Lessons from Oracle E-Business Suite Hack That Allegedly Compromises Nearly 30 Organizations Worldwide
A sophisticated cyberattack targeting Oracle E-Business Suite (EBS) customers has exposed critical vulnerabilities in enterprise resource planning systems, compromising an estimated 100 organizations worldwide between July and October 2025. The campaign, attributed to the notorious Clop ransomware group and linked to the financially motivated threat actor FIN11, exploited a zero-day vulnerability, CVE-2025-61882, to achieve unauthenticated remote code execution on internet-facing EBS portals.
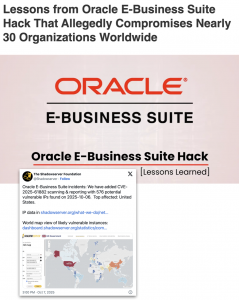
Shadowserver researchers released data on October 8, 2025, showing 576 potentially vulnerable IP addresses based on internet scanning for the zero-day vulnerability. This figure represents only internet-exposed Oracle EBS instances and does not account for organizations that may have been compromised but maintained the systems behind firewalls or other network security controls.