We can aggregate our reports by ASN, pointing our spotlight at all the malicious activity we’ve detected on a particular network.
Dashboard
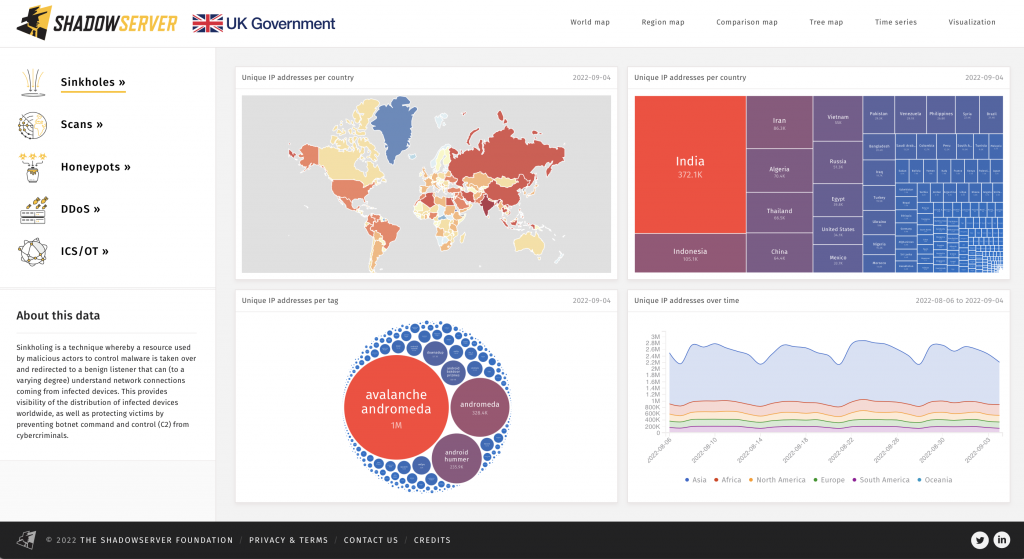
You can use the Shadowserver Dashboard to explore up to two years of aggregated country level data about many different types of cyber threat intelligence, including some data sets from Shadowserver’s unique vantage points. You can then visualize the data in various ways, which can be easily shared as URLs.
The statistics in the Shadowserver Dashboard are free to use (with attribution) for research, informing policy makers and by journalists/news media in educating the public about cyber security threats, but you are not permitted to scrape or resell the data. Please contact us if you have questions about licensing.
Curious to know more about the specific types of data we collect and the reporting we do? You can learn more below.
ASN
Bots
Bots are zombie computers controlled by cyber criminals. We find them using honeypots, honey clients, sinkholes, and tracking. Then we expose their activity in our reports.
Botnets
Botnets are multiple bots working together. Thanks to the scale of our infrastructure, we provide our partners with the resources to take them down.
DDoS
We use sinkholes to detect DDoS (distributed denial of service) attacks and bring them to our partners’ attention for remediation.
Geo Locations
We can precisely filter the activity in our reports by longitude and latitude, giving national governments the information they need to protect their region.
Malware
We have a massive, constantly growing repository of malware samples. We never throw anything away, so we can easily revisit historical data to catch anything we might have missed.
Scans
Shadowserver scans the entire IPv4 Internet 42 times every day. Then we package the data we collect in our reports, which are aggregated per subscriber on a need-to-know basis.
URLs
We collect potentially infected URLs from attacks, honeypots, sandbox runs, and spam, helping us trace malicious activity to its source.