Attack on vulnerability in Ivanti Virtual Traffic Manager observed
Last week, a critical vulnerability in Ivanti’s Virtual Traffic Manager (vTM) became known. Now IT researchers have discovered an exploit attempt based on a publicly available proof-of-concept exploit. Admins should update the software quickly – updates are now available for all supported versions.
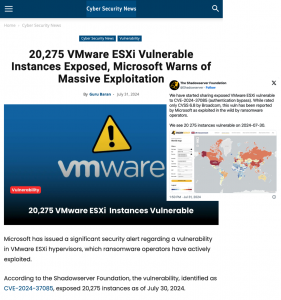
The Shadowserver Foundation has announced on X, formerly Twitter, that it has found very few Ivanti vTM devices openly accessible on the Internet. However, on Saturday last weekend, the group observed an attempt to abuse the vulnerability based on a publicly available proof-of-concept exploit.