as “avalanche-andromeda” and “andromeda-b66“, and is already included in Shadowserver’s free of charge daily reports to national CERTs and network owners. If you do not already receive this data, you can sign up for them at no cost here.
The successfully extended and expanded sinkholing of the 21 malware families that made use of the Avalanche platform, and the associated takedown of the Andromeda botnet, is another great example of how complex international operations can successfully be jointly executed by a combination of cross-disciplinary public and private partners in the ongoing fight against cyber criminals globally. We are grateful to our strategic partner the Cyber Defence Alliance (CDA), who’s generous support continues to enable The Shadowserver Foundation to be able to provide free of charge services in the support to law enforcement around the world.